The new Cyber Triage release allows you to better understand the impact of a threat. Now, you can automatically see what registry keys reference a file with malware, what processes are using the file, and remote hosts with active connections to those processes.
This new feature in 1.7 allows incident responders to more easily pivot in the data that Cyber Triage collects with its agentless system. This gives a faster and more thorough response than using ad-hoc techniques.
Context is King
When responding to an endpoint, you often want to confirm an incident and determine how bad it is so that you can quickly make some important remediation decisions. To determine how bad something is, you often need to look at what data was accessed and what other hosts and user accounts were involved. You can now do this in Cyber Triage with a new set of tabs at the bottom of the UI. This gives you information about items that are related to the item you have selected.
The new Cyber Triage feature makes it easier to find related data. Let’s look at two examples.
Malware File
Let’s say that Cyber Triage flags a file as being malware based on data from OPSWAT Metadefender. You want to know more about this file on this system.
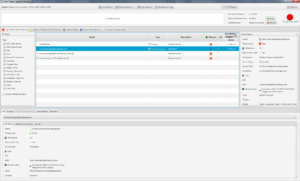
First, let’s see if had a persistence mechanism on the system to startup every time or as part of a scheduled task. We can see in the new interface that there is a registry key that causes it to start each time.
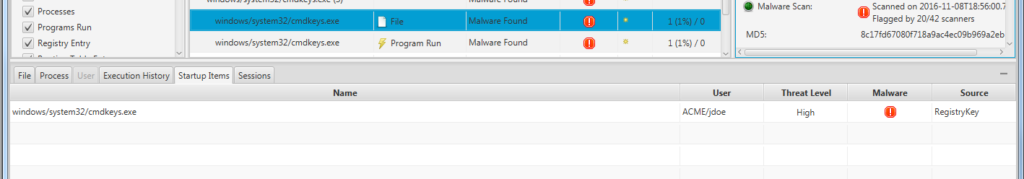
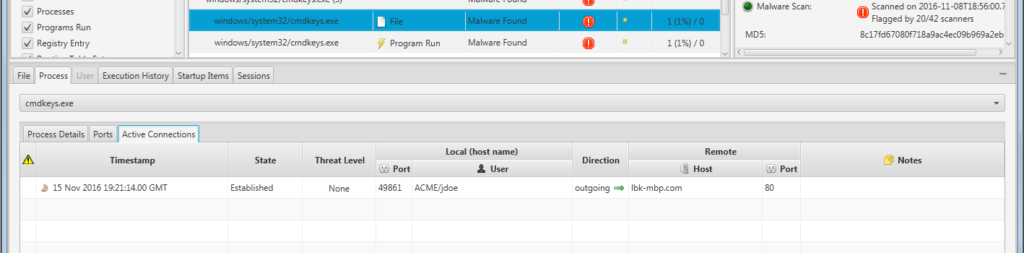
We can also see if the file was associated with a currently running process and, if so, what network connectivity it had. We can see in this example that there was a running process and it had an active network connection to an external address on port 80.
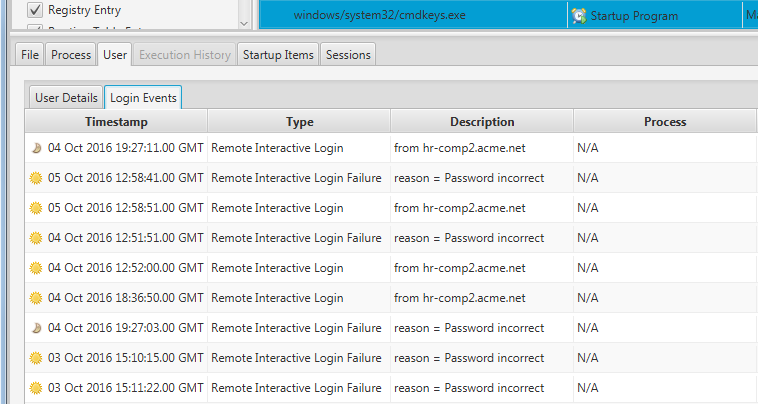
We can also use the User panel to see more information about the user account associated with the file. What was their login patterns and do they have administrator privileges?
We can also see the 8 NTFS timestamps to see when the file was created on the system to know how long the system had been infected.
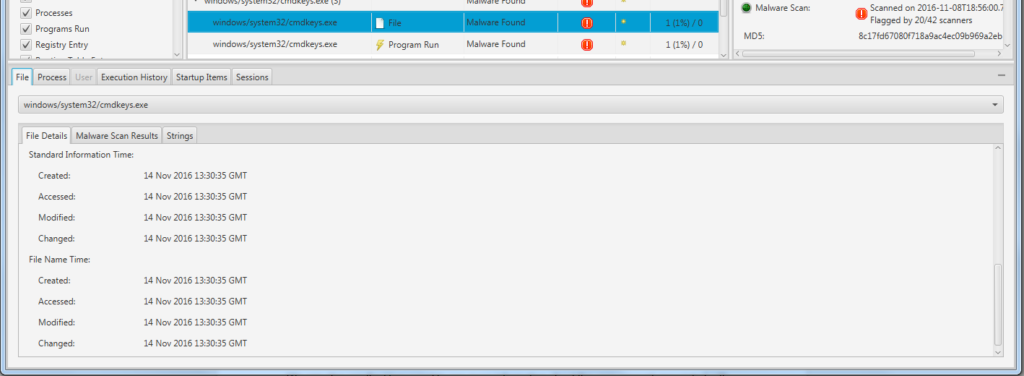
With this new feature, we were able to go from a single executable and quickly determine if it was running, how it was started, and what hosts it communicated with. We can now block network traffic to that address and use the dates as a starting point for further investigation.
Suspicious Startup Item
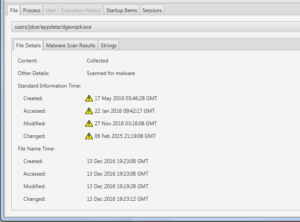
In another example, Cyber Triage identifies a startup item as suspicious because it is in a non-standard path, for example it could be in a temp folder. However, the malware scanning does not identify it as known malware. It could be a new type of malware that is not yet flagged, so some manual review seems appropriate if you have the skills to do so.
First, we pivot to the file itself in the new interface and look at the 8 NTFS timestamps to look for evidence of time stomping (changing the times after the file was created) and to see how long ago the file was created. In this case, we can see that the dates in the Standard Information attributes are before the dates in the File Name attribute, which typically indicates time stomping. The exclamation marks in the Cyber Triage UI show us this. This file now becomes more suspicious.
We can also go to the file content itself and see if it looks suspicious. Many types of malware are packed and therefore have few visible strings in them. We can look at the entropy value that Cyber Triage tells us about the file to see that it is highly compressed and the interface suggests that it is packed. This file becomes more suspicious.
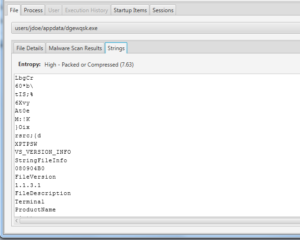
With this new user interface, we were able to quickly review some other indicators of the file and then decide to perhaps upload the file to VirusTotal or some other malware scanning system for a 2nd opinion.
There is More Coming
There are a series of releases planned that focus on interface improvements to make responses faster. We are updating the interface to automate the workflow more and give more context about when events in the incident occurred.
If you would like an evaluation copy of Cyber Triage, please contact us.