Cyber Triage 3.15 is about making SOCs faster:
- Directly import Defender telemetry for faster endpoint triage after an alert.
- Push results to DFIR IRIS to more quickly centralize findings.
- Restrict access to sensitive incidents to key personnel.
- Easily update server settings without a restart.
If you want to try the latest version of Cyber Triage so you can have more automated investigations, use this link.
Endpoint Triage with Defender EDR Telemetry
After an alert has been validated, SOC teams need to perform endpoint triage on the host to understand what happened before the alert. Windows Defender for Endpoint (and other EDRs) has historical data that could be critical to that investigation, but using this data is complicated within EDR consoles.
Now Cyber Triage can directly import Defender data, so you can quickly find what happened before the alert using your collection and Defender’s data.
With the Defender import feature, this is a SOC team’s process after an alert:
- Alert triage: Confirm the alert is valid.
- Import data into Cyber Triage: Start an investigation and import data directly from the API.
- Normalization: Cyber Triage automatically maps the Defender data to its investigation data model.
- Scoring: Cyber Triage automatically analyzes the artifacts and scores them as bad or suspicious.
- Assisted examination: Analyst reviews the data in Cyber Triage to look for data exfiltration, lateral movement, and other forms of remote access.
An example is shown here for a process retrieved from the Defender Hunt API. The “Sources” tab shows where it came from:
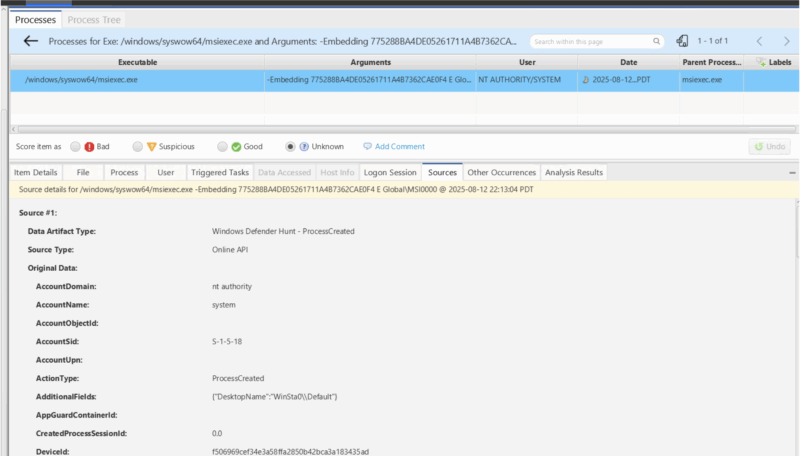
This feature is not enabled in Cyber Triage by default. Contact sales for more information.
You can see this feature at our Sep 11 webinar.
Push Results into DFIR IRIS
Some DFIR teams use DFIR IRIS to manage their cases.
It can be used to:
- Manage tasking.
- Correlate findings with past cases.
- Merge findings from multiple tools to create a final report.
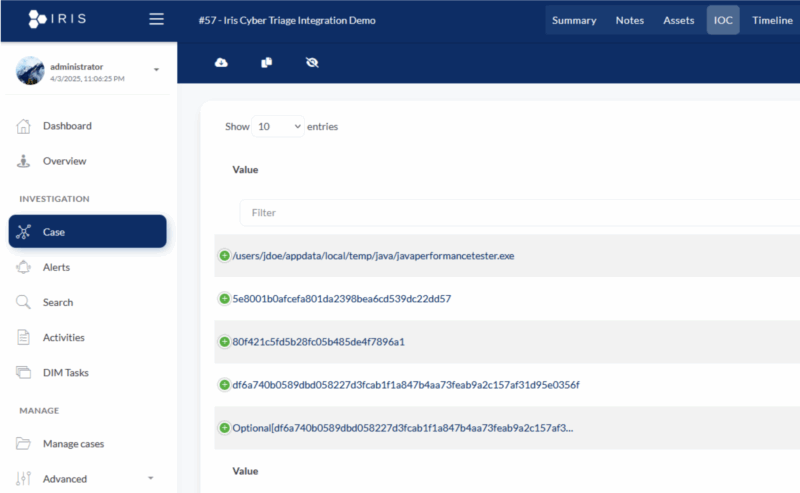
Cyber Triage can now push results directly into DFIR IRIS.
They are shown in:
- Incident timeline
- IOCs
This saves time and errors, ensuring findings are quickly centralized for teams.
