Key insights for your investigation found in one place! An overview into Windows Registry Forensics and how to leverage data for your investigations.
Jump to…
Introduction
Registry Basics and Structure
Registry Files and Their Forensic Value
Tools for Registry Forensics
Windows Registry Forensics with Cyber Triage
Keep Learning Registry Forensics
Introduction
The Windows registry is a central database that is leveraged by the operating system and many applications to store all sorts of configuration information and user preferences.
Leveraging data from the registry can provide key insights to an investigation that may not be found in other artifacts. A few of the key areas of focus are:
- User activity (program execution, files and folders accessed, urls types, and much more!)
- System configuration (OS information, hostname, timezone, adapter settings, network configuration, audit policy, and much more)
- Installed applications
- Attached storage devices
- Malware persistence
If you are looking to dive straight into key forensic artifacts from the registry check out one of our previous blog posts!
Registry Basics and Structure
What Is the Windows Registry?
A hierarchical structured database used by the system and applications to store configuration data, state information, usage telemetry, and more.
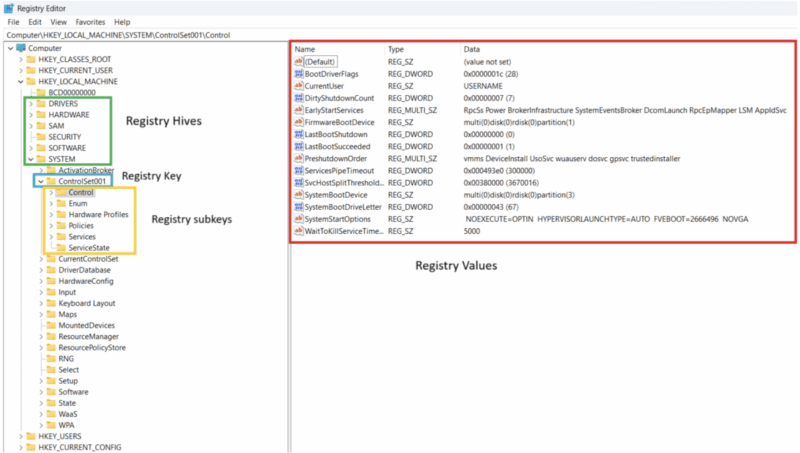
The following are key concepts related to the Windows Registry:
| Concept | Notes |
|---|---|
| Registry Files | REGF formatted binary files used to store registry data.
Ex. C:\windows\system32\Config\SOFTWARE |
| Transaction Logs | Multiple REGF formatted files that record changes to the registry before writing to the registry files. This ensures data can be recovered in case of an error.
Must be reviewed when registry files are “dirty” – uncommitted changes exist in the transaction log. Read more about transaction logs here. Ex. C:\windows\System32\Config\SOFTWARE.LOG1 |
| Registry Hives | Logical grouping/view of registry data loaded in memory.
Ex. HKLM\Software |
| Keys | Named “folder” like objects that contain last write timestamps, subkeys, and values. |
| Subkeys | A key that is stored under another key, making a hierarchical structure. |
| Values | Can hold arbitrary data and are made up of several components:
|
| Last Write times | A timestamp that records when a registry key was last updated. Updates to a key are represented by values added/modified/deleted to a key or subkeys added/renamed/deleted from a key.
These timestamps are often used in timelines to better understand activity that has occurred in the registry. |
Where can you find registry data
Registry data is stored in several places on the system.
- Memory
- Disk – registry file
- Disk – transaction logs
Memory: System specific registry hives are loaded into memory on system startup and user specific registry hives are loaded each time a user logs onto the system. The memory view of the registry is the most up to date and current view, however, not all registry data will be found in memory. For example you may have 10 users on a system and if only 1 user is logged on then only that users specific registry hives will be in memory. The other users registry data will only be found on disk.
Disk: The registry, as it exists on disk, is a bit more complex as the data may be broken up among multiple files: the primary registry file and the transaction log files. The primary registry files contain the bulk of the registry data whereas the transaction logs contain recent changes that have yet to be committed to the primary file. As a result, both files need to be analyzed to get a full picture of the registry hive when not loaded in memory.
