Cyber Triage 3.14 is out, and it’s HUGE!
- New UIs to help you quickly understand the host.
- Hayabusa integration to get more application-layer scoring and Sigma.
- Baseline feature to suppress false positives from gold images.
- Collector updates for public key encryption.
- Scoring changes so that you can mark something as “Unknown” instead of “Good.”
- Ability to set a reference date if it’s an old incident.
- Standard Pro malware limits are now weekly instead of daily.
As usual, we’re going to dive into these features here, but your other options are:
- Sign up for the webinar on May 15 at 1PM.
- Read the full release notes.
- Download the evaluation copy here.
New UIs to More Quickly Orient
The first change you’ll see in Cyber Triage is when you open the host. We describe some of the changes below, you can also view a video of the changes on YouTube.
Top-level Navigation
First, there is a new top-level navigation:
These represent the phases that we teach how to perform an investigation:
- Summary: Get a basic orientation of the system being investigated.
- Review Notable Items: Review what Cyber Triage scored as bad or suspicious with its automated analysis pipelines.
- Examine All Items: Dive deeper into all of the artifacts that were collected.
- Report: Make a report for other examiners or systems.
We’ve moved some of the views around so that they are now in the order that we expect you to use them. Start in “Summary,” then to go “Review Notable Items,” etc.
MITRE ATT&CK Tactics
Within the “Summary” section, there is a new view that will show you the items scored as “Bad,” organized by their MITRE ATT&CK mapping. This will help you more easily identify which phases of an attack were identified.
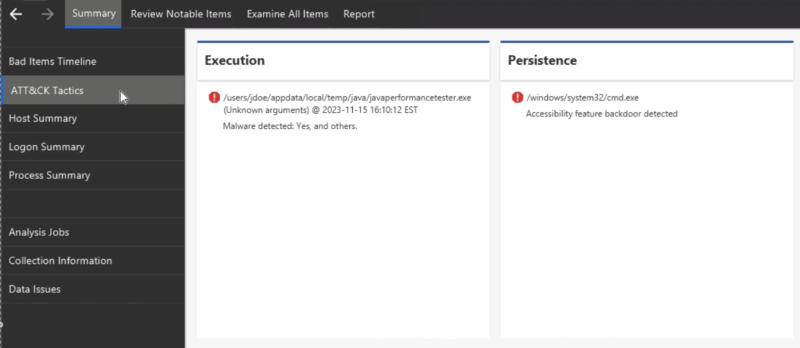
For example, you can look for the Data Exfiltration heading to look for signs of that.
Review Notable Items with Filters
The 2nd major phase of an endpoint triage is to review what items Cyber Triage automatically scored as bad or suspicious. We used to have two views for this (one for bad and one for suspicious). We’ve now merged them and sorted by time.
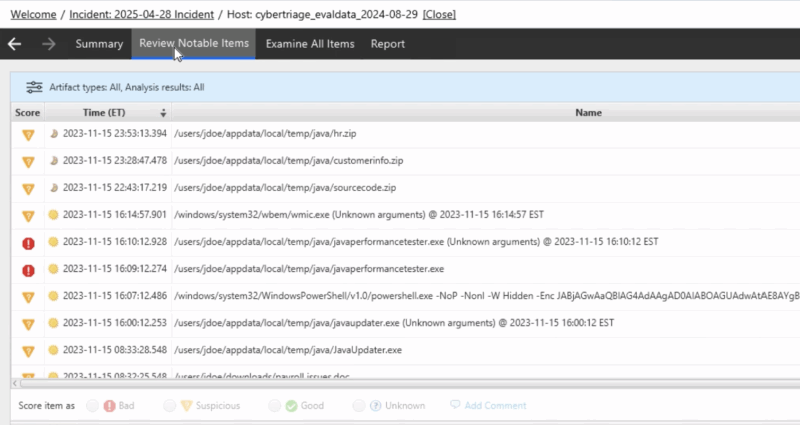
This new view makes an investigation easier because:
- Time is critical to get contact about if something is a false positive or not.
- We’ve added filtering to make it easier to focus or ignore a certain type of result.
