Welcome back to the next post in our DFIR Next Steps series on remote monitoring and management (RMM) tools. This post will focus on Pulseway. Pulseway is a newer RMM that we have recently seen used by threat actors.
Check out our previous posts in the series:
- Overview of investigating suspicious RMMs
- Investigating suspicious TeamViewer use
- Investigating suspicious LogMeIn use
- Investigating suspicious AnyDesk use
Now, let’s analyze Pulseway!
Jump to…
Pulseway Overview
Pulseway DFIR Artifacts
What It Means: The Impact of Malicious Pulseway Use
What to Do Next: How to Investigate Suspicious Pulseway Activity
How to Investigate Suspicious Pulseway Use with Cyber Triage
Pulseway Overview
What is Pulseway?
Pulseway describes itself as “An IT Management Solution That You Can Take Anywhere,” with one of the key advertised features being the ability to manage endpoints from a mobile device.
Pulseway is an agent-based SaaS solution. One interesting/concerning feature of the agent is the ability to run a silent install, provided you have administrator access. This means that once a threat actor has access to the system, they could install Pulseway in order to maintain persistence without causing any notifications to the user.
From a threat actor’s perspective, the SaaS side of things makes Pulseway a less attractive option, as logs are retained on the Pulseway server and traces of their actions will be recorded (more on that later).
Pulseway Features
The feature list is too big to list here, but we will include some significant remote features relevant to incident response.
These include:
| Feature | Notes |
|---|---|
| Remote access | Via Pulseway remote console or starting an RDP session. |
| Remote execution | Both CMD terminal and PowerShell. |
| Remote stopping/starting of processes and services | Includes terminating EDR and other security products. |
| Automation scripts | If looking to deploy ransomware, this would make it easy. |
| Remote file viewing and copying | |
| Registry viewer | |
| Application installation | |
| Remote screen viewing | With no notification to the user |
Note
*In addition to the capabilities above, Pulseway provides a wide range of fleet management functionality from reporting to configuration and patch management, along with some endpoint security provided via integrations with Webroot, Bitdefender, and “Ransomware Detection” available as add-on subscriptions.
Why We’re Interested
Our interest in Pulseway was sparked following a request from a customer who had experienced a cyber incident in which the threat actor had used Pulseway for remote access to compromised systems.
With that being said, Pulseway does not appear to be a popular tool yet, with very few references in incident write-ups or threat reports.
Pulseway DFIR Artifacts
Key Files and Paths
Pulseway is installed in %Program Files%\Pulseway, the default install (at time of testing) created 101 files, 5 folders, and used 57MB.
Some of the key files are:
| Key File | Value |
|---|---|
| C:\Program Files\Pulseway\PCMonitorManager.exe | Management GUI for the local application. Requires administrator permissions via UAC. |
| C:\Program Files\Pulseway\PCMonitorSrv.exe | Main agent, installed as a service named “PC Monitor” |
| C:\Program Files\Pulseway\PCMontask.exe | Pulseway User Agent, launched by PCMonitorSrv.exe |
| C:\Program Files\Pulseway\pcmonusertask.exe | Pulseway User Task Agent, launched by PCMonitorSrv.exe |
Persistence
Persistence is maintained via the PC Monitor service and a scheduled task – “PulsewayServiceCheck” – that runs daily and calls a batch file to check if the PC Monitor service is running, and starts it if it is not.
