Now, you can review artifacts from multiple hosts at the same time to see the big picture.
New features:
- Incident-level Bad and Suspicious Items View
- Incident-level Artifact Search
- Incident-level IOC Search
To evaluate the latest version, use this form.
Register here to attend a webinar on December 12 to hear about these new features.
Get an overview of what’s known in the incident
Having incident-level visibility is crucial when dealing with cybersecurity incidents that span multiple hosts. It allows security teams to understand how the attack unfolded and identify potential patterns or vulnerabilities across the network. This is why Cyber Triage 3.9 introduces several new ways to look across hosts in an incident.
The first is the incident dashboard. This view allows you to access and manage hosts involved in an incident, get an overview of bad/suspicious items across all hosts, and access incident-level features.
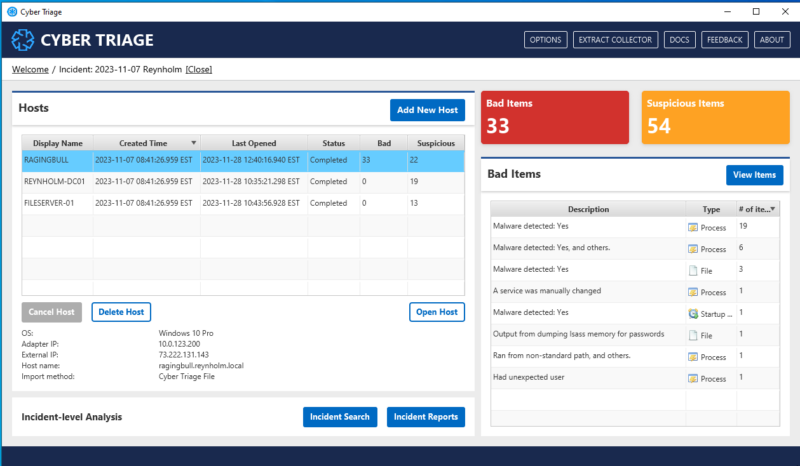
Looking to the right side of the screen, you will now find a “View Items” button:
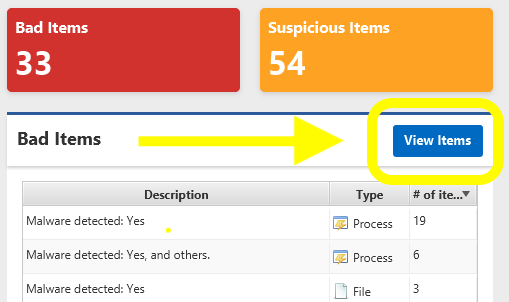
Which opens a cross-host or incident-level “Notable Items” view. This new view shows all Bad and Suspicious items across all hosts, sorted by time so that you can see what is known and when.
This allows you to, for example, focus in on:
- Which host has the earliest bad activity
- When are there big gaps in activity
- Which hosts had activity near the initial SOC alert
Each item will open an “Item Detail” panel with additional information when clicked.
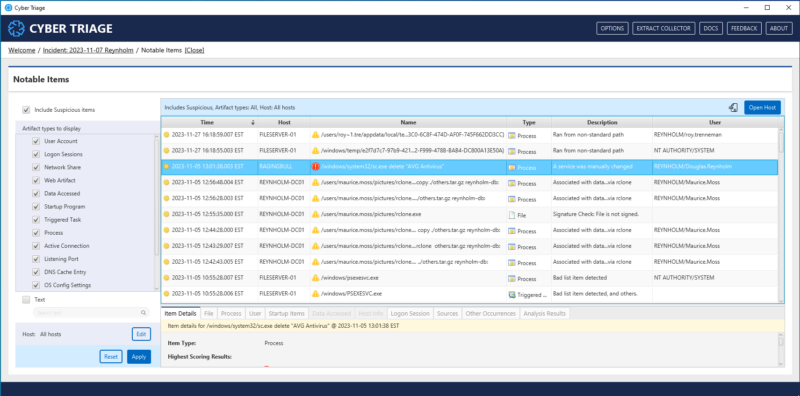
Review activity across all hosts
It is critical to be able to start with one event and look for related activity on any host in the incident to understand the source and impact of the event. Cyber Triage now allows you to view all artifacts across all hosts in a specified time range, which can show lateral movement and activity related to bad items.
There are two options for search:
- Text / IOC Search enables you to scope an incident and identify where an attacker was active. This incident-level Cyber Triage feature searches across all artifact types, looking for hashes, IPs, and other text values. IOC Search returns less detailed information than Advanced Search but helps you quickly determine which artifacts to examine in more detail.
- Advanced Search lets you hone in on a specific artifact type and pulls back more information for review. The results panel varies depending on the artifact type you search for to give you the most relevant information possible.
You can click on an item from the Text/IOC and Advance search results screen to bring up a detailed view of everything known about that item.
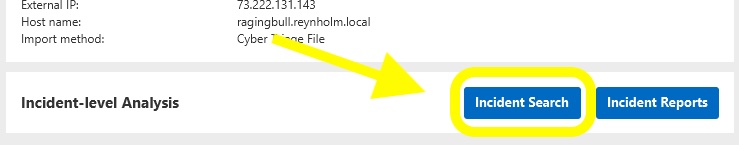
How to use incident-level search
From the incident dashboard, click the “Incident Search” button at the bottom of the screen:
The “Text / IOC Search” tab will open by default. Enter a text value or IOC. