Cyber Triage has two sets of users and we do our best to make them both happy (even though they want different features). The most recent 2.11 release focused on our “deep dive” users to allow them to more efficiently perform root cause analysis.
This blog covers:
- Two of those new deep-dive features
- Lists all of the changes
- Highlights what’s coming in version 3.
Investigation History
When investigating an endpoint, you often follow leads that don’t result in you finding relevant evidence. For example, you may:
- Start with a suspicious program being executed
- Jump to the timeline to see what happened before it was run
- Notice a file being created before the program was executed
- Jump to the file explorer view to see what else was in the same folder as the file that was created.
If it turns out that the file creation was benign and the folder not interesting, then you want to back up to resume reviewing the list of program executions.
The new Cyber Triage release tracks what items you select and where you browse to. The new arrows in the upper left allow you to backtrack to the point that you want to resume from.
Timeline Filtering
Last year, we added the timeline feature to Cyber Triage to enable you to see what happened before and after a given event. The challenge though is that there are often A LOT of events on a system and there can often be a lot of noise from non-relevant events.
The latest release of Cyber Triage added filters to the timeline that can restrict what data types to show. Example data types include program run events, user logins, and file times (modified, created, etc.).
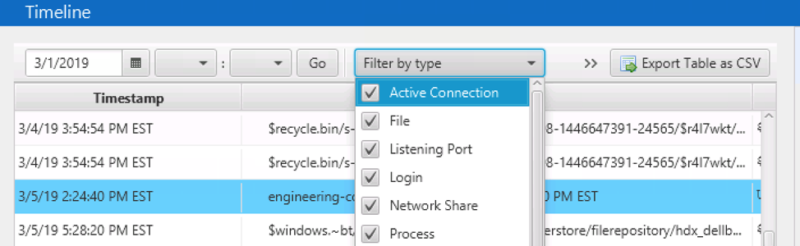
An example of when you may use this is if you have evidence of program execution, but are unsure what user executed it. In the timeline, you could use filtering to remove all event types except user login and program execution so that you can see who logged in before the execution.
Other Changes
Other changes in this release include:
- “Remote Logins” panel changed to “Logins” with a filter to show just remote or local logins
- Collect more timestamps to make timeline more complete (from registry keys, more prefetch times, process creation event logs, and scheduled task action event logs)
- New Blacklist type for “Simple Paths”
- Improved argument parsing for startup items and program run to reduce false positives.
Version 3 is Coming
Version 3 will be released later this year and include:
- New database infrastructure to allow hunting, increased scaling, and easier session management
- Use of cloud infrastructure to make setup easier and allow collaboration.
Try It Out
Our goal at Cyber Triage is to make your incident response faster, easier, and cheaper. And we believe our software does just that.
If you like to see how Cyber Triage could help your workflow, click here to try to today!