Artifact Collection
There is simply no faster or easier way to collect important artifacts (before they can be hidden or erased) than with Cyber Triage.
This tool can also be used to conduct on-premises or cloud forensics – you can use Cyber Triage with AWS, GCP and Azure for cloud investigations.
This tool runs on all versions of Microsoft Windows (XP and newer), analyzes disk images in raw or E01 formats, utilizes The Sleuth Kit®, and is contained in a single executable file, making it very easy to deploy.
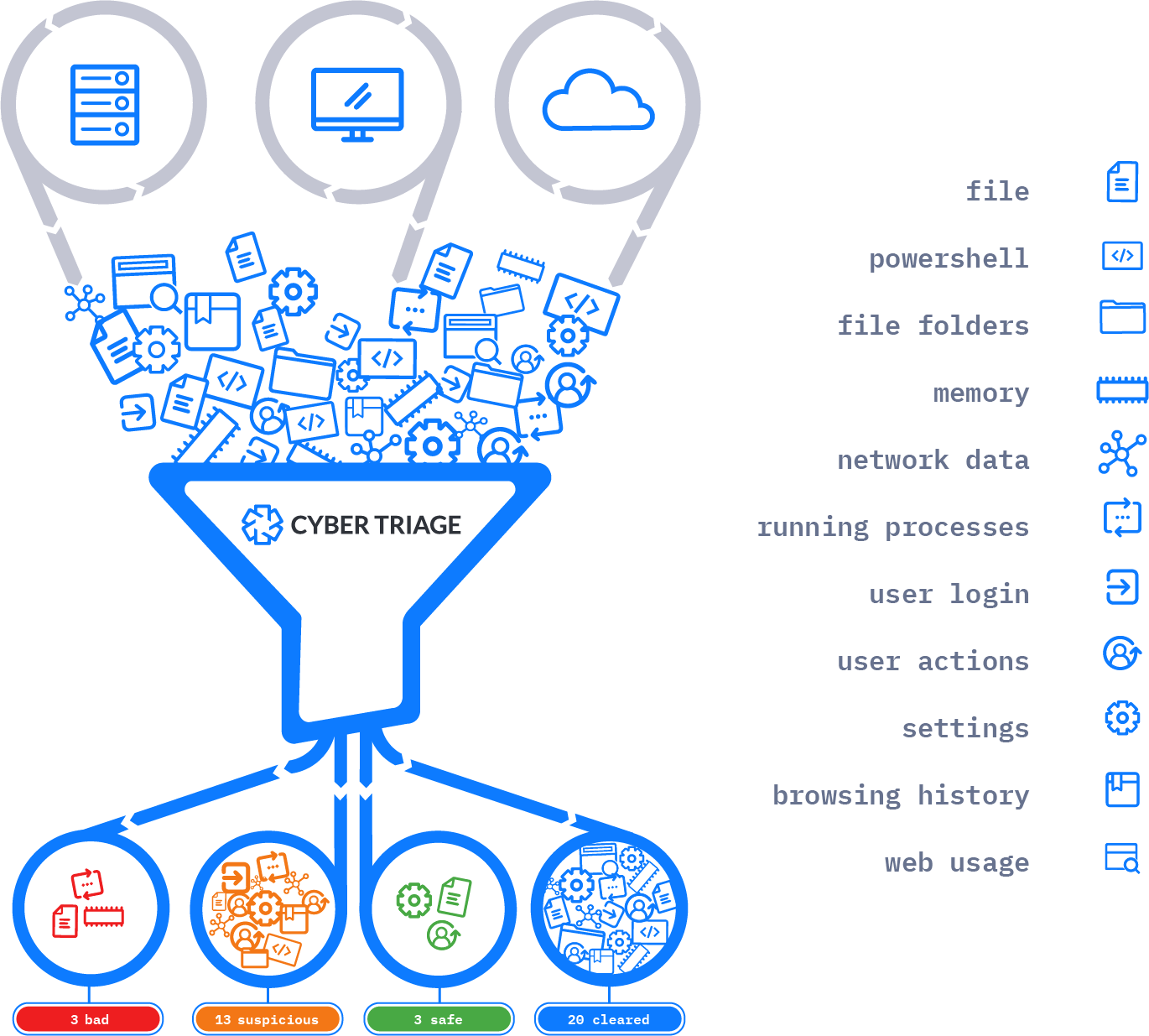
You can collect all of the following:
- Volatile data (including running processes, open ports, logged-in users, active network connections, and DNS cache)
- Malware persistence mechanisms, including startup items and scheduled tasks
- User activity, including what programs they ran, web activity, and logins
- Metadata from all files on the system
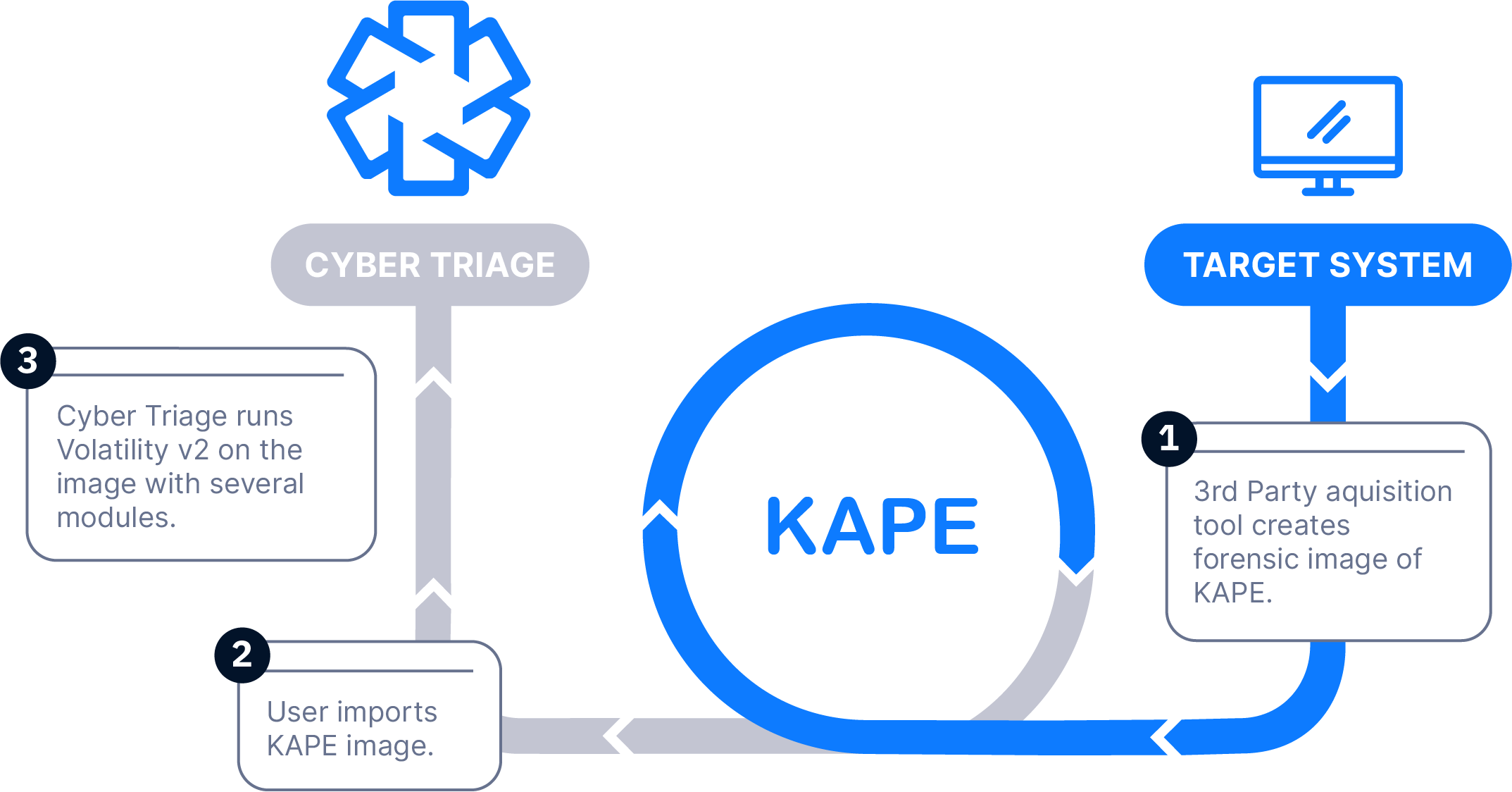
Supported Collection Scenarios
The Collector is copied to the target system via PsExec, launched, and artifacts are sent back over the network. A list of hosts can be queued.
