SPEED UP EVERY CYBER INVESTIGATION
Go from alert to report in 1/2 the time with one investigation platform for SOC and IR
Trusted by
Manual Investigations are Slow
SOC analysts can’t investigate endpoints without hours of scouring EDR data. DFIR teams can’t find root cause without days of digging with forensics tools.
The result is damaging delays, skipped steps, and persistent threats.
Automated Investigations are Fast
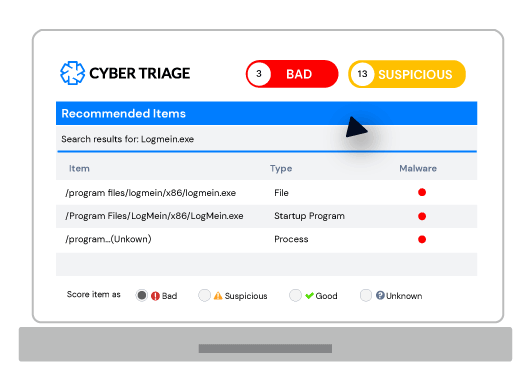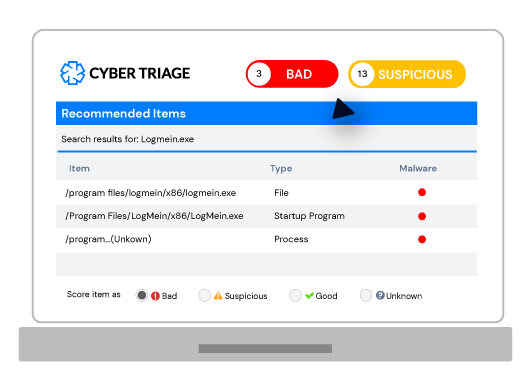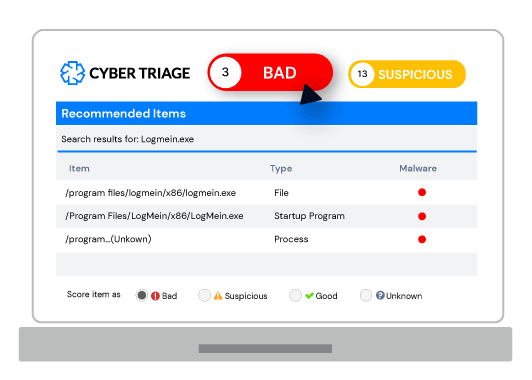
Cyber Triage is an automated investigation platform that empowers your team to investigate quickly.
- Scores artifacts so you quickly focus on relevant data.
- Scans executables with 40+ malware detection engines.
- Recommends artifacts so you follow up on all leads.
- Integrates with EDRs for rapid endpoint triage after alerts.
- Collects evidence even when EDR evasion is used.
- Deploys in environments agents can’t be used.
Investigate fast with Cyber Triage.
INVESTIGATE IN MINUTES
Automation means faster decisions.
- Find
- Evidence ASAP with EDR and SOAR integrated collection.
- Relevant artifacts immediately with automated analysis.
- Every lead fast with artifact recommendation.
RESPOND WITH CONFIDENCE
Automation means comprehensive investigations.
- Comprehensive
- Collection that covers all relevant artifact + attack scenarios.
- Analysis that scours millions of records for clues.
- Automation that ensures the basics are airtight.
SCALE WITHOUT COMPROMISE
Automation means empowered teams.
- Maximize
- Productivity of understaffed teams with automated analysis.
- Impact of jr. responders with a UI built for all experience levels.
- Teamwork with shared findings and collaborative investigations.
- Flexibility with deployments on laptop, cloud, or on-prem server.
Cyber Triage in Your Workflow
Cyber Triage is simple for IR teams to deploy and use.
Agentless collection tool collects data and sends artifacts over the network, to USB, or S3.
Step01
Data artifacts are normalized into information artifacts, simplifying the investigation.
Step02

Automated analysis finds bad and suspicious items and highlights them for review.
Step03

As the responder reviews, similar items are automatically found and recommended.
Step04

Easily generate human and machine readable reports with the findings.
Step05
Easily speed up your investigations with Cyber Triage.
Cyber Triage in Your Workflow
Cyber Triage integrates directly into EDRs.

EDR generates an alert.
Step01
Launch Cyber Triage PowerShell script.
Step02
Data is collected and sent to Cyber Triage.
Step03
Cyber Triage prioritizes bad + suspicious items.
Step04
Analyst determines best response.
Step05
Turn your EDR into an end-to-end investigation platform with Cyber Triage.
Learn DFIR Free with Brian Carrier
Intrusion investigations are amongst the most difficult for digital forensic investigators because there are so many types of evidence to look for. Our Divide and Conquer DFIR Process helps investigators answer these hard questions by breaking them into smaller questions.
Built by Forensics Veterans

Cyber Triage is built by Sleuth Kit Labs, a spinout of BasisTech. This is the same team responsible for 20+ years of open source tools, including Autopsy and The Sleuth Kit (TSK). Sleuth Kit Labs believes in making the jobs of those on the front lines easier by making software that is automated and easy to use. The company understands that it can’t decrease first responders’ responsibilities, but it can make digital forensics as easy and effective as possible.
Get Cyber Triage
Try Cyber Triage to see how it will make your intrusion investigations faster and more comprehensive. Fill out this form to get an installer. Get started with our scenario data (or your own).
Download your free 7-day evaluation
with scenario data