Velociraptor is a powerful agent-based, open-source DFIR tool that you can now use to easily deploy the Cyber Triage Collector. This allows you to use:
- Velociraptor to query and scan hundreds or thousands of endpoints for indicators.
- Cyber Triage to dive into the 10 to 20 that the attacker was active on.
This post covers the basics of the integration. Consult the user manual for details.
Jump to…
Velociraptor Basics
Why Cyber Triage + Velociraptor
Deploying the Cyber Triage Collector
Collect Artifacts Using Velociraptor
Try It Out
Velociraptor Basics
Velociraptor uses an on-premise server and agents on each endpoint.
There are 3 main functions:
- Collect: Copy specific files or artifacts on one or more hosts. Results can come back similar to KAPE outputs.
- Monitor: Have events sent back to the server for telemetry.
- Hunt: Perform queries in the enterprise to see where an item is.
We have several DFIR customers who use it in environments where EDRs do not exist. Velociraptor allows them to deploy agents to get visibility and identify where to start.
However, when they want to triage the endpoints to understand what happened, they pivot to Cyber Triage. It helps them more quickly look at historical lateral movement, processes, and system changes. Once they find evidence using Cyber Triage, they jump back to Velociraptor to hunt for other systems with the same indicators.
Why Cyber Triage + Velociraptor
Cyber Triage and Velociraptor both have their strengths and their combination allows teams to quickly investigate.
Velociraptor is optimized to run queries and collect data from hundreds and thousands of systems. Cyber Triage is optimized for triaging endpoints and assisting the investigator to find evidence.
Cyber Triage can work with Velociraptor in 2 ways:
- Launch the Cyber Triage Collector out via the Velociraptor agents.
- Use the built-in Velociraptor Windows.KapeFiles.Targets Artifact to make a KAPE-like folder that can be imported into Cyber Triage; though, we recommend you use the Collector to get more executable files.
Once that data comes into Cyber Triage, analysis begins:
- Artifacts are parsed from the source files.
- Artifacts are scored as bad or suspicious.
- As the user reviews the items and scores additional items, Cyber Triage will recommend others.
Deploying the Cyber Triage Collector
The Cyber Triage Collector is a single Windows executable that has no dependencies. All you need to do is get it to an endpoint and run it.
Its results can be sent to:
- A local file
- Cloud storage (S3/Azure)
- Cyber Triage Server
You can run it from a USB drive, via PsExec, or using agents, such as EDRs and Velociraptor.
When using agents, we recommend you use our Deployer script. It’s a Powershell script that will download the Collector EXE and launch it using the settings that you configured (cloud storage, local file, encryption, etc.).
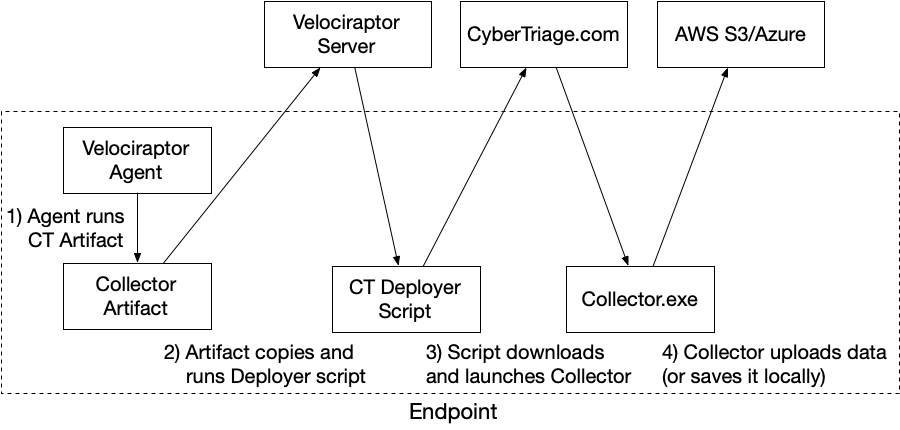
Collect Artifacts Using Velociraptor
The high-level steps to setup the Cyber Triage Collector using Velociraptor are:
- Download the Deployer script and configure it based on where you want the results to go.
