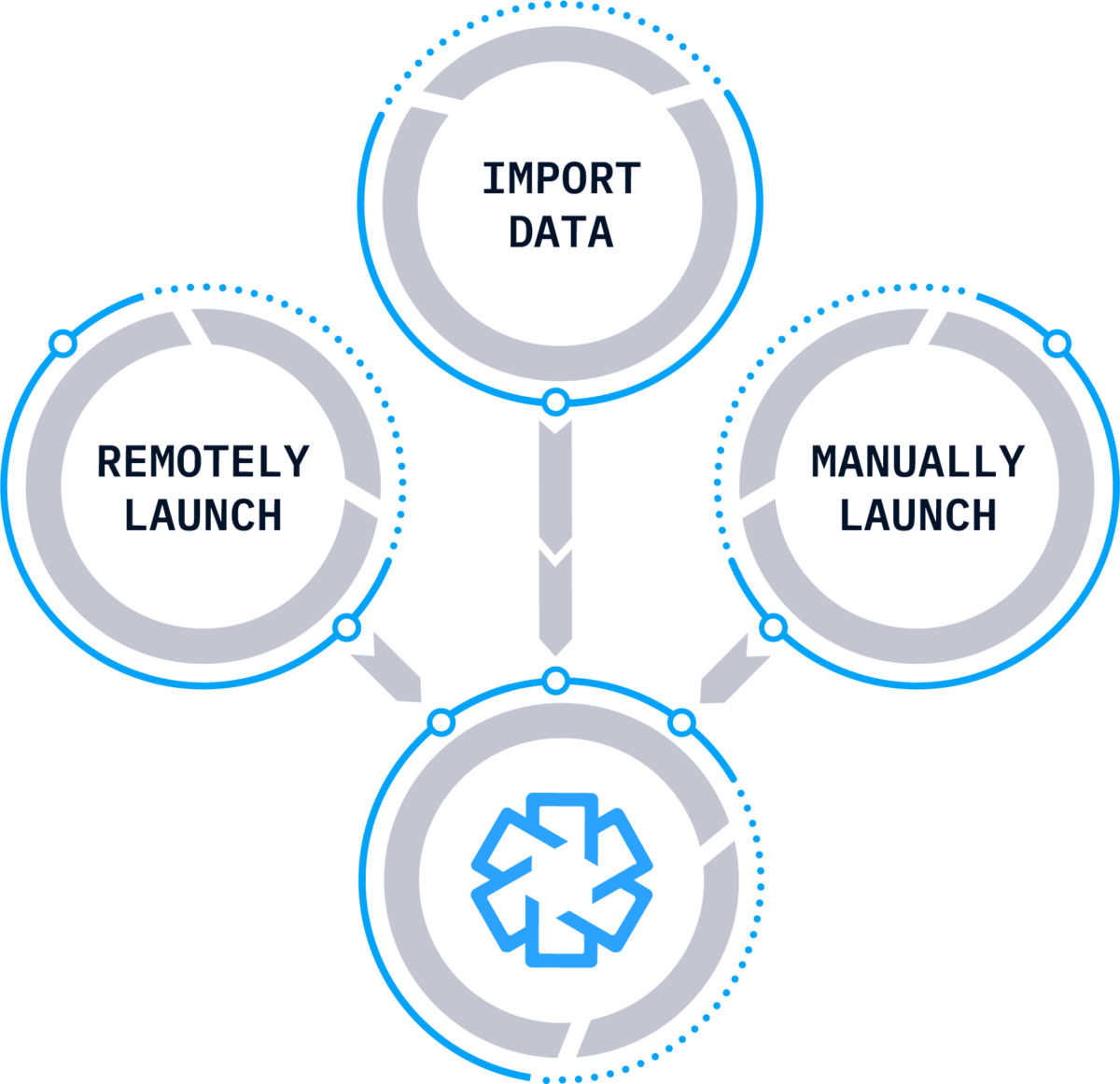
Import All Your Investigation Data
It’s critical that you are able to collect and analyze data from any system during your investigation. Cyber Triage can import data from other collection tools and its Collector has unique features to ensure you get as much data as possible.
Cyber Triage will get the data you need, regardless of the incident. It can:
- Collect from live systems
- Import data from other collection tools
- Import disk or memory images
Collect From Live Hosts
The Cyber Triage Collector can run on a live host and copy only the needed artifacts. It has unique recursive features that enable it to collect more file content than other collection tools. It will parse registry files, LNK files, and other file types so that it collects as many executable files as possible. This means you’ll be able to more accurately identify malicious files. Other collectors will copy only source files, such as event logs and registry hives.
The Cyber Triage Collector works on live systems in a variety of situations. It can be:
- Remotely launched using PsExec, an EDR, or other IT infrastructure.
- Manually launched and results saved to USB, server, or S3 bucket.
- Emailed to clients and remote offices.
- Launched by a SOAR or SIEM. See the “Integrations” for more details.
See the Deployment Scenarios section below for details.
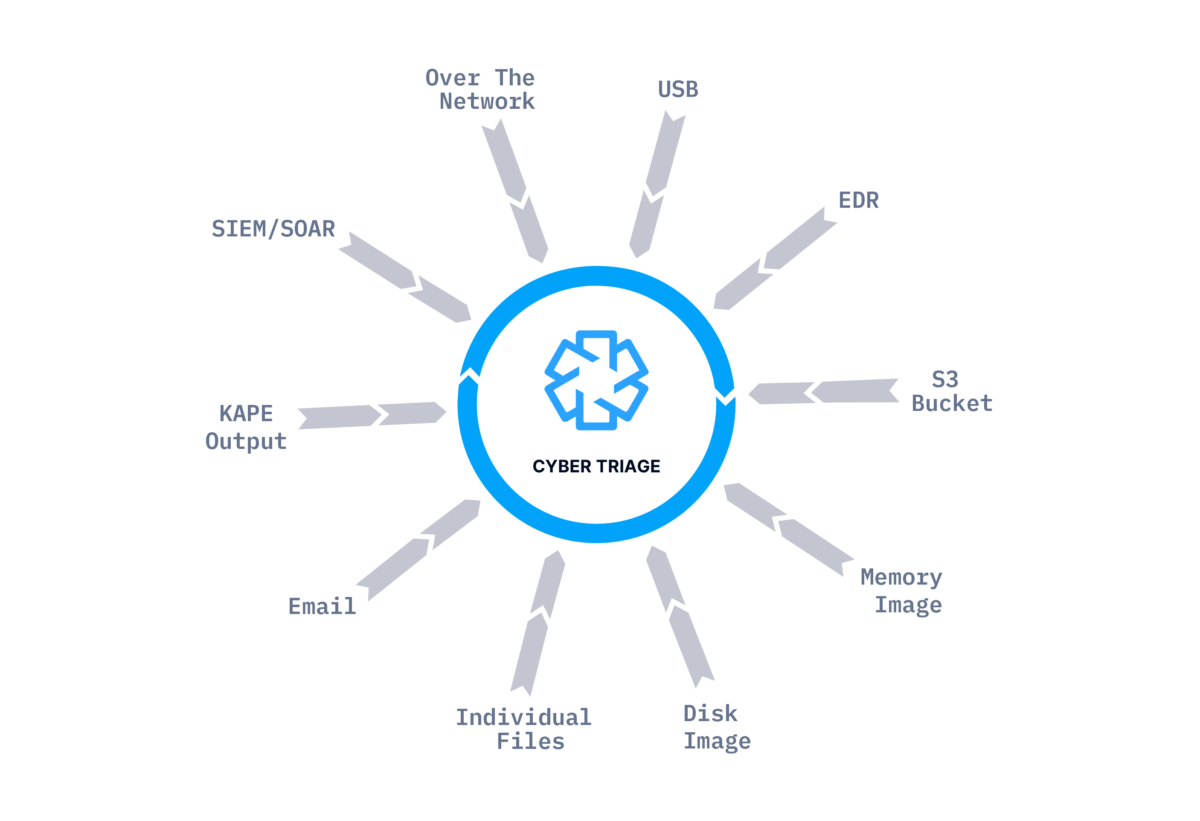
Import From Other Tools
In some situations, someone else acquired data from the system, and you’re tasked to analyze it. Cyber Triage can import images and outputs of other tools so that you can take advantage of Cyber Triage’s scoring infrastructure.
- Disk images are analyzed, and file system-based artifacts are extracted.
- Memory images are analyzed using Volatility v2.
- KAPE VHD files are analyzed, and artifacts are extracted.
See the “Deployment Scenarios” section below for more details.
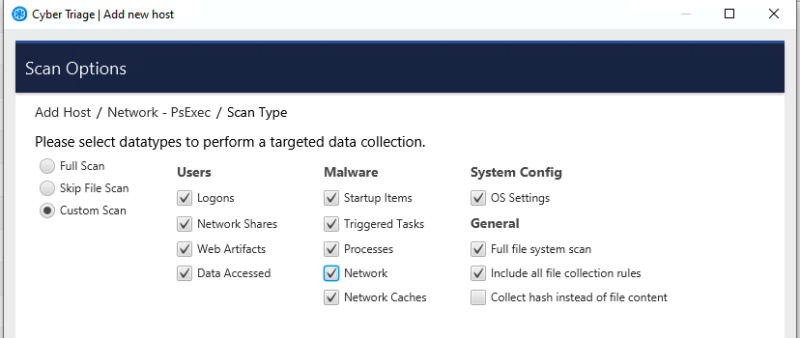
Types of Data Collected
Instead of making a full image, the Cyber Triage Collector focuses on the types of artifacts that are likely associated with an intrusion. This includes:
- Volatile data that may indicate malware, such as running processes, open ports, and active network connections
- Malware persistence mechanisms, including startup items and scheduled tasks
- User activity, including what programs they ran, web activity, and logins, which can be used to detect account take over.
- File metadata from all files on the system.
- For a complete list of collected artifacts, contact us.