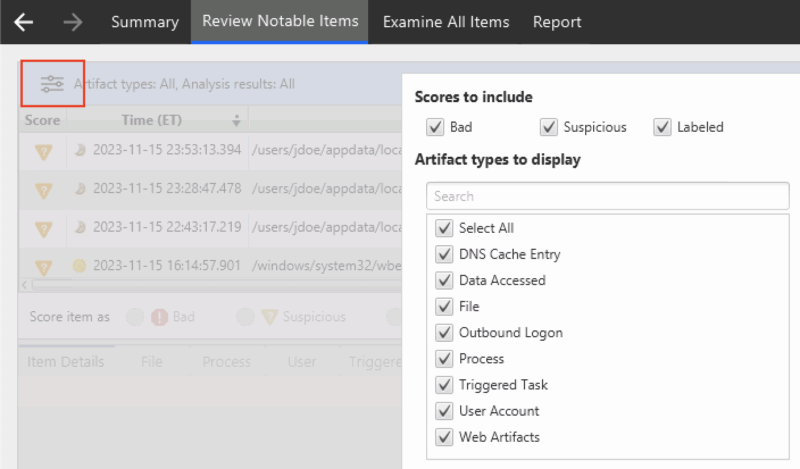
To get to the filters, use the button in the upper left and that will allow you to filter by score, type, dates, etc.
Summary View Has Old Dashboard Controls
If you are ever looking for some controls you used to find on the host dashboard, they are probably on the Summary panel.
- To restart malware scanning, go to Summary/Analysis Jobs.
- To look for collection errors, go to Summary/Data Issues.
- To see if a file was collected, go to Summary/Collection Information.
Hayabusa Integration for Application-layer Attacks and Sigma
Cyber Triage will now run Hayabusa on collected event logs to provide even more detection coverage for application-layer attacks. Hayabusa comes with a powerful set of rules and Cyber Triage users can now benefit from them.
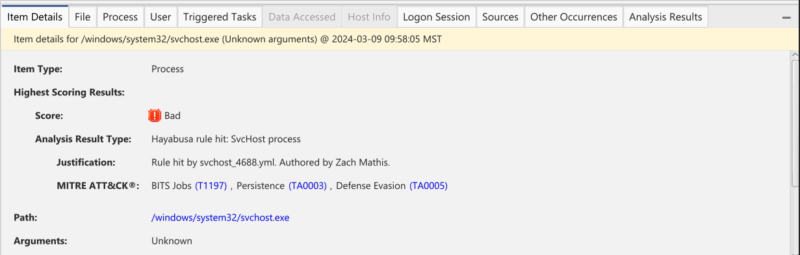
Hayabusa is automatically run on all incoming data. You do not need to do anything special to enable it.
You can also extend Hayabusa with Sigma rules, which will then be run on the event logs (but not all information artifacts).
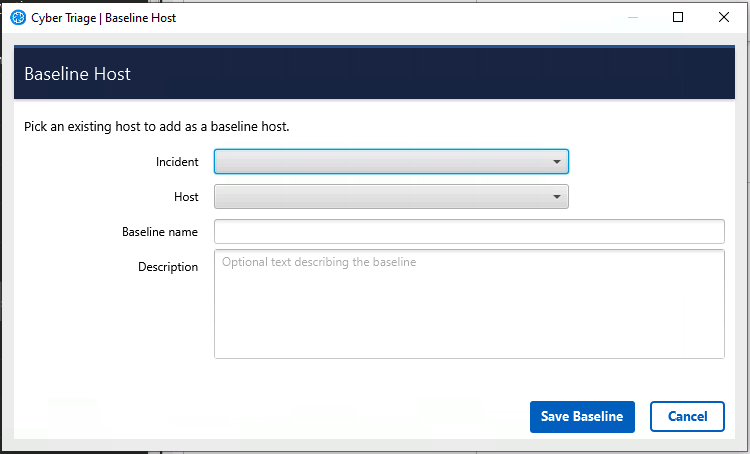
Reduce False Positives with Baselines and Gold Images
You can now configure Cyber Triage to know about your gold images and use them as a baseline. Any artifact found in those images will not be later scored as bad or suspicious. This will save your analysts time because they won’t need to manually add items to the “Good Lists.”
To add an item as a baseline:
- Ingest the gold image.
- Go to the options panel and specify that it is a baseline.
You can find more information in the user manual.