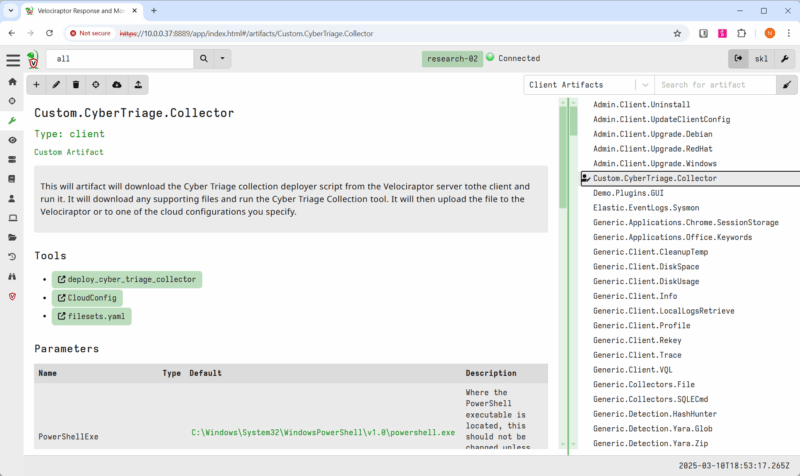
- Install the CyberTriage.Collector artifact from the Velociraptor Artifact Exchange. This artifact will ultimately run the previously configured Deployer script.
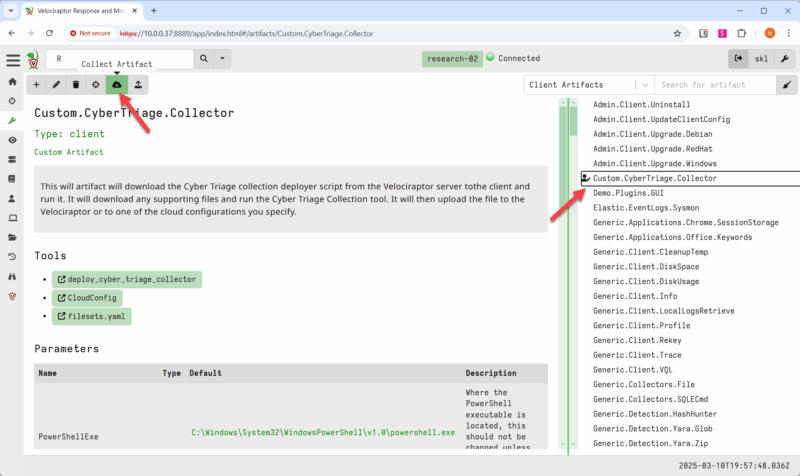
When you want to run the Collector, then:
- Select the device.
- Add the CyberTriage.Collector artifact to the Collection package.
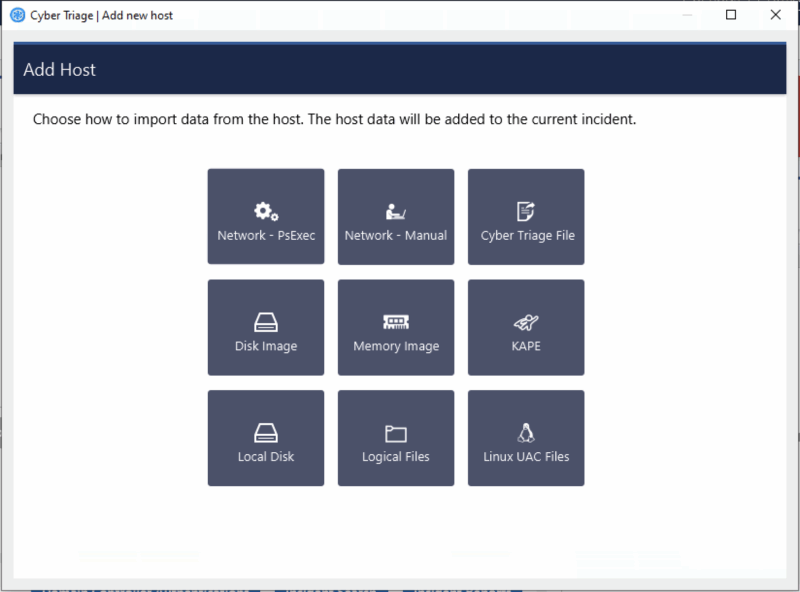
The artifacts will be sent to wherever you configured the Deployer script. You can then import the results into Cyber Triage using the “Cyber Triage File” feature.
Details for using Cyber Triage and Velociraptor can be found here.
Try It Out
Try the integration out and contact support if you have any questions. If you haven’t used Cyber Triage before to investigate endpoints, then try out the 7-day eval here. It will make your investigations faster and more comprehensive.