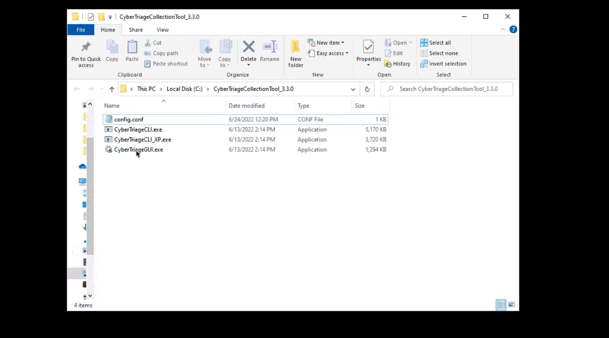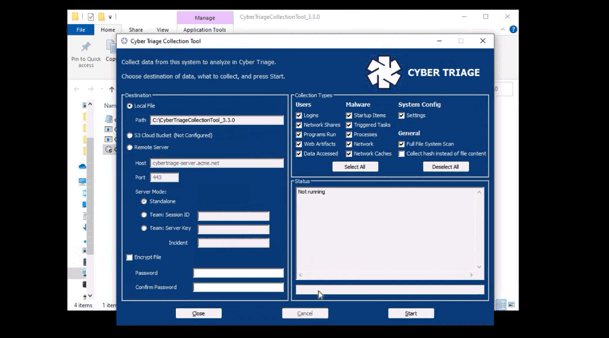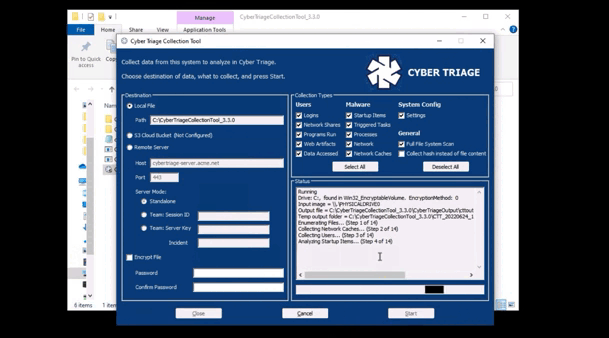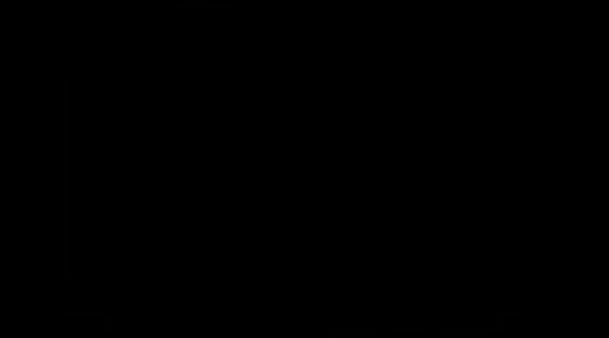
The responder can configure what is collected from each system.
Cyber Triage Collector Details
- It runs on all versions of Microsoft Windows (XP SP3 and newer)
- A single executable that requires no installation on target systems or dependencies, such as .Net.
- It can be launched from our GUI wrapper or a command prompt.
- Uses The Sleuth Kit® forensics library, making the process less vulnerable to typical rootkits and not modifying file access times.
Over the Network Scenarios
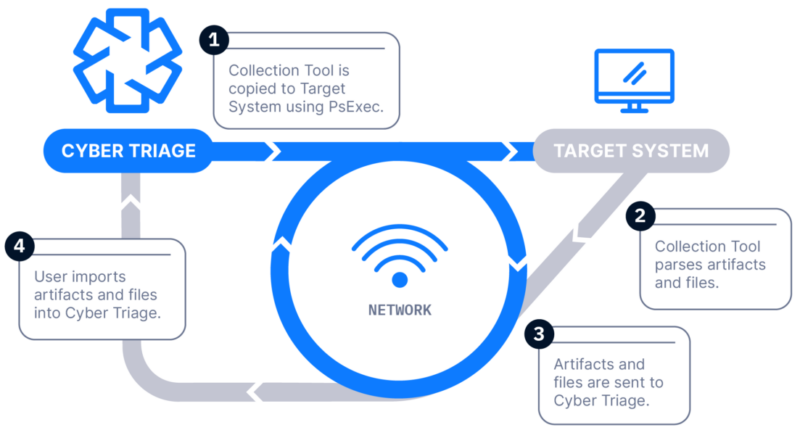
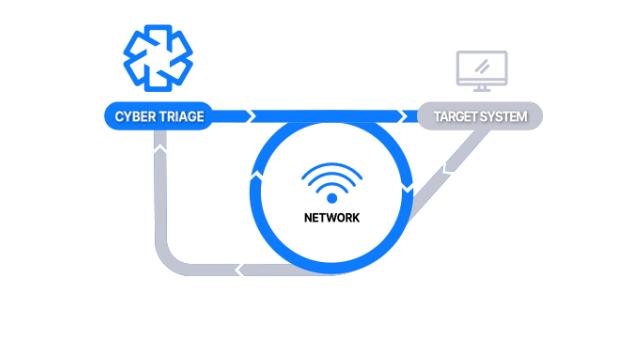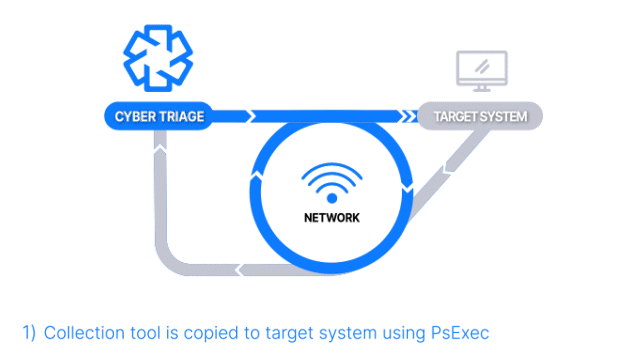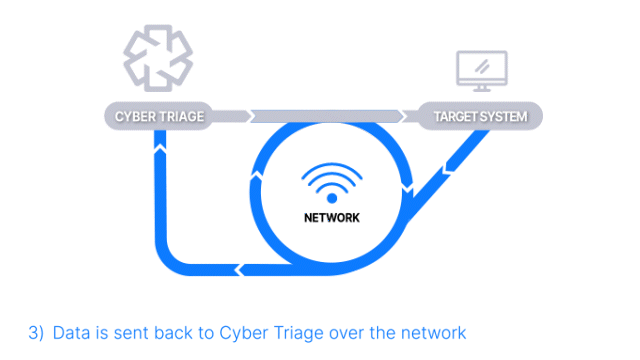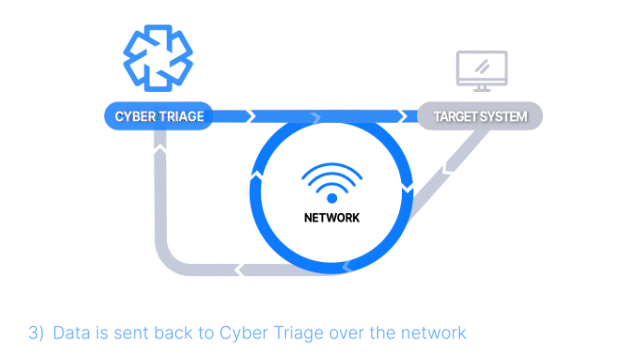
Over The Network with PsExec
How Does it Work: The Collector is copied to the target system via PsExec, launched, and artifacts are sent back over the network. A list of hosts can be added.