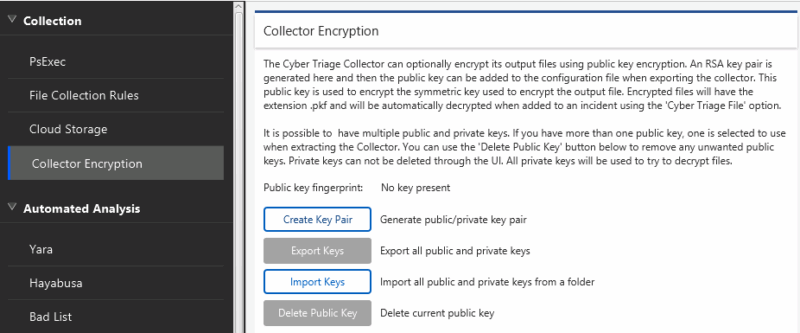
Encrypt Collector Output with a Public Key
The Cyber Triage Collector can now use public key encryption to secure its output. It previously supported a password, but this was error-prone and more risky because the password had to be supplied on the target system.
Now, the Collector can encrypt the data, and it can only be decrypted by the main Cyber Triage application.
You can generate the RSA key pair from the Options panel.
You can find more information in the user manual.
New Scoring Option: Unknown
Cyber Triage will score some items as suspicious if the item could be either from an attacker or normal system activity. Users can now mark normal activity as “Unknown” instead of “Good.”
Marking an item as “Unknown” simply means that it is not suspicious for the reasons that Cyber Triage initially thought, but it may ultimately be suspicious or bad for other reasons. Whereas marking an item as “Good” means that you know it is good and should never be considered Bad or Suspicious.
![]()
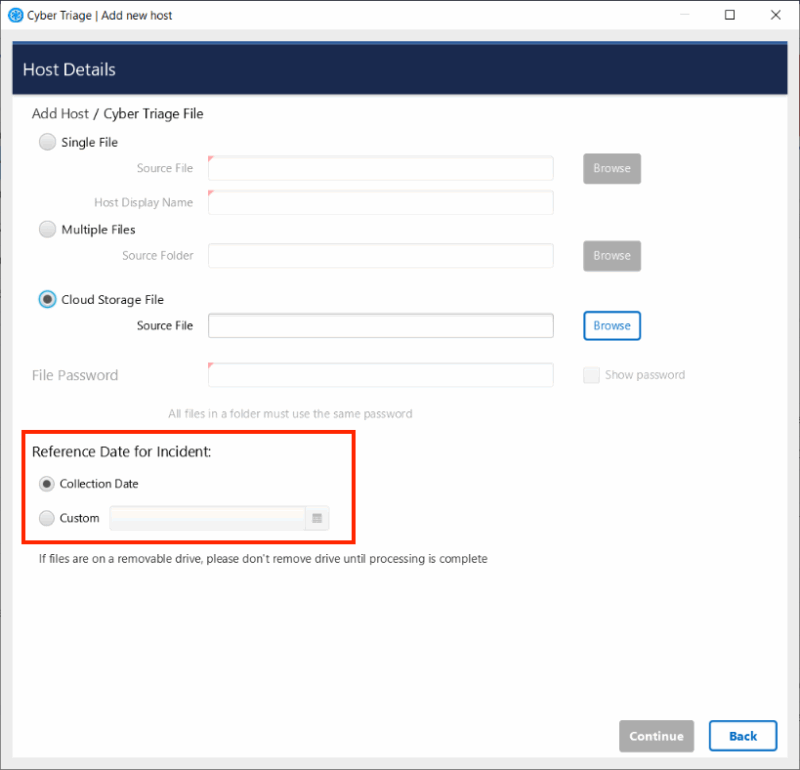
Set an Incident Reference Date
In an ideal world, you quickly collect from and analyze a host after an incident. But, sometimes weeks go by.
If that happens, you can now set a reference date when you add a host. This allows the time-based analytics to be based on that past date. For example, it will focus on the 30-days prior to the date you specify instead of the 30-days prior to when you did the collection.
You can specify this date when you add any host:
Standard Pro Malware Limits are Now Weekly
Lastly, we always want to make sure you get your investigations done quickly and never want you to hit your malware scan limits and have to wait to resume.
Standard Pro (which is the desktop version with batching and higher malware scan limits) now has weekly limits instead of daily. This means that if you have a lot of cases in one day, you can use them all up in one day instead of needing to spread it out over 5.
No change is required. Cyber Triage will automatically make the change.
Try it Out
You can get the latest copy (including 7-day evaluation) from here.