Changes are made to the in memory version of the registry and are written to transaction logs and the on-disk registry files on periodic intervals or when a hive is unloaded (ex. user logoff/system shutdown). To get a better understanding on when changes are flushed from memory to transaction log and finally primary registry files check out this helpful resource.
| Key locations for registry data on disk | |
|---|---|
| System related registry files |
C:\Windows\System32\Config
|
| User based registry files |
C:\Users\<Username>\
C:\Users\<Username>\AppData\Local\Microsoft\Windows\
|
| App based registry files |
%LOCALAPPDATA%\Packages<PackageFamilyName>\SystemAppData\Helium\
|
| AmCache registry files |
C:\Windows\AppCompat\Programs\
|
Primary Registry Hives and Their On-Disk Locations
These files are stored on disk and loaded into memory when the system boots or a user logs in. They are often the source files examined during forensics. Note this is not an exhaustive list of every registry hive, just the highest value ones.
| Hive | Description | On-Disk Path |
|---|---|---|
| HKLM\SOFTWARE | Installed software and system-wide settings. |
C:\Windows\System32\Config\SOFTWARE |
| HKLM\SYSTEM | Hardware configuration, control sets, services. |
C:\Windows\System32\Config\SYSTEM |
| HKLM\SECURITY | Local security policy and audit settings. |
C:\Windows\System32\Config\SECURITY |
| HKLM\SAM | Local user accounts and group membership. |
C:\Windows\System32\Config\SAM |
| HKU\{SID} | User-specific settings and activity. |
C:\Users\<Username>\NTUSER.DAT |
| HKU\{SID_Classes} | User class information (shell settings, application history). |
C:\Users\<Username>\AppData\Local\Microsoft\Windows\UsrClass.dat |
| User.dat (Not part of the Windows registry) | Tracks the same data as NTUser.dat except done within the context on an MSIX app. |
%LOCALAPPDATA%\Packages\<PackageFamilyName>\SystemAppData\Helium\User.dat |
| UserClasses.dat (Not part of the Windows registry) | Tracks the same data as UsrClass.dat except done within the context on an MSIX app. |
%LOCALAPPDATA%\Packages\<PackageFamilyName>\SystemAppData\Helium\UserClasses.dat |
| Amcache (Not part of the Windows registry) | Application installs, driver installs, and PE file information. |
C:\Windows\AppCompat\Programs\Amcache.hve |
NOTE
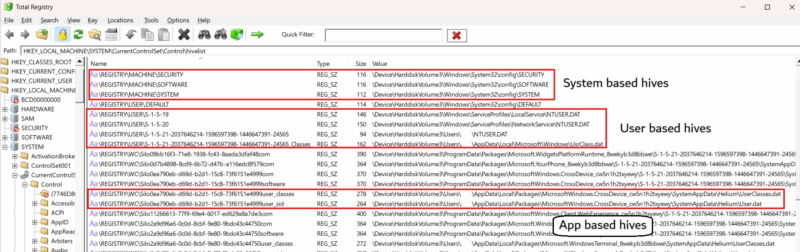
On live systems, you can see where hives are mounted by looking at the key HKLM\SYSTEM\CurrentControlSet\Control\hivelist. This key can only be found on live systems because it’s a volatile key and only exists in memory.
Registry Files and Their Forensic Value
We will be touching on a few key registry hives and some of their most popular artifacts. For more thorough breakdowns check out our Registry Forensics Cheatsheet and NTUSER.dat forensic analysis blogs.
| NTUSER.DAT | |
|---|---|
| UserAssist (guide) | Provides evidence of execution for .lnk files or PE files that have a GUI component. |
| RunMRU (guide) | Provides evidence of execution for the last 26 commands typed by a user in the Windows run dialog box. |
| OpenSaveMRU (guide) | Provides evidence of data access by recording the last 20 files accessed via an Open/Save dialog per extension. |
| OfficeMRU (guide) | Provides evidence of files accessed specifically through an office product (ex. Word, powerpoint, excel). |
| Shellbags (guide) | Provides evidence of folder existence and in certain scenarios folder accessed. Archive file references can be found here as well.