How It’s Different: Everything is done over the network, and no interactive access is required.
Common Use Cases:
-
- Internal SOC teams investigating alerts
- Integration with SOAR workbooks (requires a Team license)
- Scoping an incident at a client site
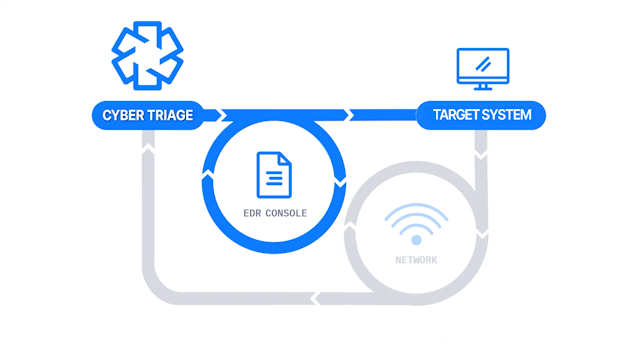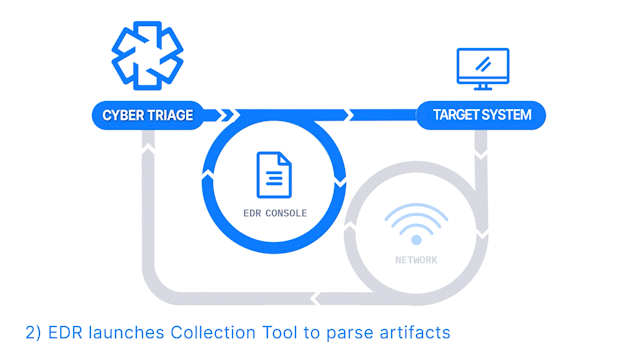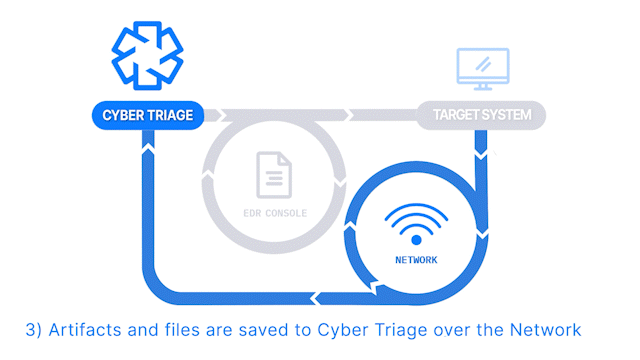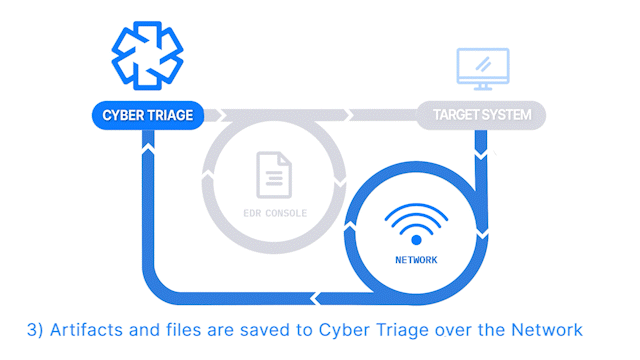
Deploy with EDR
How Does it Work: The Collector is launched on target computers using an EDR or X. The results are then sent to a waiting Cyber Triage server to be immediately analyzed. This requires a Team license.
How It’s Different: Deploy to dozens or hundreds of computers using existing IT infrastructure.
