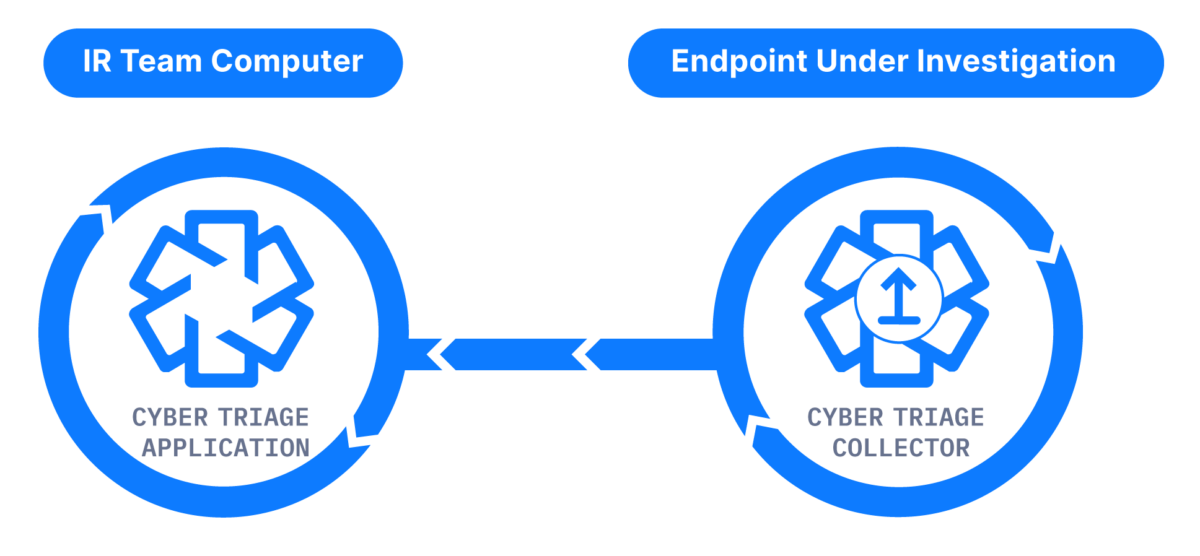
Cyber Triage’s Collector tool ensures you get as many artifacts as possible to identify attacker activity.
While Cyber Triage can import data from other collection tools, you’ll benefit from using its Collector because:
- It collects the most amount of relevant data, especially scripts and executable content
- It’s easy to deploy because it’s a single executable file
- It’s rules can be customized
- It can upload to encrypted data to cloud storage or directly to a Cyber Triage server
The Collector is a separate application that can communicate with the main Cyber Triage application.
Adaptive Collections Get All The Artifacts
Cyber Triage performs an adaptive collection, which means it does more than just copy a static list of files. It also parses them and recursively copies any other file or identifier that is found, such as executables or documents.
This unique approach allows you to get copies of the scripts and executables that run on the system and then determine if they are malicious. With other tools, you are guessing. They are static and collect only the files that were configured to collect.
As an example, a common attacker technique is to create a registry entry to launch their malware each time the computer starts. With a traditional, static collection tool, the registry will be collected and you can later see the following file is run:
C:\windows\temp\update.lnk
But, you won’t know if that file is good or bad because you don’t have a copy of it. You won’t know that the ‘update.lnk’ file will also load the malicious “C:\windows\temp\update.dll” file when it is run.
But, the adaptive collection approach with the Cyber Triage Collector will get all of these files because it parses the LNK file and also collects the DLL.
| Static Standard Collection | Adaptive Cyber Triage Collection |
|
|
With these additional files, Cyber Triage will be able to detect that ‘update.dll’ is malicious with its malware scanning service.
Cyber Triage’s adaptive collection approach ensures that you get as many relevant artifacts as possible so that you can make better decisions.
Artifacts Collected
The artifacts that the Cyber Triage Collector copies include:
Process-Related
|
User-Related
|
Operating System Settings
|
File Content
|
If you would like a full list of artifacts that we collect, contact us.
