Welcome back to the next post in our DFIR Next Steps series on remote monitoring and management (RMM) tools. This post will focus on LogMeIn products.
Check out our previous posts in the series:
Now, let’s get into LogMeIn!
Jump to…
LogMeIn Overview
LogMeIn Indicators of Existence
Exe names
Domains
Folders
Windows events
Registry keys
Log files
DFIR Next Steps: How to Investigate Suspicious LogMeIn Use
How to Investigate Suspicious LogMeIn Use with Cyber Triage
LogMeIn Overview
LogMeIn is more than just the name of a tool. It’s a brand with many different cloud-based IT solutions. The LogMeIn brand is part of the larger GoTo company that includes the suite of GoTo applications (GoTo Meeting, GoTo Webinar, GoTo Training, etc.).
For the purpose of this post we will focus on the traditional LogMeIn tools that provide remote access and management capabilities.
These include:
Notes
RemotelyAnywhere is not covered in this post. While GoTo continues to provide support for RemotelyAnywhere, licensing for the tool does not appear to be available to new customers. It has been replaced by the other LogMeIn products
The GoTo based tools will be left for future blog posts: GoToMyPC, LogMeIn Resolve (formerly known as GoTo Resolve), and GoToAssist. We chose to group Resolve with the other GoTo products instead of LogMeIn because it was historically a GoTo product that still uses the GoTo infrastructure and naming. And while GoTo continues to provide support for GoToAssist, the tool is no longer available to new customers. It has been replaced by LogMeIn Resolve.
LogMeIn Rescue
| Target Use Case | What Can It Do | How It Can Be Abused |
|---|---|---|
|
Ad-hoc remote support sessions for helpdesk teams, MSPs, and customer support. |
Provides simple on-demand remote support with little to no setup for clients. Remote screen share can be done through a browser while remote control requires the execution of a single exe provided by the support interface. It allows screen sharing, remote control, bidirectional file transfer, and unattended access. |
Rescue is more likely to be abused by tech support scammers due to its ease of use in setting up on-demand remote sessions via URLs. However, the unattended access feature can be abused by threat actors to provide persistent remote access to compromised systems. |
LogMeIn Pro
| Target Use Case | What Can It Do | How It Can Be Abused |
|---|---|---|
|
Persistent remote access to systems for individuals or small teams. |
Provides a streamlined process of obtaining persistent remote access to systems without the need of user intervention. Remote sessions provide the ability to screen share, remote control, file transfer, and console-based access. |
Threat actors can either install LogMeIn on compromised systems to provide backdoor access or compromise a LogMeIn cloud account to gain access to all remote systems and abuse the currently deployed infrastructure. |
LogMeIn Central
| Target Use Case | What Can It Do | How It Can Be Abused |
|---|---|---|
|
Remote monitoring and management of large fleets of endpoints with automation and policy control. Generally geared towards IT administrators and large MSPs. |
Central uses the same technology as Pro with additional features such as scripting automation, device patching, monitoring and alerting, additional deployment methods, and is optimized for managing large fleets of devices. |
Threat actors can either install LogMeIn on compromised systems to provide backdoor access or compromise a LogMeIn cloud account to gain access to all remote systems and abuse the currently deployed infrastructure. |
LogMeIn Indicators of Existence
This section provides key indicators used to identify the existence of LogMeIn activity on both systems being remote controlled as well as systems initiating remote access activity.
Exe Names
Knowing the various exe names and when they are used can help identify what LogMeIn product is in use as well as the specific usage scenario.
For example:
If we see “LMIRTechConsole.exe,” we know that LogMeIn Rescue is used on the system and that the system is being used to remote into other devices as opposed to the device being remoted into.
LogMeIn Rescue
| Source* |
|---|
LogMeInRescueTechnicianConsoleApp.msi
|
LMIRTechConsole.exe
|
LMIGuardianSvc.exe
|
| Destination** |
|---|
Support-LogMeInRescue.exe
|
LMI_Rescue.exe
|
LMI_Rescue_Srv.exe
|
LMI_RescueRC.exe
|
Unattended_srv.exe
|
Unattended.exe
|
LogMeIn Pro and LogMeIn Central
| Source* |
|---|
LogMeInClientApp.msi
|
LMIIgnition.exe
|
LMIGuardianSvc.exe
|
| Destination** |
|---|
LogMeIn.msi
|
LogMeIn.exe
|
LogMeInRC.exe
|
LogMeInSystray.exe
|
LogMeInToolkit.exe
|
LMIGuardianSvc.exe
|
RaMaint.exe
|
* Source is the machine initiating remote session.