Common Use Cases:
- SOCs who want more in-depth data than what the EDR provides
- Consultants who are scoping an incident in an environment with no EDR
Manual Launch Scenarios
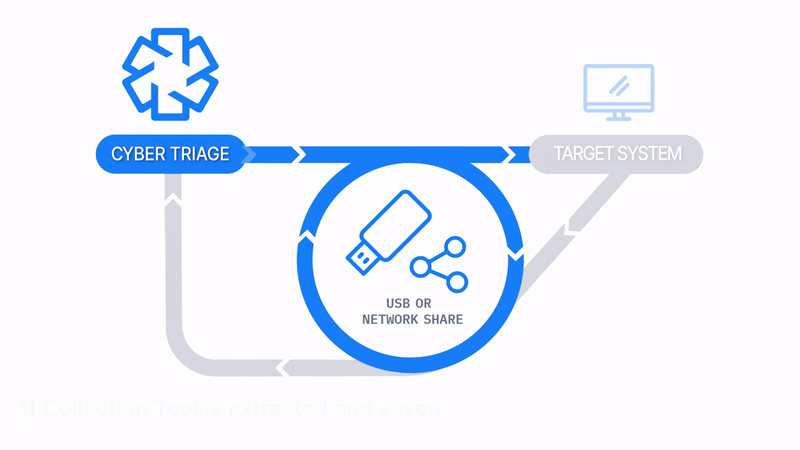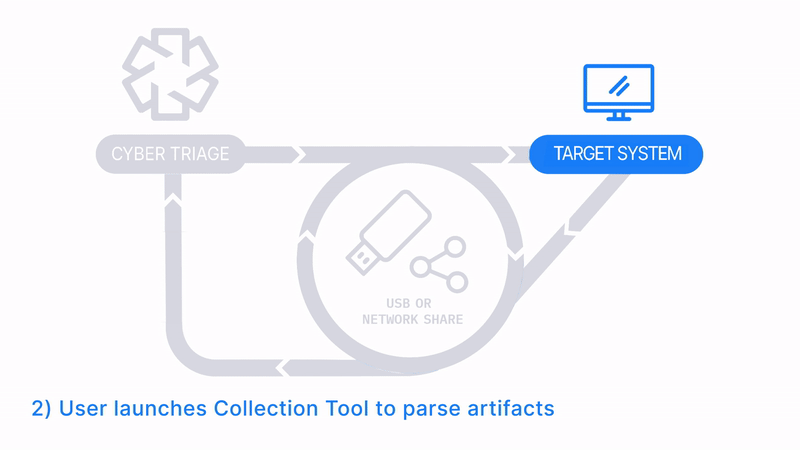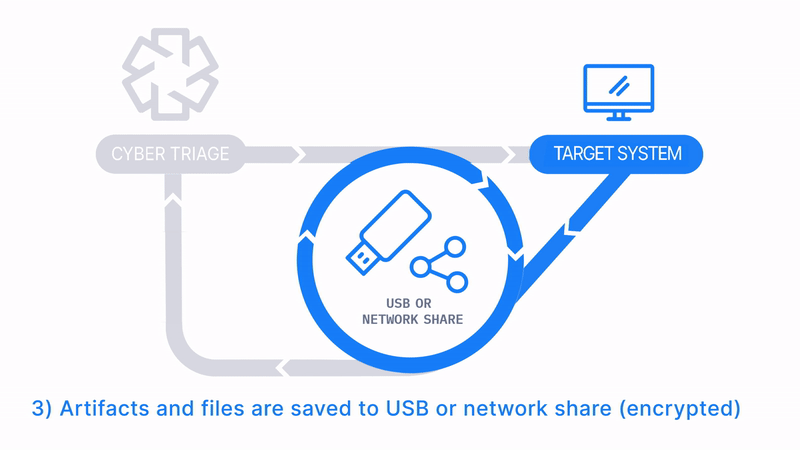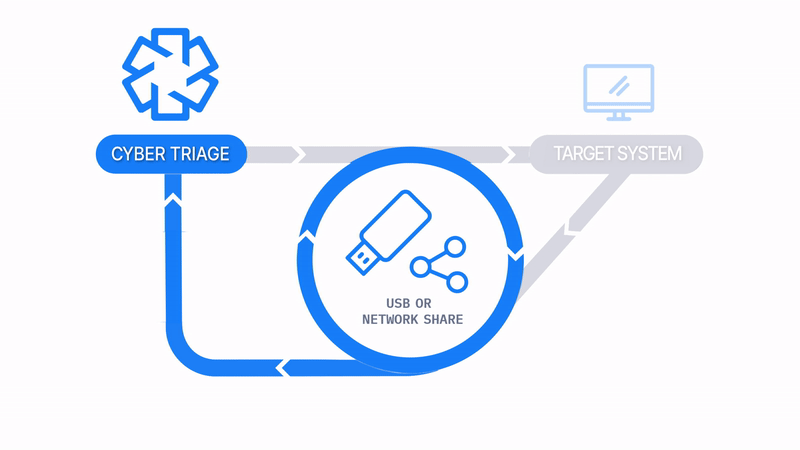
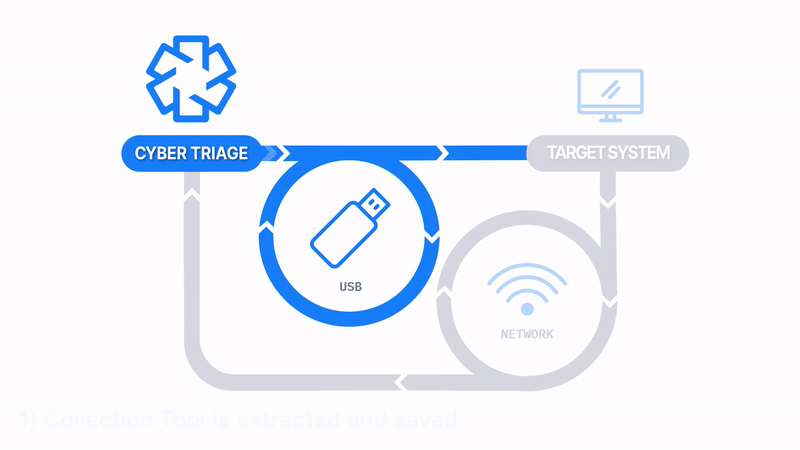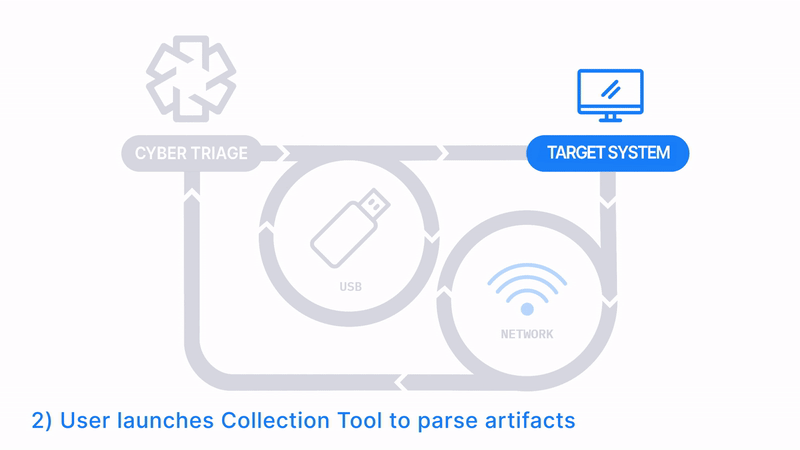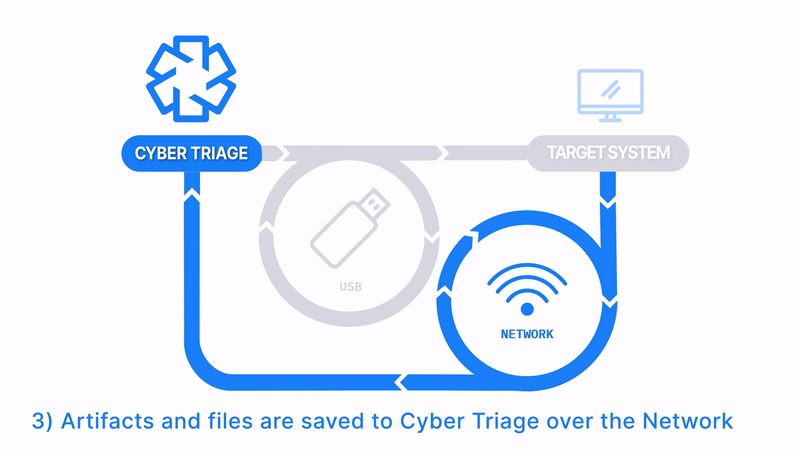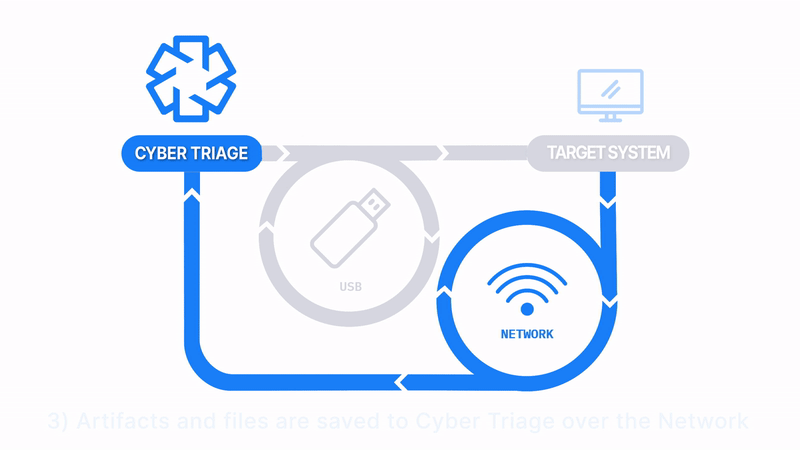
Launch From and Save To USB or Network Drive
How Does it Work: The Collector is copied to a USB drive, it’s manually run on the target system, and artifacts are saved back to the USB. The data is then manually imported into Cyber Triage. Files can be imported in batches using a Standard Pro or Team license.
How It’s Different: No network is required.