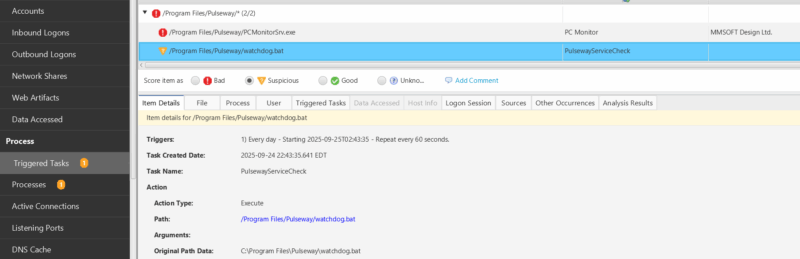
Configuration
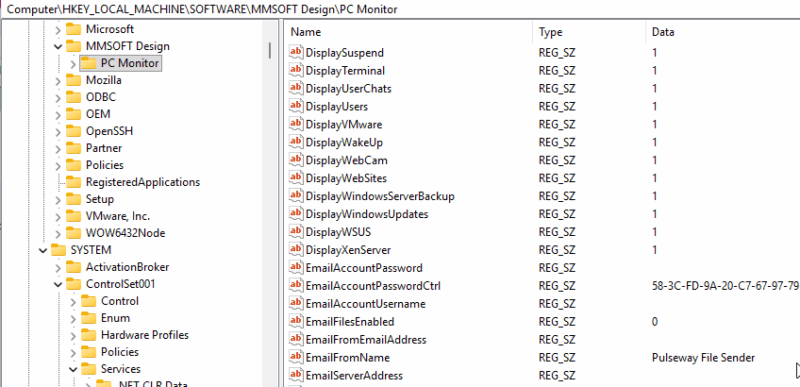
Most configuration appears to be maintained in a single registry key: \HKLM\SOFTWARE\MMSOFT Design\PC Monitor
This appears to contain subkeys for most of the application settings, including keys referencing passwords. Note that researching the values of these keys was beyond the scope of this research.
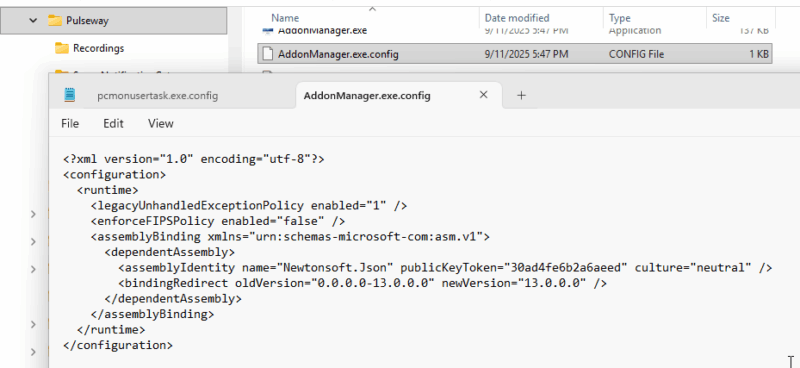
In addition to the registry entries, there were a number of *.config files containing XML data for various executable files. The .config files are named after the .exe files.
Log Files
Pulseway uses two event logs for recording activity: the Windows application log and the “Pulseway-CommandAudit” log.
The Pulseway Command Audit log can be found at %SystemRoot%\System32\winevt\Logs\Pulseway-CommandAudit.evtx
All events (in both logs) are recorded as event ID 24001.
Application Log
The Application log records both remote access to the system and standard operating information. Unfortunately, as the same Event ID is used for all Pulseway records, it is necessary to search the record data for significant events.
These include:
| Example Log Data | Description |
|---|---|
| Received Request Start Remote Control RC | A remote connection was requested. This record will include the GUID of the requesting host. |
| Received Request Get screens from device Id:
‘1-f43fbae6-34d9-4e8e-b64a-4c1aec36b9d9’ |
Remote viewing of current screens. |
| Received Request Run command:
‘see fb472da4-6dbf-44cb-b052-a86127d68b88 in Pulseway-CommandAudit log’ from device Id: ‘1-f43fbae6-34d9-4e8e-b64a-4c1aec36b9d9’ |
A remote command was executed. Note that the command itself is not displayed in the application log. It can be found in the Command Audit log, by cross-referencing the supplied GUID. |
| Received Request Run PowerShell command:
‘see 16535d8d-e03c-4e49-b5c1-dadbe638d431 in Pulseway-CommandAudit log’ from device Id: ‘1-f43fbae6-34d9-4e8e-b64a-4c1aec36b9d9’ |
A remote powershell command was executed, as with the “Run command” the command itself will be saved to the Command Audit log. |
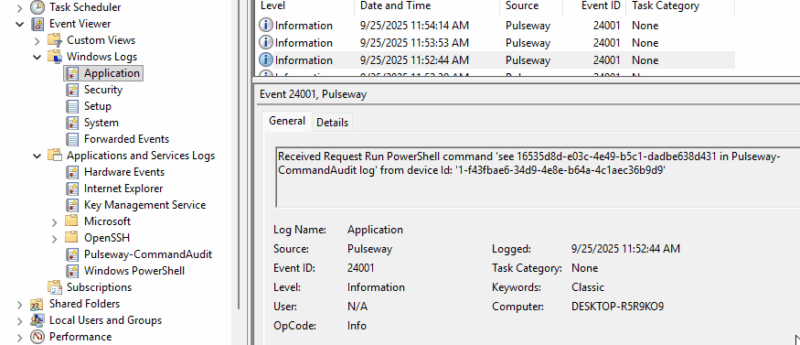
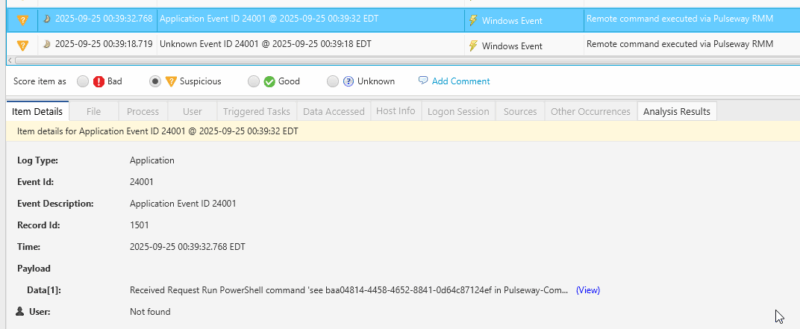
Command Audit Log
Entries in the command audit log will include the commands or PowerShell cmdlets run from the management console.
An example is shown below:
Arguments for 57e457d5-23fd-46d8-9c44-4719def4c499: ‘netstat’
Domains
When a pulseway account is created, a subdomain of pulseway.com will be created using the domain of the registered email address.
In our example, that was reynholmenterprises.pulseway.com.
| Remote Access Domains |
|---|
|
What It Means: The Impact of Malicious Pulseway Use