This feature is not enabled in Cyber Triage by default. Contact sales for more information.
Restrict Access to Incidents
Cyber Triage can now limit who can view sensitive incidents.
This is important in these deployments:
- Enterprise
- Law enforcement
When making an incident, you can choose to allow everyone to see it, or you can choose to restrict it to only those who need to know.
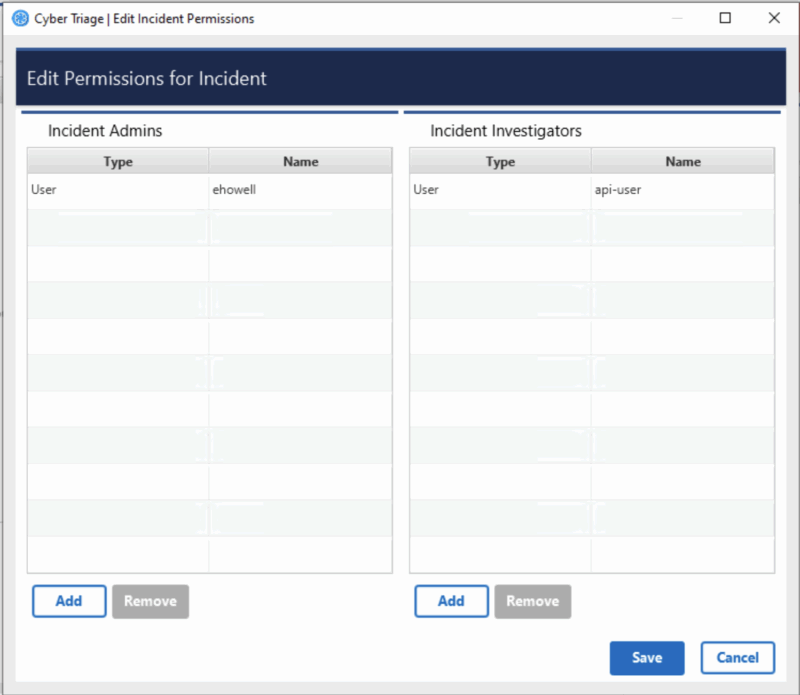
This feature is not enabled in Cyber Triage by default. Contact sales for more information.
Easier Server Administration
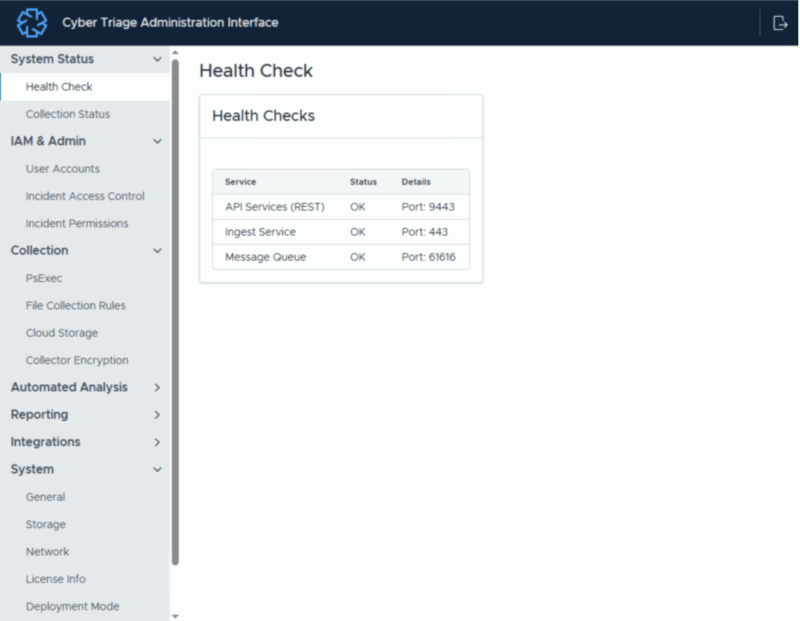
When deploying the Cyber Triage Team Server as a Windows service, you can now make changes without requiring a restart. The web app-based administration interface has been expanded to support all of the server settings.
So, now you can just connect with a web browser, enter your administrator credentials, make changes, and review status.
Try 3.15 Out
Cyber Triage 3.15 is built to make your investigations faster and more comprehensive.
If you’d like to see it in action for yourself, try it for free today.