Common Use Cases:
- Consultants/MSSPs send the Collector to the client for them to do the collection.
- The target system is removed from the network.
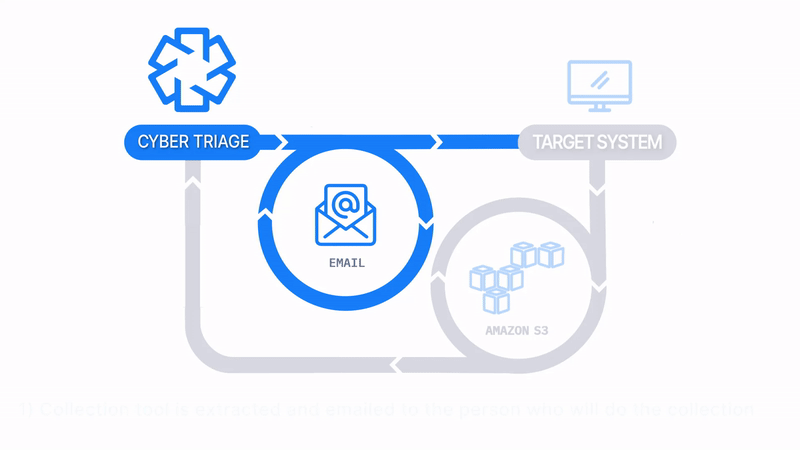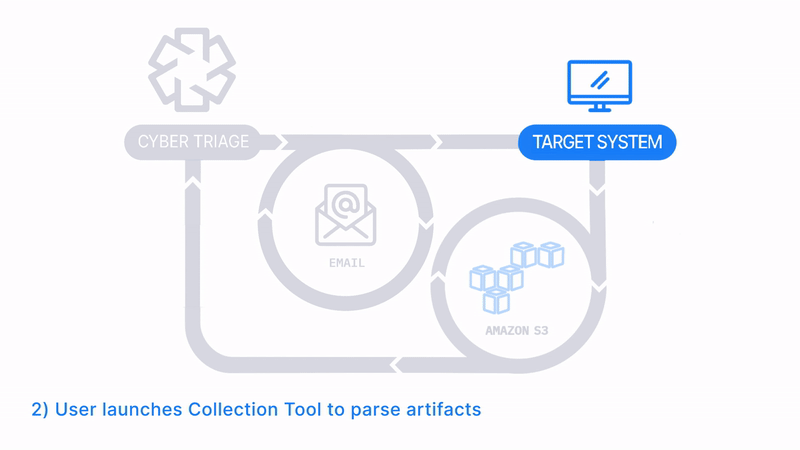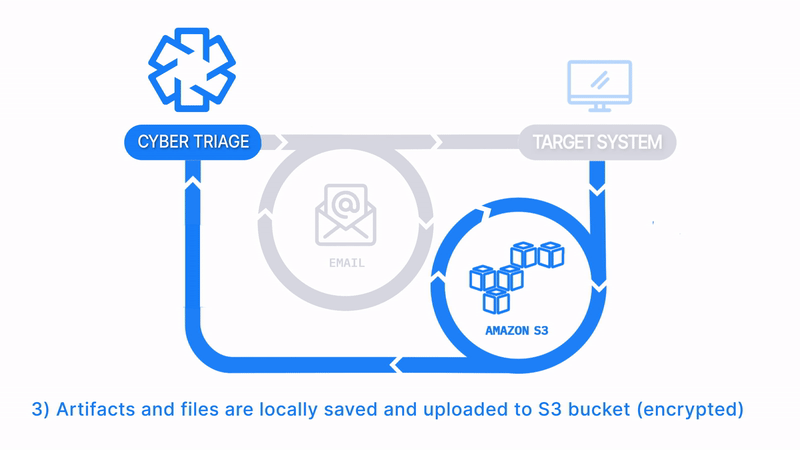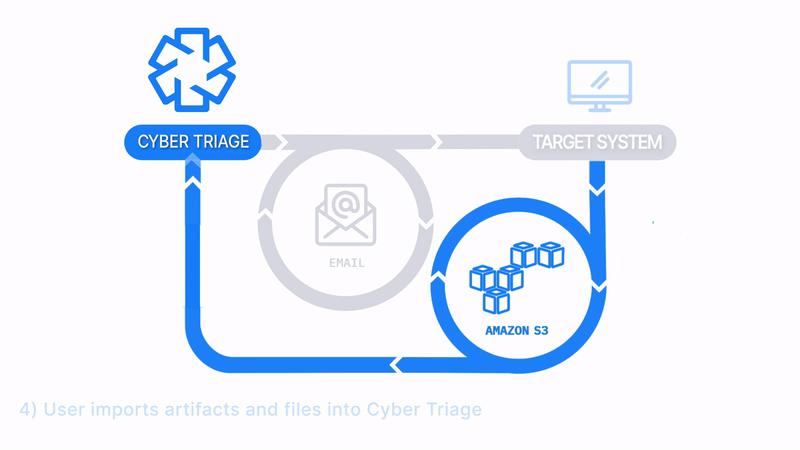
Email The Collector and Save to S3 or Azure
How Does it Work: The Collector is emailed to a client or local IT member, they run it on the target system, and artifacts are uploaded to an S3 or Azure bucket. The data is then manually imported into Cyber Triage.
How It’s Different: Uploads to S3 buckets or Azure
Common Use Cases:
- Consultants have clients upload data to their S3 bucket as a data staging area.
- Remote office locations send data to the main SOC via corporate S3 buckets.
Manually Launch and Send Back Over The Network