NOTE: Will only contain data for files/folders accessed via the network. Normal file/folder access is record in UsrClass.dat. |
| TypedPaths | Provides an ordered list of the last 26 paths typed into the File explorer address bar. Url1 represents the most recently typed path. |
| MountPoint2 | USB devices and network shares that the user has had access to. |
| UsrClass.dat | |
|---|---|
| Shellbags (guide) | Provides evidence of folder existence and in certain scenarios folder accessed. Archive file references can be found here as well. |
| MUICache (guide) | Tracks program execution for apps with a GUI component. |
| SYSTEM | |
|---|---|
| ShimCache (Guide) | Used to track app compatibility info. Can prove file existence and sometimes file execution. |
| Activity Moderator (BAM/DAM) | Used to track apps that run in the background or are used during various low-power usage scenarios. |
| Mounted Devices | Used to map drive letters to attached devices. |
| Enum USB/USBSTOR | Used to get a list of attached USB device history: vendor ID, product ID, serial #, first and last attached times. |
| Windows Services | Contains info on all installed Windows services, including system drivers. |
| System configuration details | Time zone, computer name, last shutdown time, network interfaces, and network history. |
| SOFTWARE | |
|---|---|
| Application and OS Settings | System-wide installed applications:
Scheduled Tasks (Guide):
System-wide Autorun entries:
|
| Amcache.hve (blog) | Includes information on installed applications, drivers, and certain PE files (SHA1 hash and PE header info). |
Check out the following resources if you are interested in diving deeper into the registry artifact rabbit hole:
- RegSeek: A repository of registry artifacts with a UI to make finding registry artifacts easier.
- RegRipper4: Popular registry parsing tool, by Harlan Carvey, with an extensive list of registry parsing plugins.
- RECmd: Popular registry parsing tool, by Eric Zimmerman, with an extensive list of registry parsing artifacts scripted out. One example is Kroll_Batch with over 100 keys parsed out of the NTUser.dat hive.
Tools for Registry Forensics
There are many options available to interact with registry data. We will touch on some of the most popular options for interacting with the registry. If you want a deeper dive check out our Registry Forensics Tool Guide.
Parsing registry from memory:
Accessing live registry (running system):
- Using PowerShell cmdlets.
- Using Windows APIs.
- Using command line tools like reg.
- Using Regedit.exe or other GUI tools like Total Registry.
Parsing registry files:
- RegRipper4: Tool to automate the parsing of registry hives. Has a large library of pre-built plugins to extract forensic artifacts and allows yara scanning of hives
- Registry Explorer: GUI tool for viewing registry files. Has a large prebuilt list of bookmarks and parsers for common forensic artifacts to help speed up investigations
- RECmd: Similar to regripper, it automates the parsing of registry hives to pull out key forensic artifacts of interest.
- Plaso: Has a registry parsing plugin that parses a hand full of artifacts from the registry to put into a timeline
Windows Registry Forensics with Cyber Triage
Cyber Triage automates the collection of registry hives as well as the parsing of key artifacts from those hives. We also score items of interest to help reduce noise so analysts can focus on higher value data. This means less time worrying about remembering where data is and more time figuring out what happened.
| Some of the key artifacts we pull from the registry are | |
|---|---|
| Evidence of process execution | RunMRU, UserAssist, Bam/Dam, ShimCache and MUICache. |
| Evidence of data accessed | Open/Save MRU and Office recent files. |
| Evidence of persistence | Autorun keys (Ex. run/runonce), Services, Scheduled Tasks, and newly created user accounts. |
| Evidence of lateral movement | Mountpoint2 (network shares), Terminal Server Client (outgoing RDP). |
| OS Configuration information | Hostname, Adapter addresses, Install date, Product name, OS version, security audit settings, and Timezone information. |
Cyber Triage maps data artifacts like UserAssist and MUICache to Information artifacts (higher level grouping) like Processes. We do this because we believe reviewing information artifacts is easier to understand than having to know the context around each data artifact. You can read more about this approach here.
