Cyber Triage Finds Malware Using 40+ Scanning Engines from ReversingLabs.
Malware is used at some point in nearly every intrusion. It enables the attacker to obtain passwords, maintain a foothold, or encrypt data.
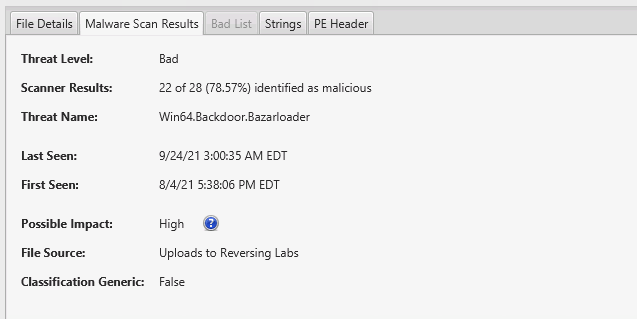
Cyber Triage finds malware using 40+ scanning engines from ReversingLabs. Because no single detection tool is perfect, using over 40 gives you a broad set of opinions on if a file is good or bad.
You can also locally apply Yara rules and upload to the Recorded Future sandbox.
Scan Every Executable
The Cyber Triage malware forensics tool will copy many executable and library files from the investigated host. This includes files associated with running processes, startup items, and previously launched programs.
You have control over how that data is analyzed. For example, you can lookup detection results based on the file’s signature (hash) if someone already uploaded the file and results already exist, or you can upload the file contents and let the engines analyze them.
Privacy Protection
Many responders have heard horror stories of uploading malware to public service and revealing an attack to the world.
The Cyber Triage service is different:
- When files are uploaded, they are sent to a private repository. The general public cannot see the results. Only fellow Cyber Triage customers who query for the same hash value.
- Only PE format executable and library files are uploaded. PDF and Office documents are not. This limits PII risk.
You control how the service is used. Even with the above safeguards, you can choose to never upload files. In fact, we make special licenses that prevent uploads if that makes you feel safer.
Offline Mode
Some DFIR labs are air-gapped and cannot directly query the online service. To service those labs:
![]()
Cyber Triage will export a list of hash values from the collected host to a text file.
![]()
The investigator will copy the text file to an Internet-facing computer and upload the hashes to a website.
![]()
The investigator will get a text file response and copy that back into Cyber Triage.
Extensible Limits
Cyber Triage licenses come with daily or weekly limit on files that can be analyzed. But, you can purchase boost codes for big incidents when you need extra capacity.
To ensure you can complete as many investigations as needed, there are three levels of limits:
- Base: The core limits that come with your license, such as 4,000 lookups per day for Standard Pro.
- Flex: Extra lookups that you can use to finish a host if you run out of base. Each license comes with 1000 flex lookups per month.
- Boost: Additional lookups that you can purchase with a credit card.
The User Guide has more details on the limits and how they are used.