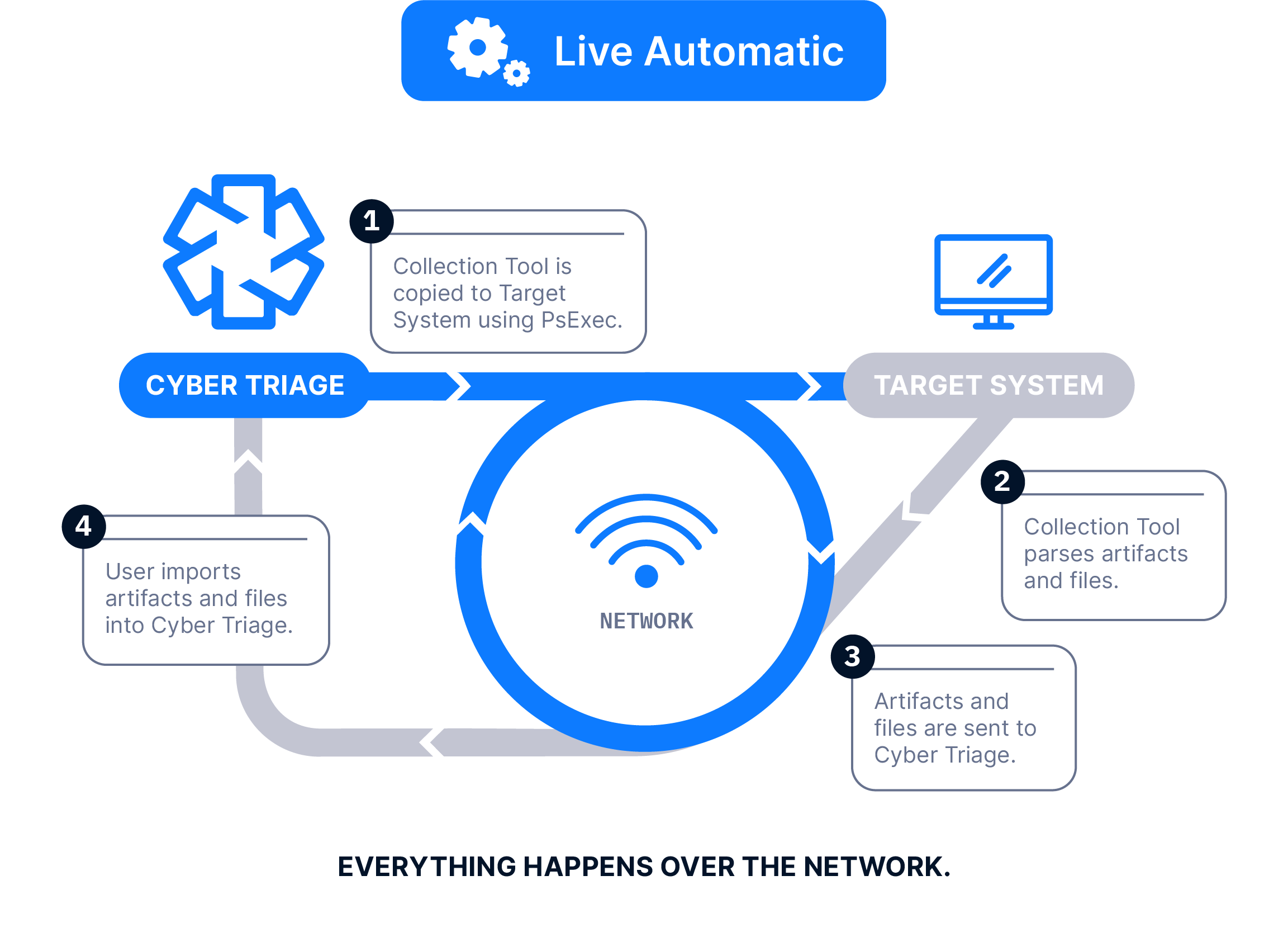
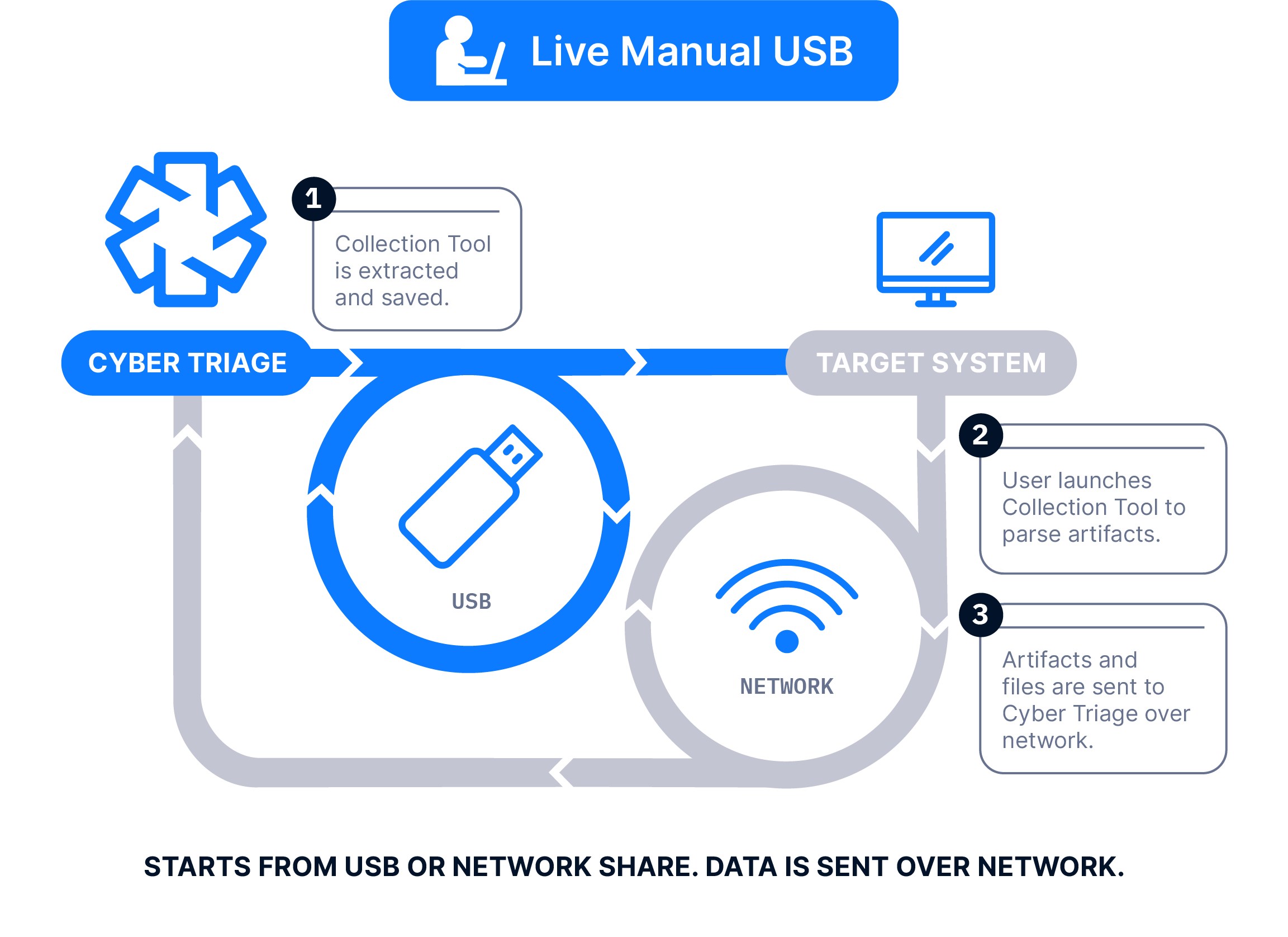
The Collector is copied to a USB drive, it’s manually run on the target system, and artifacts are saved back to the USB. The data is then manually imported into Cyber Triage. Files can be imported in batches using a Standard Pro or Team license.