** Destination is the machine being remote controlled.
Domains
Knowing what domains are related to LogMeIn activity enables users to determine the LogMeIn product in use and in certain scenarios the activity at hand.
For example:
- Some URLs are used to download setup exes onto remote endpoints to provide support.
- Some can be used to identify when a remote session has begun.
- Others are used for management of remote endpoints.
LogMeIn Rescue
| logmeinrescue.com | |
|---|---|
| Subdomain | https://secure.logmeinrescue.com/Account/Login |
| Details | LogMeIn Rescue account logon page. Indicates that someone is attempting to log into a LogMeIn Rescue cloud account. |
| Subdomain | https://secure.logmeinrescue.com/webtc/ |
| Details | Web console. Indicates someone has access to a LogMeIn Rescue account and is looking to access a system remotely. |
| Subdomain | https://secure.logmeinrescue.com/TechConsole/DesktopApp/Download.aspx |
| Details | Main download link for Rescue desktop app. It downloads LogMeInRescueTechnicianConsoleApp.msi used to remote into devices similar to the web console. |
| Subdomain | https://secure.logmeinrescue.com/customer/code.aspx |
| Details | Web client used to join a session. User needs to enter a support code to join the support session. If valid, leads to https://console.logmeinrescue.com/chat. |
| Subdomain | https://console.logmeinrescue.com/connect/502050387 |
| Details | Direct link to access a support session. Number on the end is unique to each support session created. If valid, user is redirected to https://console.logmeinrescue.com/chat. |
| Subdomain | https://console.logmeinrescue.com/chat/633941077 |
| Details | Web client in a support session. |
| Subdomain | https://secure.logmeinrescue.com/Customer/Download.aspx?PrivateCode=269601&CompanyID=5546223&URLReferrer=https%3a%2f%2fconsole.logmeinrescue.com%2f&ClickOnceBOFlag=False |
| Details | URL to download remote access client (Support-LogMeInRescue.exe). Users are generally prompted to click a download button to get the remote access support client when prompted by the support technician. |
| Subdomain | https://secure.logmeinrescue.com/UnattendedAccess/Generator.aspx |
| Details | URL to download custom-made unattended access installer made from the web console |
| Subdomain | rsc-*****-**.logmeinrescue.com |
| Details | LogMeIn cloud infrastructure to handle remote sessions. Ex: rsc-www26-03.logmeinrescue.com or rsc-app26-03.logmeinrescue.com |
| logmeinrescue.eu | |
|---|---|
| Details | Same examples as logmeinrescue.com except the new domain. |
| logmeinrescue-enterprise.com | |
|---|---|
| Details | Same examples as logmeinrescue.com except the new domain. |
| logmein123.com | |
|---|---|
| Details | Old URL that redirects to https://secure.logmeinrescue.com/Customer/Code.aspx |
| logmein123.eu | |
|---|---|
| Details | Old URL that redirects to https://secure.logmeinrescue.eu/Customer/Code.aspx |
| logmein.com | |
|---|---|
| Subdomain | rsc-*****-**.logmeinrescue.com |
| Details | LogMeIn cloud infrastructure. Ex: rsc-app26-04.logmein.com |
LogMeIn Pro and LogMeIn Central
| logmein.com | |
|---|---|
| Subdomain | https://secure.logmein.com/central/Central.aspx |
| Details | Tech/IT web management console. |
| Subdomain | https://secure.logmein.com/LogMeInClientApp.msi |
| Details | Windows installer to make remote connections. |
| Subdomain | https://secure.logmein.com/Logmein.msi |
| Details | Windows installer to allow remote access to the system. |
| Subdomain | https://secure.logmein.com/addacomputer3_msi.aspx |
| Details | Download link for custom-configured LogMeIn.msi via the web management console. |
| Subdomain | lmi-*****-**.logmein.com |
| Details | LogMeIn cloud infrastructure. Ex: lmi-www26-04.logmein.com or lmi-app26-04.logmein.com. |
Folders
Knowing what folders exist on a system related to LogMeIn activity can shed light on some of the following activity:
- When the tool was first used.
