Welcome back to the next post in our DFIR Next Steps series on remote monitoring and management (RMM) tools. This post will focus on AnyDesk.
Check out our previous posts in the series:
- Overview of investigating suspicious RMMs
- Investigating suspicious TeamViewer use
- Investigating suspicious LogMeIn use
Now, let’s analyze AnyDesk!
Jump to…
AnyDesk Overview
AnyDesk Indicators of Existence
Exe Names
Config/Log Files
Folders
Domains
DFIR Next Steps: How to Investigate Suspicious AnyDesk Use
How to Investigate Suspicious AnyDesk Use with Cyber Triage
AnyDesk References
AnyDesk Overview
AnyDesk is a remote desktop application developed by AnyDesk Software GmbH.
It enables platform-independent remote access across:
- Windows
- macOS
- Linux
- iOS
- Android
- And more
It has features like:
- VPN
- REST API
- File transfer
- Session logs
- Remote printing
- Unattended access
- And more
6Sense reports that AnyDesk has up to 10% of the remote support market share, second only to TeamViewer.
AnyDesk is significantly more straightforward in its fingerprint and its offerings compared to TeamViewer and LogMeIn. There is a single exe used for all scenarios (client, server, service) that is highly configurable. AnyDesk is also the only software product, but it has different licensing tiers that enable additional functionality in the product.
Key features:
| Feature | Details |
|---|---|
| Simple and easy to deploy | Single exe that’s highly configurable and can be installed using the exe. |
| Can run as single exe | More likely to be used in tech support scam because it’s easy to download and deploy. |
| Can be installed | More likely to be used in ransomware attacks for persistence. |
| Unattended access | No user interaction is required on the remote system making stealthy remote access easy. |
| No account requirement | AnyDesk does not require an account to be made to use its product. Although the capabilities are limited without a license.* |
| Flexible deployment | Cloud and on-premises capabilities exist. |
NOTE
*This differs from TeamViewer and LogMeIn. They both require an account to be associated with their software to initiate outgoing connections.
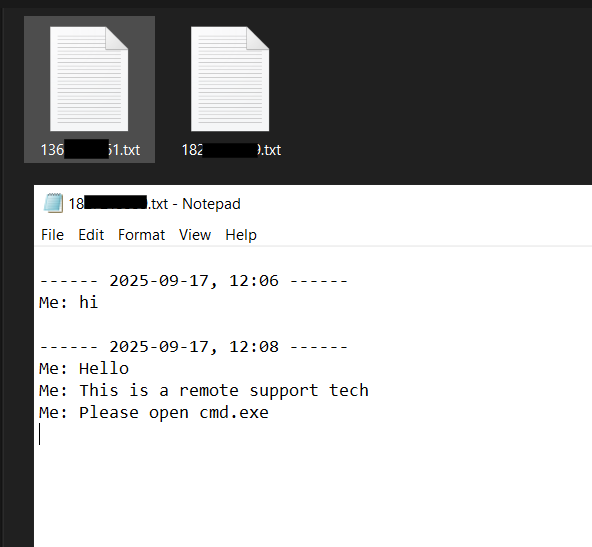
Examples of AnyDesk abuse:
- DFIR Report: Ransomware group installed AnyDesk to maintain persistence.
- CISA: Portable version of AnyDesk was abused by threat actors to maintain persistence to the system and carry out refund scams.
- ThreatDown: Ransomware groups installed AnyDesk to maintain persistence and go undetected using “known” and “safe” RMM tools.
- CyberSecurityNews: AnyDesk was used to maintain persistence, exfil data, and bring in additional malicious PowerShell payloads.
AnyDesk Indicators of Existence
This section provides a list of indicators you can use to identify AnyDesk activity on an endpoint.
Exe Names
| AnyDesk.exe/AnyDesk*.exe |
|---|
| Description: AnyDesk uses a single exe for all of its functionality, but it’s highly configurable. |
Known path(s):
|
Notes:
|
PE header info:
|
NOTE
**Custom-made exes and MSIs will have a different default installation path that includes an identifier.
Ex: C:\Program Files (x86)\AnyDesk-ad_679ecc64
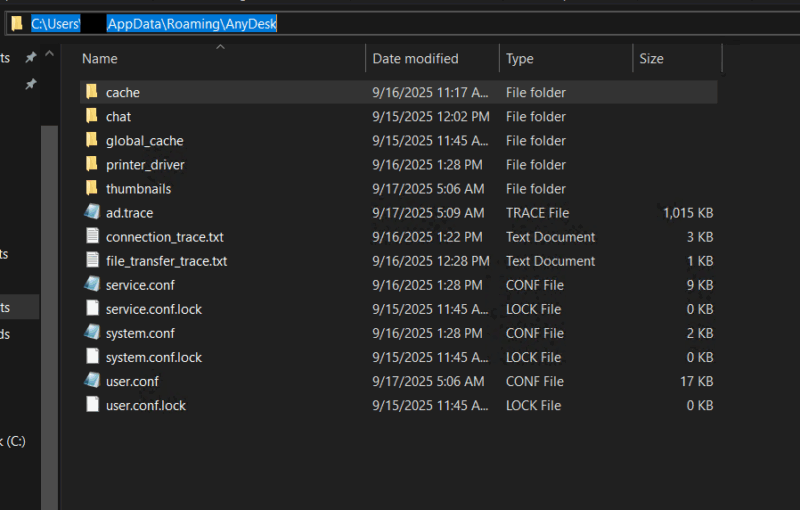
Config/Log Files
| User.conf |
|---|
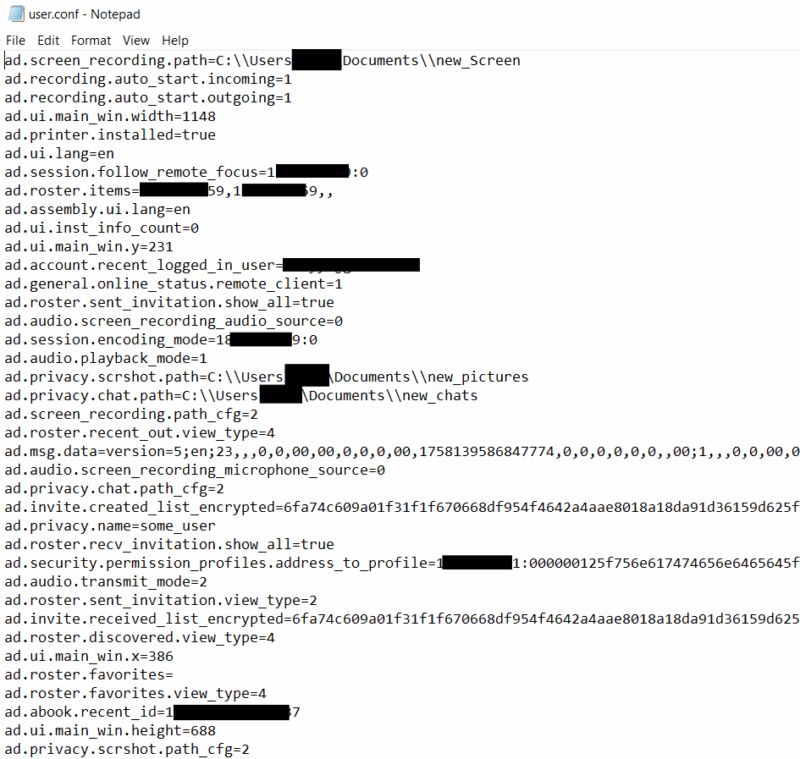
| Description: Contains user-specific configuration data for AnyDesk. Most of the AnyDesk settings that can be configured in the UI are stored here. |
Known path(s):
|
Notes:
|
| Example: |
| System.conf |
|---|
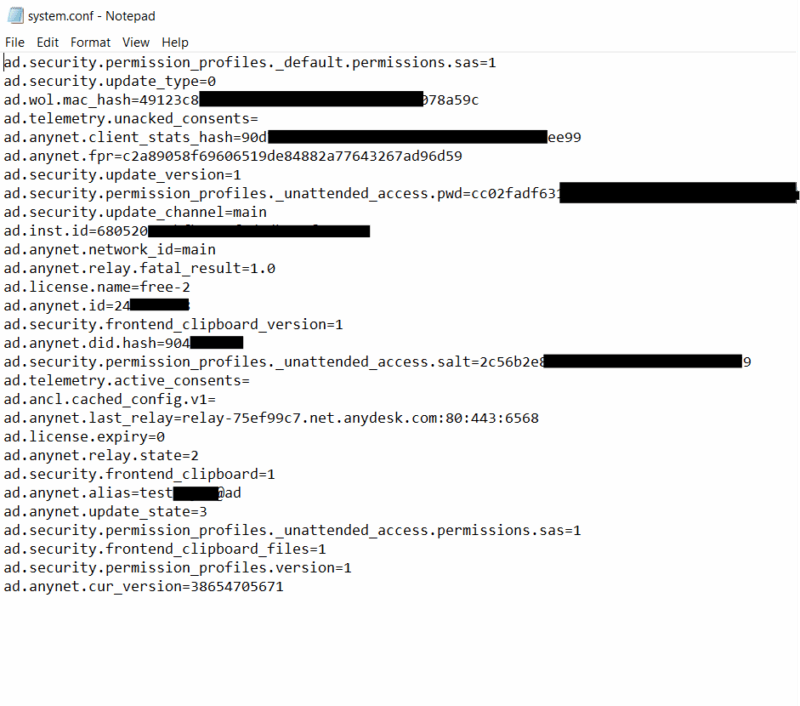
| Description: Contains system-specific AnyDesk configuration information. |
Known path(s):
|
Notable entries:
|
| Example: |
| Connection_trace.txt |
|---|
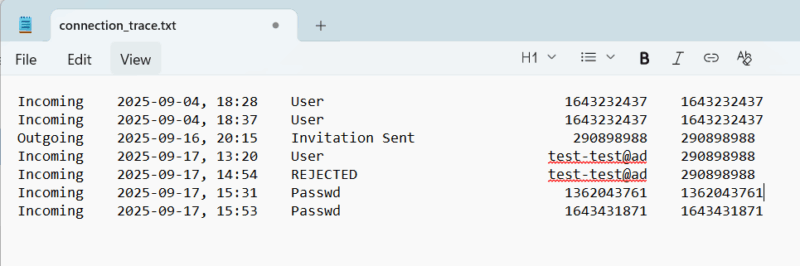
| Description: Contains information about when incoming connections have been accepted/rejected and when outgoing invites were sent. |
Known path(s):
|
Notes:
|
| Example: |
| File_transfer_trace.txt |
|---|
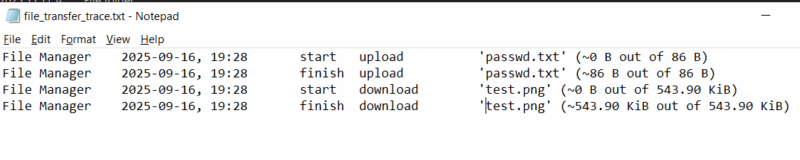
| Description: Contains information about files uploaded or downloaded to the system. File is generated on both sides of the connection and is only created or updated when a file transfer occurs. |
Known path(s):
|
| Notes: Log file only contains file names and not paths of files transferred. |
| Example: |
| Ad.trace/Ad*.trace |
|---|
| Description: Contains detailed application-level logging for AnyDesk to allow application troubleshooting. Data isn’t structured like other log files, so it’s not as straightforward to use. It does, however, contain a lot of useful information like remote IPs, AnyDesk IDs, connection times, files transferred, etc. |
Known path(s):
|
| Notes: Log file only contains file names and not the paths of files transferred. |
Folders
| AnyDesk Installation Folder |
|---|
| Description: Main folder where AnyDesk is installed. It contains a single file: AnyDesk exe. |
Known path(s):
|
| Notes: Folder creation date can indicate when AnyDesk was installed. |
| Session Recording Folder |
|---|