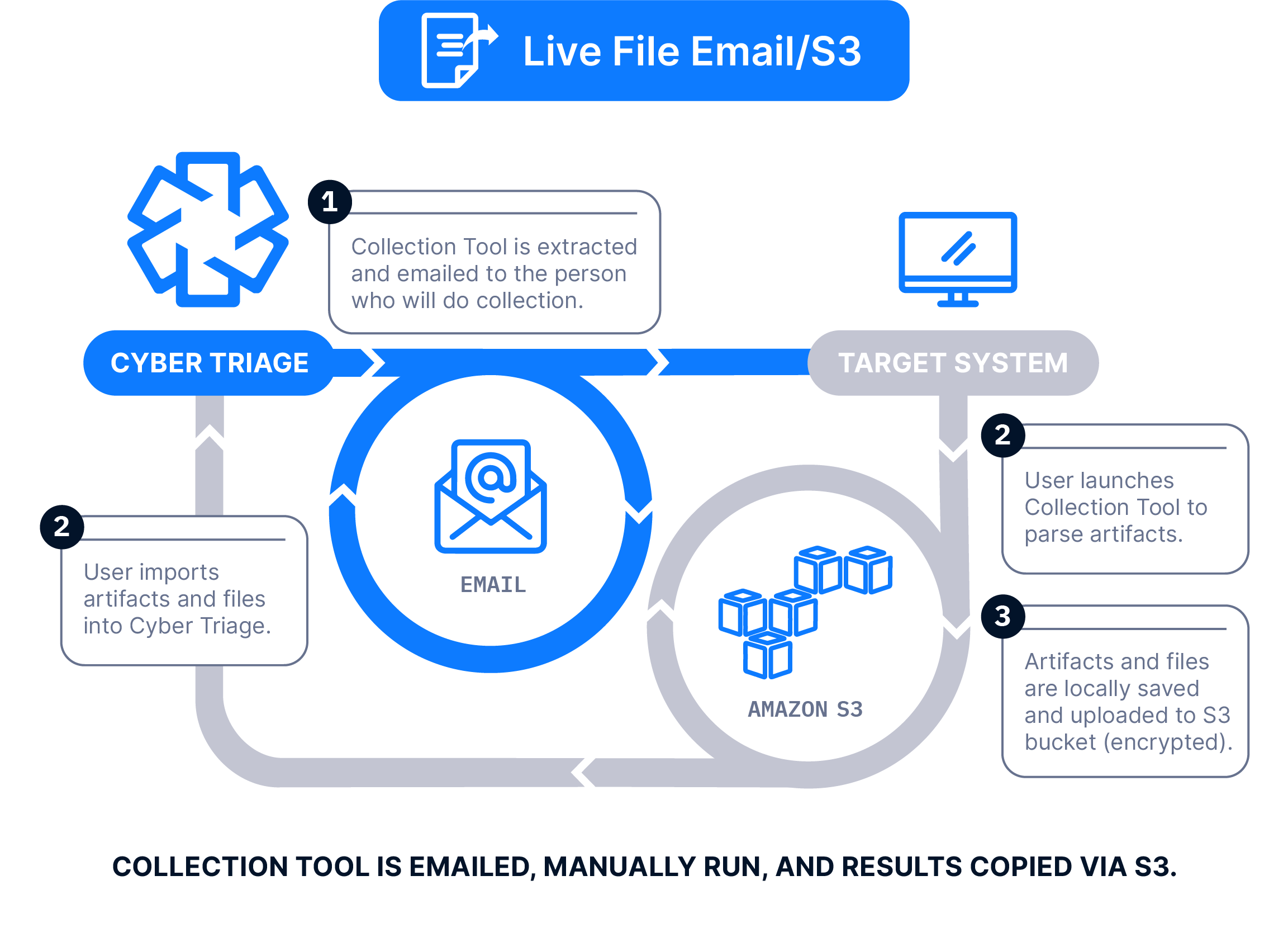
The Collector is emailed to a client or local IT member, they run it on the target system, and artifacts are uploaded to an S3 bucket. The data is then manually imported into Cyber Triage.