For example if you wanted to know what are all of the binaries that are in persistence locations on a system you could review triggered tasks instead of having to review autoruns outputs, scheduled tasks, services, etc…
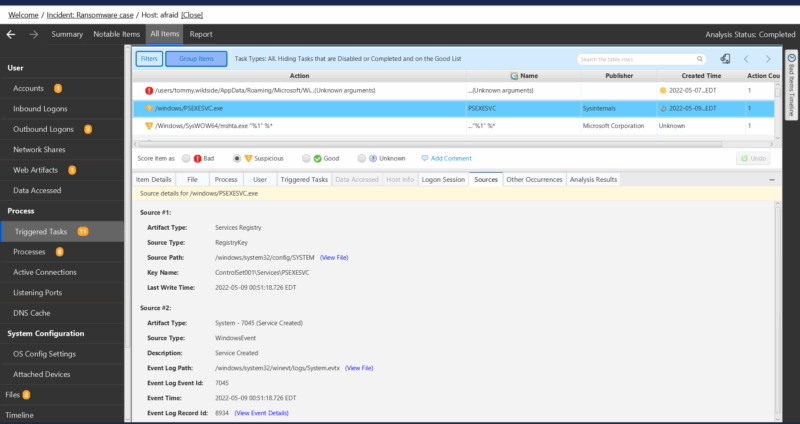
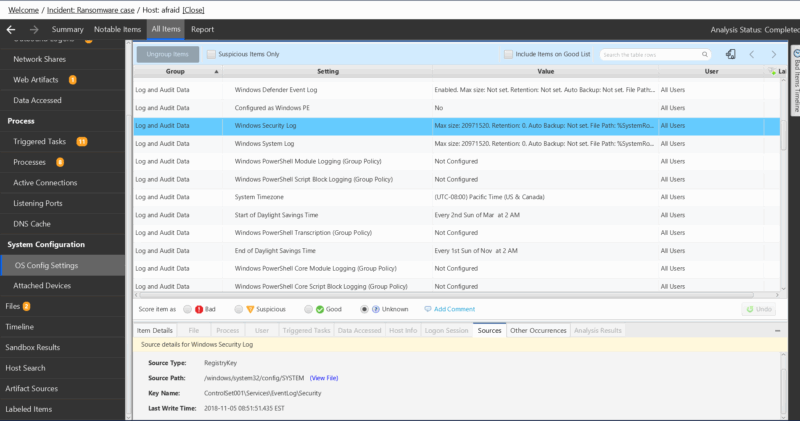
Another example would be if you want to know what audit policies are enabled on a host to better understand why data might be missing you would review OS Configuration Settings instead of reviewing each registry key that could be of interest.
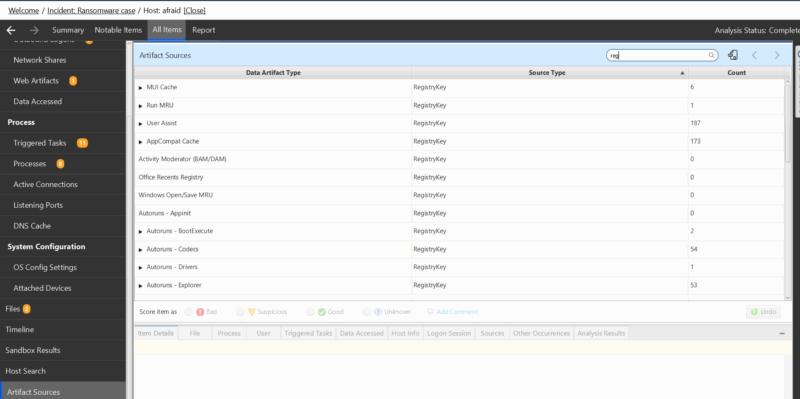
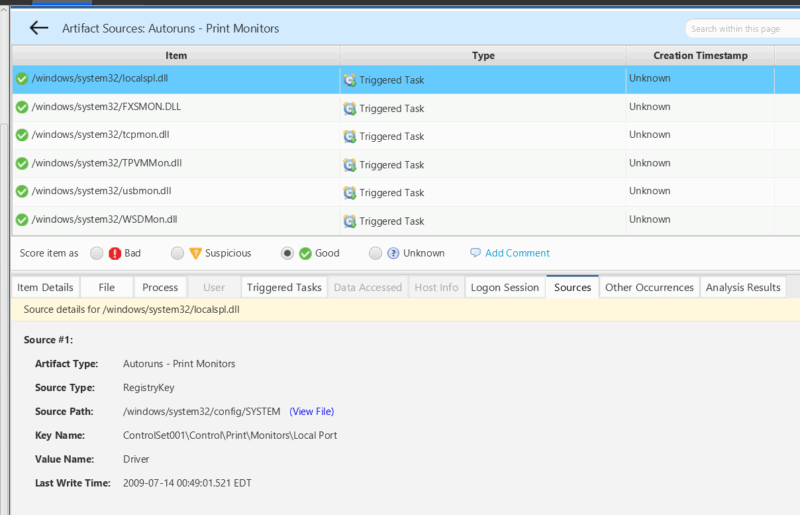
However, if your process involves looking at a specific data artifact like runmru or prefetch then we make that easy for you as well. The Artifact Sources table will break down all of the data artifacts that Cyber Triage processes. Clicking into a data artifact will then display all of the information artifacts created from that data artifact.