Cyber Triage 3.11 is out and the main theme is ‘more access’ with a special focus on disk images. Cyber Triage can import data from both live systems, other DFIR collectors, and full disk images (or virtual machines). This release has some long requested features to access more disk image data and to export more data.
This post dives into some of the new key features, but the Release Notes has the full list. We’ll cover:
- Decrypting BitLocker
- Ability to read all files from a disk image
- Expanded file explorer view
- Exporting all files
We’ll be hosting a webinar on July 10 at 1PM Eastern to see these features in action. You can sign up here.
You can download the latest installer from here.
Decrypt BitLocker Disk Images
Cyber Triage can now decrypt BitLocker disk images without the need for a 3rd party mounting tool. BitLocker is increasingly common, even if its password is stored in plaintext on the drive, called the clear key.
We added support into The Sleuth Kit to identify and decrypt BitLocker. While the Cyber Triage use of this feature is out now, we will release a new Sleuth Kit and Autopsy this summer with the same capability.
To use this feature, simply:
- Point Cyber Triage at a disk image (like in previous versions)
- Cyber Triage will detect that it has BitLocker encryption and attempt to find the clear key
- If a password or recovery key is needed, Cyber Triage will prompt you for it
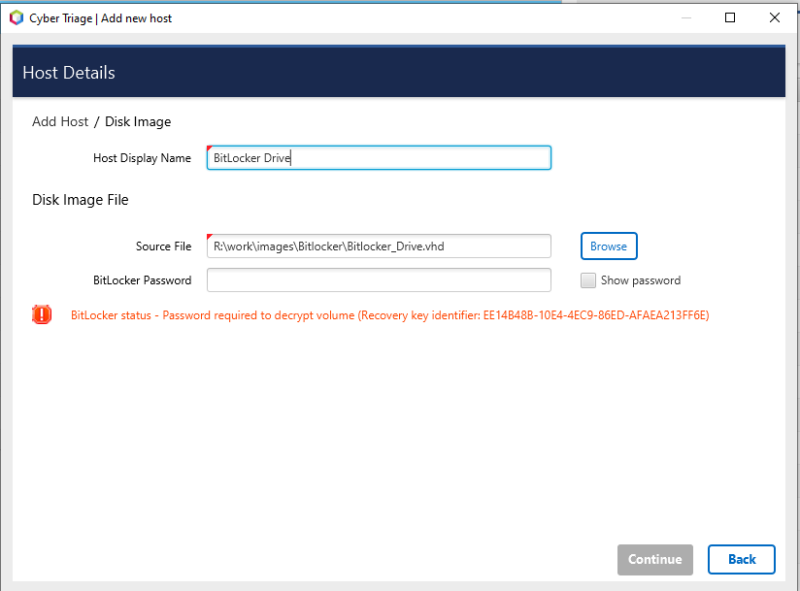
Cyber Triage will store the password so that the drive can continue to be accessed in the future as the investigation progresses.
Access Any Files in a Disk Image
The second disk image related feature in 3.11 is about being able to access all files when you import a disk image. Historically, you could easily access the “priority” files that were part of the triage collection, such as executables for startup items or recent web downloads. Now, if the disk image is still available, you can access any file.
For a bit of context on why this behavior existed, Cyber Triage treats a disk image similar to a live host. To quickly process the image, it focuses on the data that it thinks is most relevant to an intrusion. It will extract copies of the key executables from the disk image and store them inside of the Cyber Triage folders (just like it does for live systems).
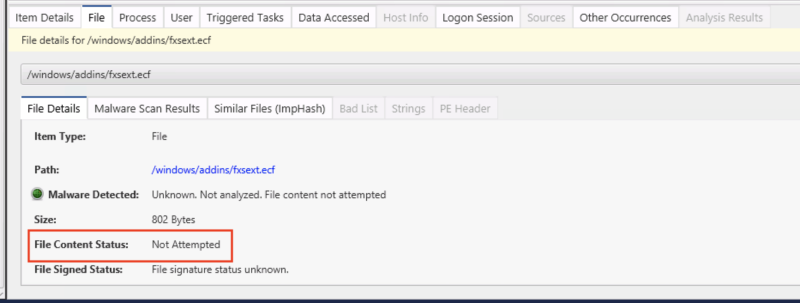
Before 3.11, if you wanted to do a deeper dive investigation into a disk image, you may see a “Not Attempted” message such as this for a non-priority file on the “File Content Status”:
In 3.11, Cyber Triage will go to the disk image to access these files and the “Item Details” panel will show you “Available” instead:
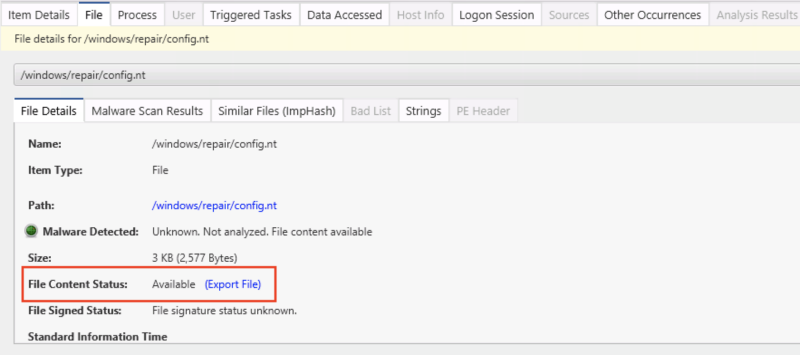
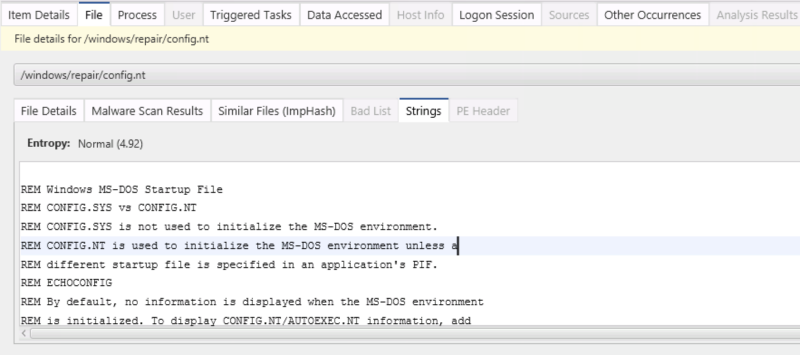
You can then export this file or view the contents in the “Strings” viewer.
Expanded File Explorer View
Cyber Triage has always had a basic file explorer view. Our main priority has always been to make sure you can get easy access to the artifacts. But, as Cyber Triage has moved beyond just a triage tool, we’ve had more requests to make file navigation easier.
3.11 has three changes to make it easier for you to see what other files there are on the system:
- When you select “Files”, we will show you the file explorer versus just the suspicious files
- There is a tree panel on the left showing directories
- There are more columns shown within the directory
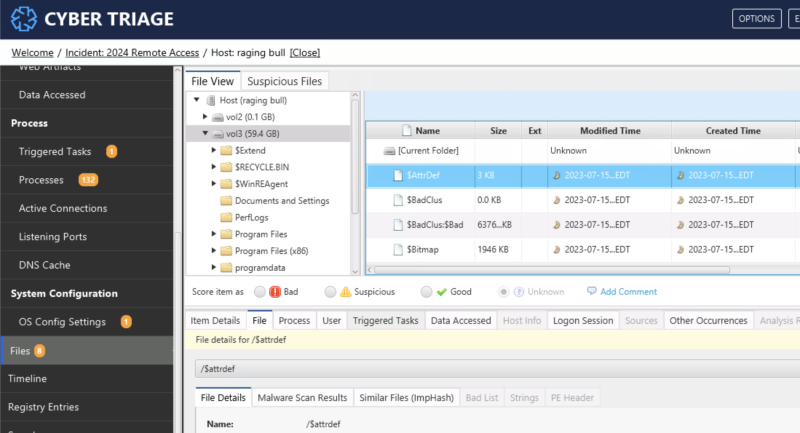
These changes, combined with access to all disk image files, means that a more in-depth investigation can be performed within Cyber Triage.