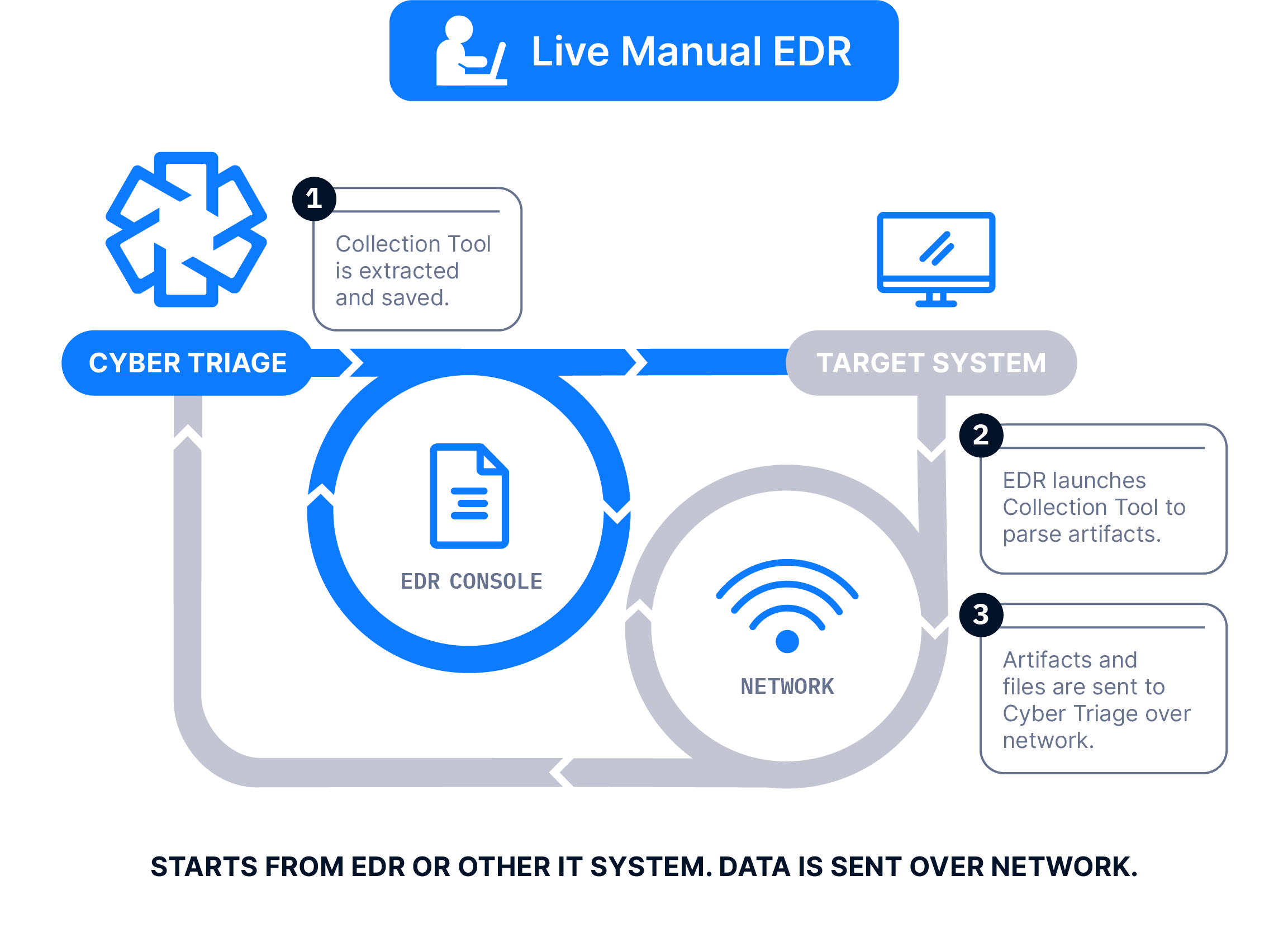
The Collector is launched on target computers using an EDR or SOAR. The results are then sent to a waiting Cyber Triage server to be immediately analyzed. This requires a Team license.