| Description: Contains session recordings for both incoming and outgoing sessions. This can be initiated manually during a session or configured to occur each time a session is started via settings. |
| Known path(s): C:\Users\*\Videos\AnyDesk |
Notes:
|
Examples:
|
| Screen Recording Folder |
|---|
| Description: Contains screen recordings performed locally from AnyDesk. |
| Known path(s): C:\Users\*\Videos\AnyDesk\screen recordings |
| Notes: Folder is created when AnyDesk starts up if it does not already exist. The folder creation timestamp can indicate the first time AnyDesk was run by a user. |
| Examples: screen_recording_20250904165730_0.anydesk |
| Screenshot Folder |
|---|
| Description: Contains screenshots taken during a remote session. |
| Known path(s): C:\Users\QA\Pictures\AnyDesk |
| Notes: Folder is created when AnyDesk starts up if it does not already exist. The folder creation timestamp can indicate the first time AnyDesk was run by a user. |
| Examples: anydesk00000.png |
Domains
| Subdomain | Details |
|---|---|
| https://download.anydesk.com/AnyDesk.exe | Default download link for AnyDesk. |
| https://download.anydesk.com/AnyDesk-CM.exe | Download link to an AnyDesk configured to only receive connections. |
| https://download.anydesk.com/AnyDesk-SM.exe | Download link to an AnyDesk configured to only initiate connections. |
| https://my.anydesk.com/v2/api/v2/custom-clients/downloads/public/GIDDDDDDWHH1/file_name.exe | Public download link used to download custom-made AnyDesk exes. Anyone with the link can download. |
| https://my.anydesk.com/v2/builds/download/952535/new%20file%20name.exe | Private download link to download custom-made AnyDesk exes. You need to log in to the associated account to be able to download. |
| relay-*.net.anydesk.com | Cloud infrastructure to download information and support remote connections. Ex: relay-c6eb91af.net.anydesk.com |
DFIR Next Steps: How to Investigate Suspicious AnyDesk Use
The goal of this section is to provide some investigative questions that should be answered to help determine if the AnyDesk activity on the system is expected.