Export All Collected Files
The last of the commonly requested features is that you can now export all collected files with a new report module. The primary use case for this feature is to be able to use additional tools besides Cyber Triage for your analysis.
One source of this request is from people who want to use the Cyber Triage Collector to ensure they get as many files as possible from a live system. The adaptive Cyber Triage Collector will parse registry hives and other files to go beyond a static list of files to collect. It will also collect the executables and other files that artifacts reference.
But, the Collector’s output is a JSON file that not all other tools support. With this feature, you can collect with the Collector and then choose the new “All Collected Files in a ZIP” report module.
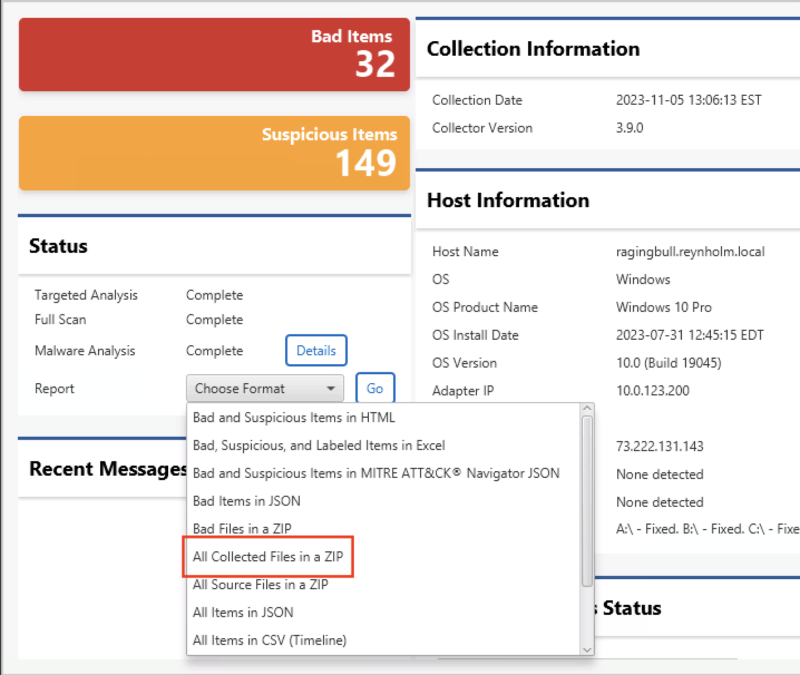
This will create a ZIP file for you with all of the thousands of collected files.
After the export is complete, you have a full folder structure of the exported files.
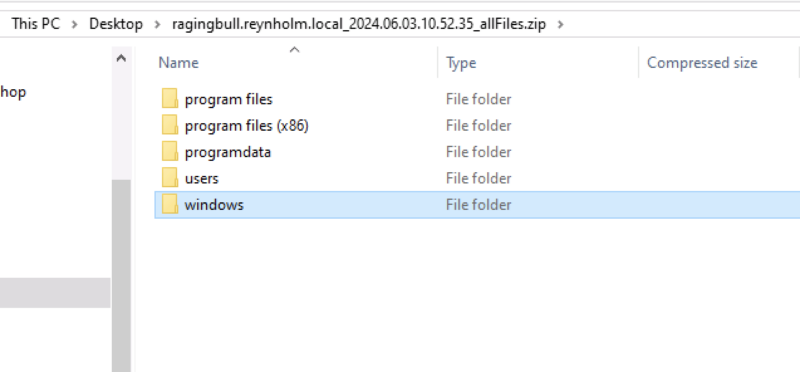
Be careful extracting this folder though since it may contain malware and some ZIP extraction tools do not deal well with long file paths (such as the default Windows extractor).
Access More Files Today
Our goal is always to make sure you can quickly get to the data you need for your investigations. If you are looking for a tool to allow you to go from triage to deep dive with a disk image or other data set, then make sure you try out the latest version. You can download it from the form here.