- When a remote session was initiated.
- When a user associated an account with a management app.
- When an app was first closed.
LogMeIn Rescue
| Source* | |
|---|---|
| Folder | C:\Program Files*\LogMeIn Rescue Technician Console |
| Details | Default installation location for the desktop app “LMIRTechConsole.exe” that is created by LogMeInRescueTechnicianConsoleApp.msi. |
| Folder | C:\Users\*\AppData\LocalLow\LogMeIn Rescue |
| Details | Created on startup of the desktop app “LMIRTechConsole.exe,” if it doesn’t already exist. Contains web app-related files and data. The .log files that do exist in the folder are not plain text. |
| Folder | %localappdata%\LogMeIn Rescue\update |
| Details | Created when a valid account is signed into the desktop app “LMIRTechConsole.exe,” if it doesn’t already exist. Appears to be a staging location for updates, but did not see files during testing. |
| Folder | %localappdata%l\LogMeIn\Dumps |
| Details | Created on exit of “LMIGuardianSvc.exe” that exits when the desktop app “LMIRTechConsole.exe” is closed, if it doesn’t already exist. Appears to be a staging location for crash dump and debug info, but did not see files during testing. |
| Folder | C:\ProgramData\LogMeIn\Dumps |
| Details | Created on exit of “LMIGuardianSvc.exe” that exits when the desktop app “LMIRTechConsole.exe” is closed, if it doesn’t already exist. Appears to be a staging location for crash dump and debug info, but did not see files during testing. |
| Destination** | |
|---|---|
| Folder | %localappdata%l\LogMeIn Rescue Applet\ |
| Details | Created on start of the client downloader “Support-LogMeInRescue.exe.” Used for temporary support sessions and not “unattended access” sessions. Contains subfolders (ex: LMIR0B345001.tmp), each representing a support session. Subfolders are normally cleaned up when the session is closed via bat files placed in %localappdata%. Ex: LMIR0B345001.tmp.bat and LMIR0B345001.tmp_r.bat. Subfolders contain all the relevant exes/DLLs and logs related to the session. |
| Folder | C:\Program Files*\LogMeIn Rescue Applet\ |
| Details | Created when a support technician requests system-level access. Clients are prompted to confirm a UAC prompt to elevate privileges. Same content as the %localappdata% version. Also used when unattended access is set up. Creates a new subfolder session each time there is a connection. |
| Folder | C:\ProgramData\LogMeIn Rescue Applet\ |
| Details | Contains temp session folders that appear to be cleaned up. Generated when unattended access is used. |
| Folder | %localappdata%\LogMeIn Rescue Unattended\ |
| Details | Same idea as %localappdata%l\LogMeIn Rescue Applet\ except this folder is used for “unattended access” sessions. Content is not. The bat files to clean up folders are also put into C:\Program Files (x86). |
| Folder | C:\Program Files*\LogMeIn Rescue Unattended\ |
| Details | Used when unattended access is set up. |
| Folder | C:\ProgramData\LogMeIn Rescue Unattended\ |
| Details | Used when unattended access is set up. |
LogMeIn Pro and LogMeIn Central
| Source* | |
|---|---|
| Folder | C:\Program Files (x86)\LogMeIn Ignition |
| Details | Default installation location for the desktop client “LMIIgnition” and its supporting binaries. |
| Folder | %localappdata%\LogMeInIgnition |
| Details | Created on startup of the desktop app “LMIIgnition.exe,” if the folder does not already exist. |
| Folder | %localappdata%\LogMeInIgnition\Update |
| Details | Created when a valid account is signed into the desktop app “LMIIgnition.exe,” if the folder does not already exist. |
| Folder | %localappdata%l\LogMeIn\Dumps |
| Details | Created on exit of “LMIGuardianSvc.exe” that exits when the desktop app “LMIIgnition.exe” is closed, if it doesn’t already exist. Appears to be a staging location for crash dump and debug info, but did not see files during testing. |
| Folder | C:\ProgramData\LogMeIn\Dumps |
| Details | Created on exit of “LMIGuardianSvc.exe” which exits when the desktop app “LMIIgnition.exe” is closed, if it doesn’t already exist. Appears to be a staging location for crash dump and debug info, but did not see files during testing. |
| Destination** | |
|---|---|
| Folder | C:\Program Files (x86)\LogMeIn |
| Details | Default installation location for the host exe “LogMeIn.exe and its supporting binaries. |
| Folder | C:\ProgramData\LogMeIn |
| Details | Created when LogMeIn service first runs. This is where the service logs its activity “LogMeIn.log.” |