4 we’ll review:
- Does the organization use AnyDesk?
- Is AnyDesk expected to be on the endpoint?
- What AnyDesk configuration is being used?
- Is the activity expected?
Now let’s dig into each:
| #1 Does the organization use Pulseway? | |
|---|---|
| Yes | Go to question 2 |
| No | Unauthorized AnyDesk tool found and should most likely be removed. Proceed to question 4 to determine the impact.
Ex: Did a threat actor bring it in, did a disgruntled IT administrator use it for nefarious activity, or was it an employee using it without bad intentions? |
| #2 Is AnyDesk expected to be on the endpoint? | |
|---|---|
| Yes | Go to question 3 |
| No | Unauthorized AnyDesk tool found and should most likely be removed. Proceed to question 4 to determine the impact.
Ex: Did a threat actor bring it in, did a disgruntled IT administrator use it for nefarious activity, or was it an employee using it without bad intentions? |
| #3 What AnyDesk configuration is being used? |
|---|
| Determine if AnyDesk is being used as a standalone instance, installed instance, or both. Installed instances are more likely to be legit and common within an organization, while standalone is more common for personal use or remote support scenarios. If both are found that may be another red flag to further investigate.
Indicators to look for installed version:
Indicators to look for portable version:
|
| #4 Is the activity expected? |
|---|
| There are a lot of subquestions that need to be answered to answer the bigger question of if the activity is expected.
Questions like:
|
How to Investigate Suspicious AnyDesk Use with Cyber Triage
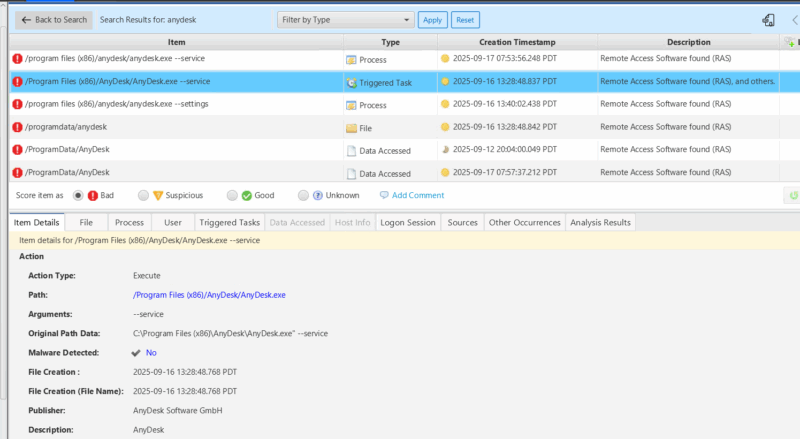
Cyber Triage can be used to find RMM tools like AnyDesk on systems without the need for analysts or responders to remember all of the various file names, folder paths, web artifacts, log files, or registry keys. That detection logic is built into Cyber Triage to automate this process so defenders can spend more time determining if the RMM tool activity is expected or not.
Cyber Triage will:
- Automatically collect AnyDesk-specific log and configurations files.
- Automatically detect AnyDesk indicators of existence on the system (along with over 40 other RMM products).
- Automatically provide insight into how long AnyDesk has been on the system based on the various indicators of existence previously mentioned. For example, you’ll be able to tell what the earliest and latest activity related to AnyDesk.
From there, analysts can follow the next steps outlined above to determine if the activity is expected or not.
We have had engagements where Cyber Triage has flagged 3 or 4 different tools on a single endpoint. Even if these are not a result of malicious activity, it can help to root out poor security practices and act as a preventative measure to better secure access to such devices.
If you’d like to try Cyber Triage on an RMM investigation — or just to see if it speeds up your process in general — you can free for 7 days.
AnyDesk References
- NCC Group: The Dark Side: How Threat Actors Leverage AnyDesk for Malicious Activities
- The DFIR Spot: AnyDesk – Investigating Threat Actors Favorite Tool
- Synacktiv: Legitimate RATs: a comprehensive forensic analysis of the usual suspects
- LOLRMM: AnyDesk
- iblue.team: AnyDesk Remote Access
- HatsOffSecurity: AnyDesk Forensic Analysis and Artefacts
- Tyler Brozek: AnyDesk Forensics | AnyDesk Log Analysis
- The DFIR Report: From OneNote to RansomNote: An Ice Cold Intrusion