How Does It Work: The Collector is copied to a USB drive, it’s manually run on the target system, and artifacts are sent back over the network.
How It’s Different: Someone else can start the collection, but the responder sees the results immediately. Responder doesn’t need admin credentials.
Common Use Cases:
- Security teams doesn’t have administrator credentials on an endpoint, and the local IT person starts the collection.
- Consultants who are not given administrator credentials and local IT starts the collections.
Import Other Data Sets
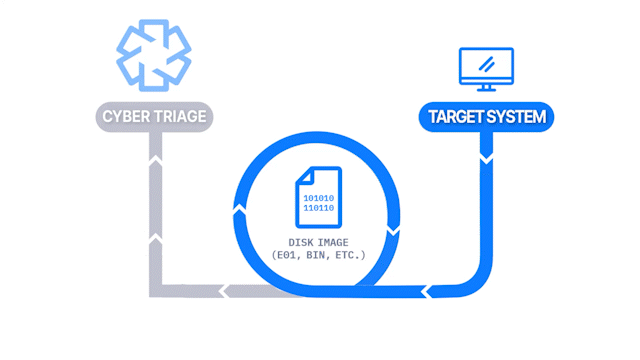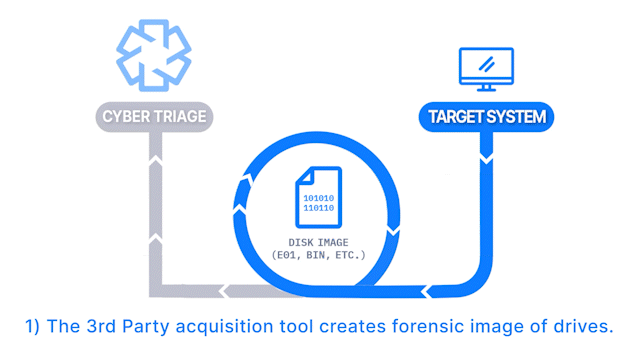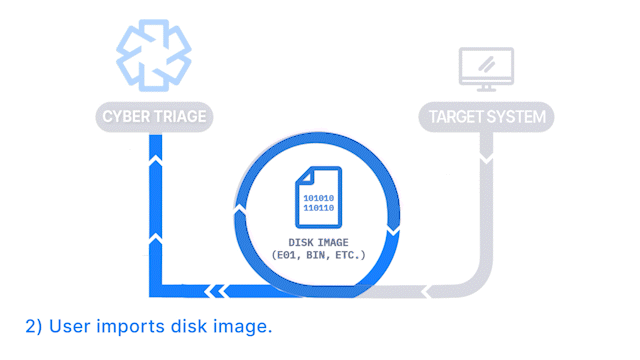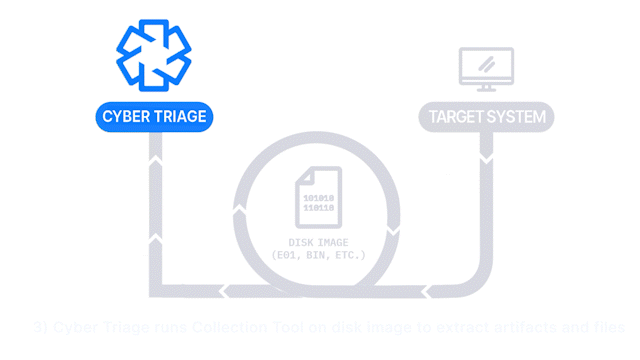
Disk Image
How Does it Work: A disk image is created with a 3rd party tool and then analyzed by Cyber Triage. File system-based artifacts are extracted and analyzed.