Pulseway is a powerful RMM tool. Once installed, a remote user has complete control of the compromised system. They are able to perform more actions than a locally logged-on Administrator can, as the remote PowerShell and command execution is run as the SYSTEM user.
Because the PowerShell commands are run as the SYSTEM user, the PowerShell console log is not updated, and PowerShell commands are not logged to the PowerShell event log. However, they will appear in the Pulseway Command Audit Log.
Other remote commands – for example, downloading of files – also leave no trace on the target system other than entries in the Command Audit log.
What to Do Next: How to Investigate Suspicious Pulseway Activity
The goal of this section is to provide some investigative questions that should be answered to help determine if the Pulseway activity on the system is expected.
We’ll review:
- Does the organization use Pulseway?
- Is Pulseway expected to be on the endpoint?
- What commands were executed with Pulseway?
- Is the activity expected?
Now let’s dig into each:
| #1 Does the organization use Pulseway? | |
|---|---|
| Yes | Go to question 2 |
| No | Unauthorized Pulseway tool found and should most likely be removed. Proceed to question 4 to determine the impact. Ex: Did a threat actor bring it in, did a disgruntled IT administrator use it for nefarious activity, or was it an employee using it without bad intentions? |
| #2 Is Pulseway expected to be on the endpoint? | |
|---|---|
| Yes | Go to question 3 |
| No | Unauthorized Pulseway tool found and should most likely be removed. Proceed to question 4 to determine the impact. Ex: Did a threat actor bring it in, did a disgruntled IT administrator use it for nefarious activity, or was it an employee using it without bad intentions? |
| #3 What commands were executed using Pulseway? |
|---|
|
| #4 Is the activity expected? |
|---|
| There are a lot of subquestions that need to be answered to answer the bigger question of if the activity is expected.
Questions like:
|
How to Investigate Suspicious Pulseway Use with Cyber Triage
Cyber Triage will score the existence of Pulseway as suspicious. Cyber Triage will also collect the application log, which can be extracted from the collection for deeper analysis.
Another option is to write sigma rules to score Pulseway log entries as suspicious and a file collection rule to collect the Pulseway-CommandAudit log.
The next release of Cyber Triage will include rules for scoring Pulseway event log entries and collecting the Command Audit log.
If you’d like to try Cyber Triage on an RMM investigation — or just to see if it speeds up your process in general — you can free for 7 days.