| Folder | C:\Program Files (x86)\LogMeIn Ignition |
| Details | Default installation location for the desktop client “LMIIgnition” and its supporting binaries. |
| Folder | %localappdata%\LogMeInIgnition |
| Details | Created on startup of the desktop app “LMIIgnition.exe,” if the folder does not already exist. |
| Folder | %localappdata%\LogMeInIgnition\Update |
| Details | Created when a valid account is signed into the desktop app “LMIIgnition.exe,” if the folder does not already exist. |
| Folder | %localappdata%l\LogMeIn\Dumps |
| Details | Created on exit of “LMIGuardianSvc.exe” that exits when the desktop app “LMIIgnition.exe” is closed, if it doesn’t already exist. Appears to be a staging location for crash dump and debug info, but did not see files during testing. |
| Folder | C:\ProgramData\LogMeIn\Dumps |
| Details | Created on exit of “LMIGuardianSvc.exe” which exits when the desktop app “LMIIgnition.exe” is closed, if it doesn’t already exist. Appears to be a staging location for crash dump and debug info, but did not see files during testing. |
Windows Events
LogMeIn Rescue
| Security Event Log | |
|---|---|
| Events | 4624/4625 successful/failed logon. |
| Details | Look for logon events with a process of “LMI_Rescue_Srv.exe” or “unattended_Srv.exe” for when a user had to enter credentials to logon or requested system privilege elevation on the remote system. Logons are type 2 “local interactive,” so there will be no remote host information. |
|
Application Event Log |
|
|---|---|
|
Source = MSIInstaller |
|
| Event |
1040/1042 installer transaction start/stop. |
| Details |
Provides the path and name of the MSI. Search for “LogMeInRescueTechnicianConsoleApp.msi”. |
| Event | 1033 installation status. |
| Details | Provides product name regarding the MSI being installed and the status, if it was successful or not. Look for product name containing “LogMeIn Rescue.” |
| System Event Log | |
|---|---|
| Events | 7045 (service installed). |
| Details | Look for services that start with “LogMeIn Rescue” that indicates either unattended access or elevation to system privileges for a temporary session. |
LogMeIn Pro and LogMeIn Central
| Security Event Log | |
|---|---|
| Events | 4624/4625 successful/failed logon. |
| Details | Look for logon events with a process of “LogMeIn.exe” for when a user had to enter credentials to authenticate to a remote system. Logons are type 2 “local interactive,” so there will be no remote host information. |
|
Application Event Log |
|
|---|---|
|
Source = MSIInstaller |
|
| Event |
1040/1042 installer transaction start/stop. |
| Details |
Provides the path and name of the MSI. Search for “LogMeInClientApp.msi” or “LogMeIn.msi”. |
| Event | 1033 installation status. |
| Details | Provides product name regarding the MSI being installed and the status, if it was successful or not. Look for product name containing “LogMeIn.” |
| Source = LogMeIn | |
| Event | 104 Unsuccessful logon attempt. |
| Details | Contains public IP that initiated the attempt. |
| Event | 102/105 Successful logon/logoff. |
| Details | Contains the public IP that initiated the connection and user logged on. |
| Event | 202/205 Start/end of remote session. |
| Details | Contains the public IP that initiated the connection and user logged on. |
| System Event Log | |
|---|---|
| Events | 7045 (service installed). |
| Details |
|
Registry Keys
LogMeIn Rescue
| Source* |
|---|
HKU\Software\LogMeInRescue
|
HKLM\SOFTWARE\WOW6432Node\LogMeInRescue
|
| Destination** |
|---|
| N/A |
LogMeIn Pro and LogMeIn Central
| Source* |
|---|
HKLM\SOFTWARE\WOW6432Node\LogMeIn Ignition
|
HKU\Software\LogMeIn Ignition
|
| Destination** |
|---|
| HKLM\SOFTWARE\LogMeIn |
| HKLM\SOFTWARE\LogMeIn, Inc. |
| HKU\Software\LogMeIn |
Log files
LogMeIn Rescue
| Source* |
|---|
| N/A |
| Destination** |
|---|
Session.log
|
LogMeIn Pro and LogMeIn Central
| Source* |
|---|
C:\ProgramData\LogMeIn\LogMeInBrowserPlugin.log
|
C:\ProgramData\LogMeIn\PluginYYYYMMDD.log
|
%localappdata%\LogMeInIgnition\LogMeInIgnition.log
|
%localappdata%\LogMeInIgnition\LogMeInIgnitionYYYYMMDD.log
|
| Destination ** |
|---|
C:\ProgramData\LogMeIn\LogMeIn.log
|
C:\ProgramData\LogMeIn\LMIYYYYMMDD.log
|
DFIR Next Steps: How to Investigate Suspicious LogMeIn Use
The goal of this section is to provide some investigative questions that should be answered to help determine if the LogMeIn activity on the system is expected.
