Ransomware is Everywhere
Ransomware is becoming an increasingly common way for criminals to exploit companies. In addition to deciding if you should pay the ransom, you also need to know how the attacker initially got in and what other persistence mechanisms they installed. Otherwise, they’ll just keep coming back.
Cyber Triage focuses on making it easier for you to work back from the start of the encryption process to how the ransomware was launched and how the attacker got in. After all, a ransomware attack is like most other attacks, except the final step is to encrypt the data instead of only stealing it.
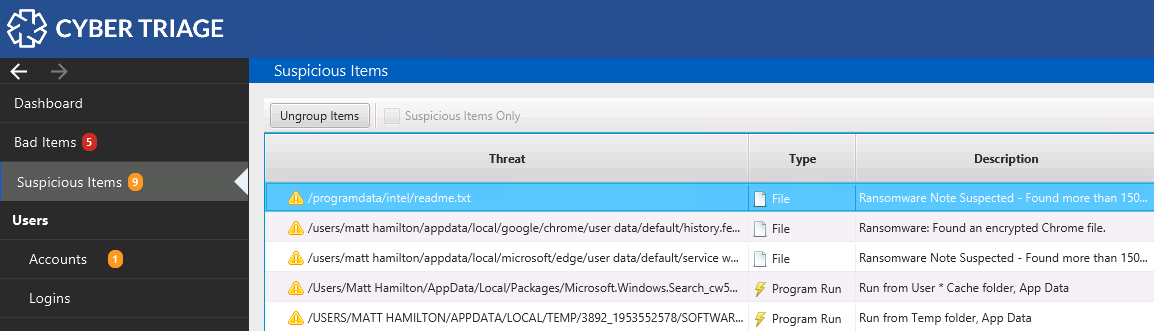
Ransom Note Detection
Cyber Triage detects ransomware notes using statistical techniques and threat intelligence. It flags the first and last notes to give you a range of when the encryption was being performed. The statistical techniques allow you to identify notes that have not been seen before or that have very common names (such as “README.TXT”).
Once you see the first note, you can work back to see what activity happened before that.
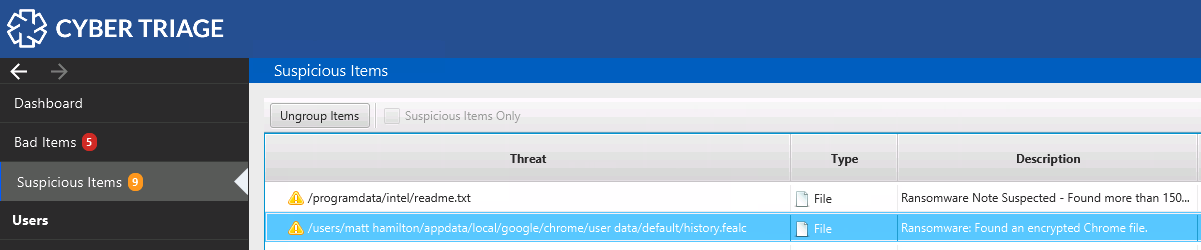
Encrypted Database Detection
Cyber Triage detects important files that are encrypted and makes you aware of them. For example, if web browser databases are encrypted.
This allows you to have a better understanding of why you are not seeing certain types of artifacts. The evidence of the attack may be inside of the encrypted files.
Plus the Standard Features
The other Cyber Triage features are also used during a ransomware investigation to make sure you can detect:
- Lateral movement between systems
- Persistence mechanisms and backdoors
- Launching of reconnaissance and malicious programs
Cyber Triage’s scoring capabilities ensures that you can focus on the most relevant artifacts first during your ransomware investigations.
- For more details, including a complete list of ransomware investigation capabilities , contact us.