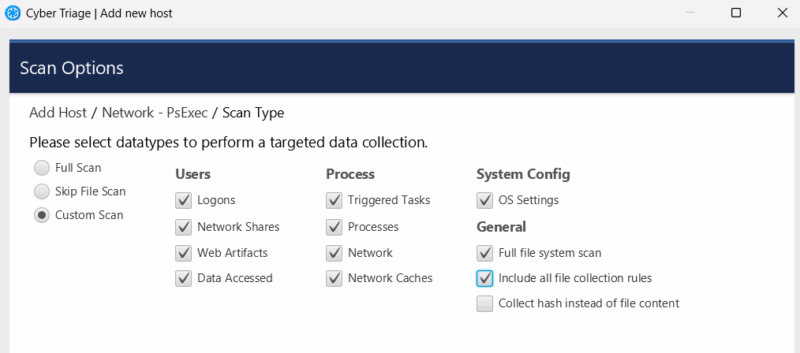
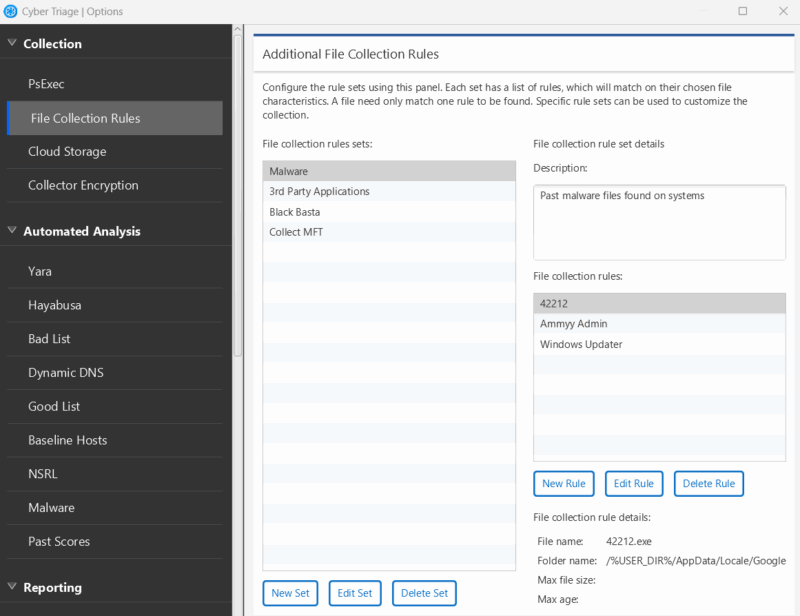
Customized Rules
You can configure the Collector to make copies of specific files. This is useful when you want to always collect a specific application log or look for an indicator of compromise (IOC).
Rules can include:
- Full or partial paths
- Wildcards
- Size limits
- Date ranges
For example, you can collect all files with a certain extension that were created within the past 30 days.
These rules can be configured in the Cyber Triage UI.
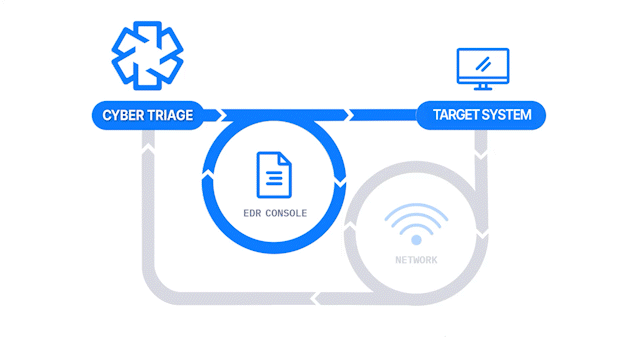
Save Results to a File, Server, or Cloud
|
The output of the Collector is a compressed JSON file that can be optionally encrypted. The data can be sent:
See the Collection page for all of the supported scenarios. |
 |
Once the JSON file has been imported into Cyber Triage, you can view and export the data. More details on the collection scenarios can be found here.
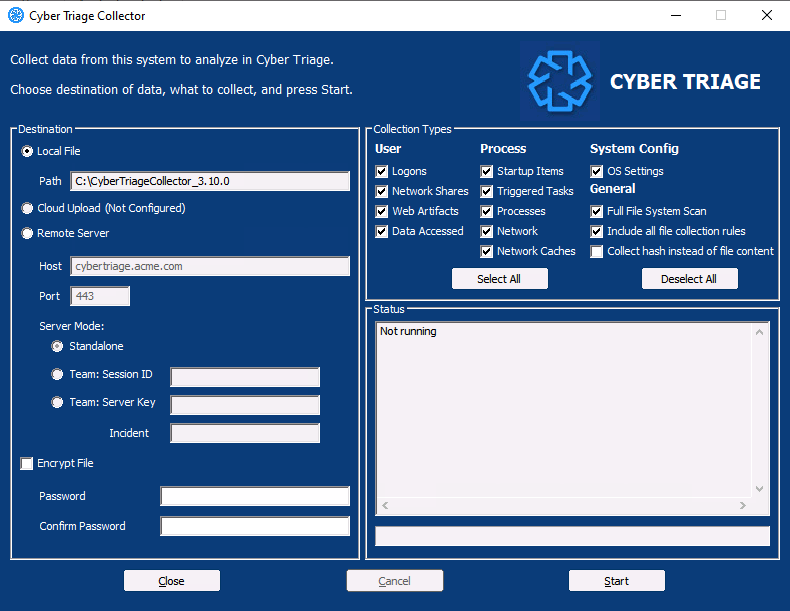
Run as a UI or Command Line
The Collector itself is a command line tool, which makes it easy to automate and for experts to run. You can integrate it with EDRs using the Deployer script.
But, sometimes you want to send it to a client and not make them type in commands. The Collector comes with a UI wrapper that allows a user to select checkboxes instead of typing arguments.
Built As a Forensic Tool
| The Collector is built on the popular Sleuth Kit® open source library, which was created by Sleuth Kit Lab CEO Brian Carrier. It is used in Autopsy and dozens of other forensics tools. Use of this industry-standard library allows the Collector to bypass rootkits and access locked files. |  |
System Requirements
The Cyber Triage Collector requires:
- Microsoft Windows XP or later
- Administrator credentials
More details and command line arguments can be found in the user manual.
Getting the Cyber Triage Collector
The Collector comes with all versions of Cyber Triage (Team, Standard, and Lite). You can extract it from the main UI.
Try out Cyber Triage today to get access to the Collector and make sure you quickly get all of the data you need.