Find more evidence on an endpoint with the latest Cyber Triage release. Last week’s 1.6.0 release expands on Cyber Triage’s thoroughness and ease of use. We’ll talk about two new analysis techniques in this post: collecting all file metadata and detecting fast flux domains. Both of these allow any company to perform a more in-depth triage than you’d get with ad-hoc approaches.
It’s All About the Metadata
When using the latest Cyber Triage, you’ll be able to find more indicators of compromise (IOCs) because blacklist rules are now applied to all files on the target system. This allows you to better use threat intelligence to triage systems.
Cyber Triage has always collected content and metadata about files that were referenced in the registry, startup folders, and scheduled tasks. Now, it collects metadata (name, times, size, etc.) about all files as it scans the file system looking for suspicious files.
What this means for you is that if you have threat intelligence about a suspicious path, such as “C:TempBadStuff” and you add that path as a blacklist item, then Cyber Triage will always flag it. When you get updated intelligence about paths, then you can search previous collections for them because the collected data is always stored in the backend database.

The Cyber Triage collection tool uses The Sleuth Kit to analyze file systems and therefore we can pull all 8 NTFS timestamps and not modify the access times as we traverse the file system. In a future release, we’ll use these time stamps to make timelines so that you have context about what happened before and after each threat.
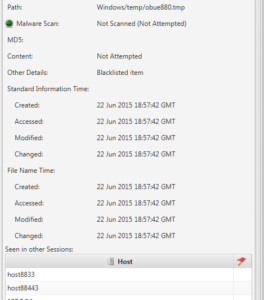
Another use of this additional metadata is to help a responder know what normal is. Cyber Triage uses the backend database to show you what other hosts have the same file, which helps the responder know how rare or common a file is in the enterprise.
Fast Flux Domains
To avoid detection, malware and malicious programs use a technique called fast flux to quickly change what IP address a domain name maps to when they reach out to their command and control servers. This approach makes it more difficult for companies to block known bad IP addresses at the network level.
When investigating an endpoint, you want to look for dynamic domains that the endpoint connected to because it could be a sign that malware is on the host. You’d find references to these domains in the DNS cache or maybe web browser history. The problem is that there are 10s of thousands of dynamic DNS domains. FreeDNS, for example, has over 86,000 domains that a user can pick from.
Cyber Triage now identifies the dynamic domains for you when it displays the hostnames found from DNS cache, active connections, registry, and event log. This makes it easier for you to quickly identify if the endpoint was connecting to a dynamic DNS domain.
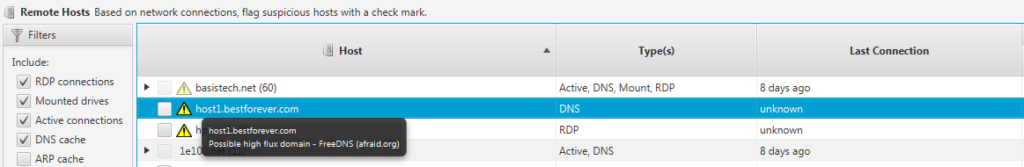
Cyber Triage identifies the dynamic domains based on name servers. For example, all of the 86,000 domains from FreeDNS use NS1.AFRAID.ORG as their name server. Cyber Triage comes with a list of common dynamic DNS providers and users can add their own services to it
More is Better
To properly triage an endpoint, you need to quickly look in the places where evidence could be. The latest Cyber Triage release lets you look at more places for evidence while not taking more time. Contact us to get a Cyber Triage demo and free evaluation copy.