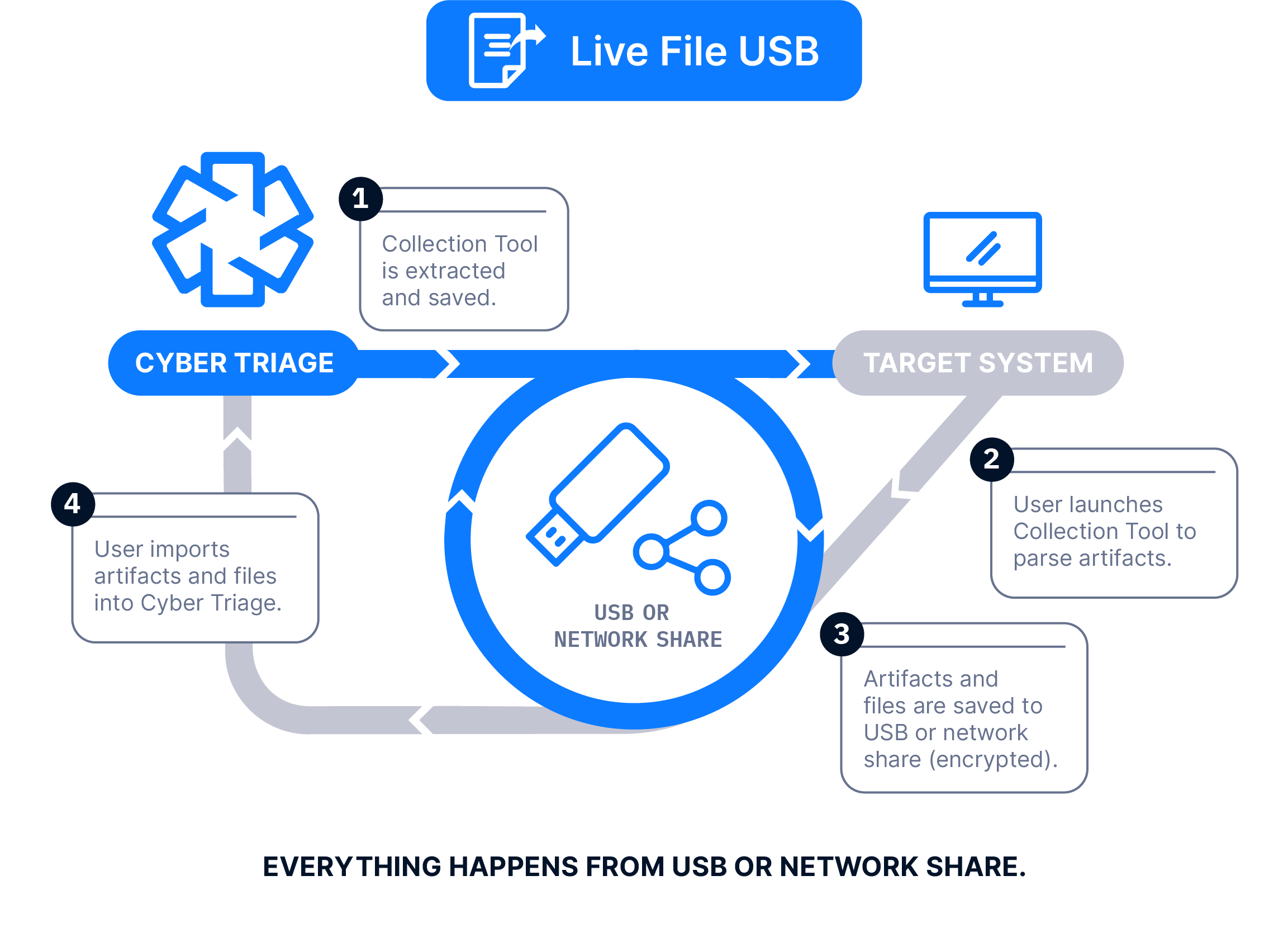
The Collector is copied to a USB drive, it’s manually run on the target system, and artifacts are sent back over the network.