How It’s Different: It allows you to import a disk image.
Common Use Cases: Consultants or law enforcement that are given data after another has started the investigation. As part of a deeper dive to determine the root cause.
Memory Image
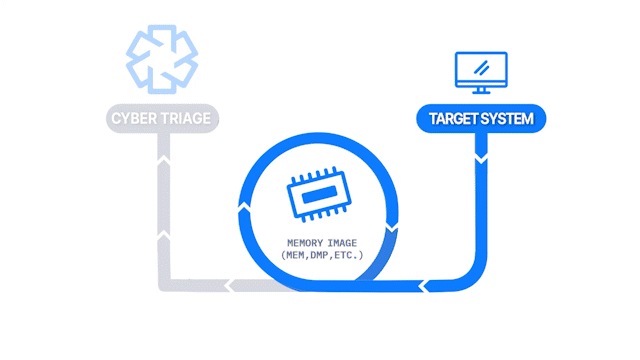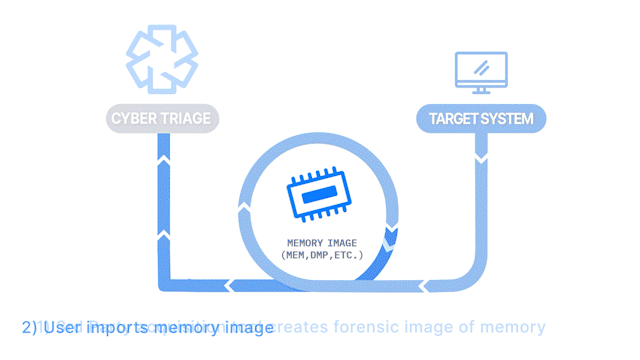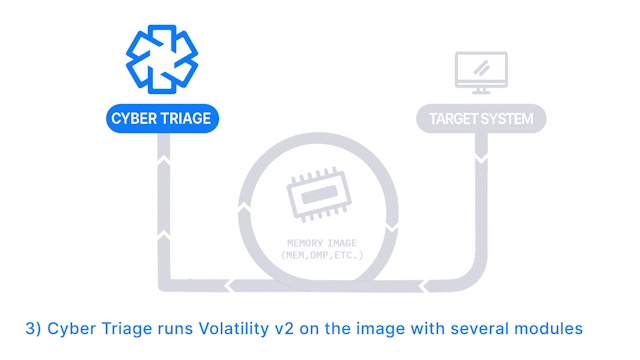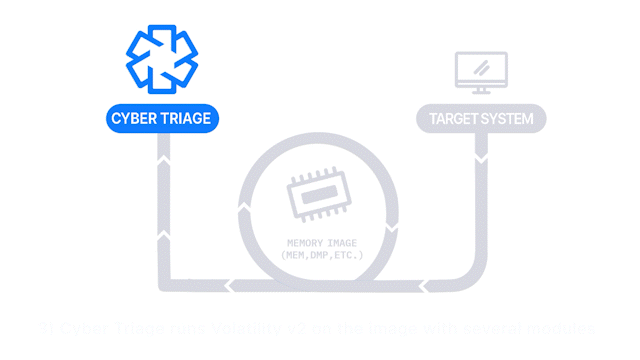
How Does it Work: A memory image is created with 3rd party tool and then analyzed using Volatility v2.
How It’s Different: It allows you to import a memory image.
Common Use Cases: Responders want to parse raw memory images to find advanced malware and persistence mechanisms.
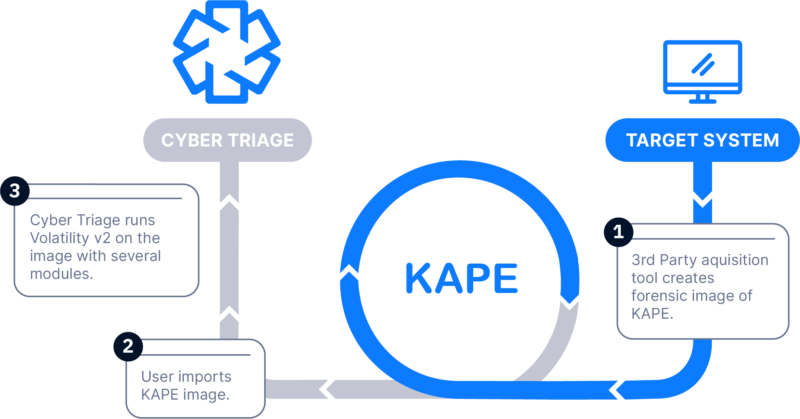
KAPE Data
How Does It Work: KAPE is used to collect data from a live system. The resulting VHD with registry hives and event logs is then imported and analyzed.
How It’s Different: Allows you to import KAPE data.
Common Use Cases: Responders who use KAPE for their initial collection want to use Cyber Triage scoring on the results. Responders are given a KAPE collection acquired by their customer or another response team.
Faster Forensics For Even Faster Remediation With Cyber Triage
Plans start as low as $208/month for unlimited support and 4000 daily scans with ReversingLabs.