4 we’ll review:
- What LogMeIn product is being used?
- Does the organization use that LogMeIn product?
- Is it expected on that endpoint?
- Is the activity expected?
Now, let’s dig into each:
| #1 What LogMeIn product is being used? |
|---|
| For example, Rescue, Pro/Central, or Resolve. Various indicators previously discussed can help to identify which LogMeIn product is being used. Exe names, folder paths, installers, and web activity can be used to distinguish between Rescue and Pro/Central. |
| #2 Does the Organization Use that LogMeIn Product? | |
|---|---|
| Yes | Go to question 3 |
| No | Unauthorized LogMeIn tool found and should most likely be removed. Proceed to question 4 to determine the impact. Ex: Did a threat actor bring it in, did a disgruntled IT administrator use it for nefarious activity, or was it an employee using it without bad intentions? |
| #3 Is It Expected on that Endpoint? | |
|---|---|
| Yes | Depending on the context of the alert that triggered the investigation, you can stop here or proceed to question 4. If the alert was that an RMM tool was found running on a system, you can probably stop and tune your alerting. However, if there is other suspicious activity around the LogMeIn activity, further analysis should be performed. |
| No | LogMeIn should be removed from the device, and proceed to question 4 to determine the impact. |
| #4 Is the activity expected? |
|---|
| There are a lot of subquestions that need to be answered to answer the bigger question of if the activity is expected.
Questions like:
|
How to Investigate Suspicious LogMeIn Use with Cyber Triage
Cyber Triage can be used to find RMM tools like LogMeIn on systems without the need for analysts or responders to remember all of the various file names, folder paths, web artifacts, log files, or registry keys. That detection logic is built into Cyber Triage to automate this process so defenders can spend more time determining if the RMM tool activity is expected or not.
Cyber Triage will:
- Detect if an RMM tool exists on the system (over 40 products).
- Provide insight into how long the RMM tool has been on the system based on the various indicators of existence previously been mentioned.
From there, analysts can follow the next steps outlined above to determine if the activity is expected or not.
We have had engagements where Cyber Triage has flagged 3 or 4 different tools on a single endpoint. Even if these are not a result of malicious activity it can help to root out poor security practices and act as a preventative measure to better secure access to such devices.
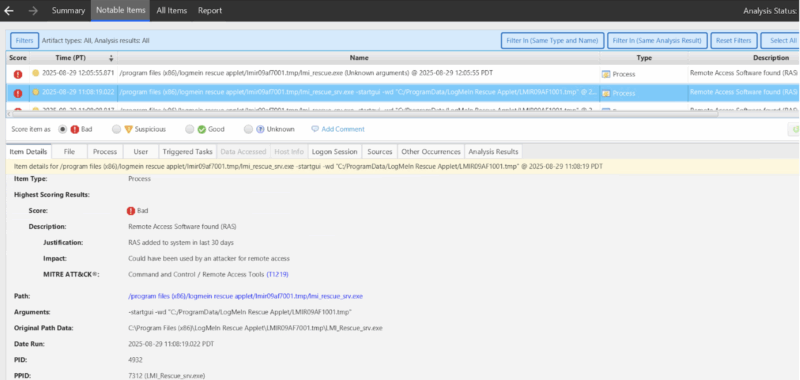
Example of Cyber Triage detecting LogMeIn Rescue activity new to a system.
If you’d like to try Cyber Triage on an RMM investigation — or just to see if it speeds up your process in general — you can free for 7 days.