This tool features:
- Malware scanning from 40+ engines
- Yara to integrate cutting-edge rules
- Heuristics that experienced responders look for, such as anomalous processes
- Import IOC threat intelligence lists
Prioritization and Scoring
You can’t afford to waste time on unimportant artifacts during a high-pressure intrusion investigation. This tool eliminates that risk by automatically scoring all of the collected artifacts and providing valuable context about them.
For example:
- Timelines show what happened before and after a given event
- File Explorer uncovers what files are stored alongside malware and other suspicious files
- You can easily pivot data types to learn about related artifacts, such as a network connection associated with a file
- Artifacts are categorized as: bad items, suspicious items, and good items.
Recommendation Engine
Ensure the thoroughness of an intrusion investigation with this beneficial tool. As you review prioritized items, this tool finds additional suspicious evidence for you to check out.
It can be easy in intrusion investigation to become “overwhelmed” with data due to the thousands of artifacts that are generated during malware and account takeovers. While you review the scored data produced by the Collector, the Recommendation Tool will display all related items to you, and you’ll be reminded to take a look at any of the related items that were marked suspicious.
With this tool you can:
- Use results to quickly resolve the current investigation and make future ones more efficient
- Team version allows team members to collaborate on the same incident and share results
- Generate HTML or JSON reports of each host or incident to share results and include in reports
Collaboration Capabilities
Another common issue that can delay intrusion investigations and decrease their comprehensiveness and efficiency is a lack of easy collaboration.
The team version of this tool makes sure you and your staff can collaborate at every step of the investigation.
Increasing investigation efficiency and convenience even more, REST APIs allow other enterprise tools to query for artifacts and indicators and results can be used to prioritize items in future incidents.
Ransomware Investigation
Ransomware is becoming an increasingly common way for criminals to exploit companies. In addition to deciding if you should pay the ransom, you also need to know how the attacker initially got in and what other persistence mechanisms they installed. Otherwise, you are likely to find yourself in a similar situation in the future.
This tool is focused on making it easier for you to work back from the start of the encryption process to how the ransomware was launched and how the attacker got in.
Ensure you focus on the most relevant artifacts first during your ransomware investigations with this valuable tool.
You get:
- Ransomware note detection using statistical techniques and threat intelligence
- Encrypted database detection – this tool detects important files that are encrypted and makes you aware of them
- Plus, the tool detects lateral movement between systems, persistence mechanisms and backdoors and the launching of reconnaissance and malicious programs
Everything You Need to Conduct Thorough & Accurate Investigations
Use the complete Cyber Triage Toolkit to quickly and correctly diagnose an intrusion, explain what happened and why, and to make sure it doesn’t happen again.
Being able to respond quickly to an intrusion and conduct a fast, accurate investigation will limit damage and make everyone breathe a little easier in what can be a very difficult situation.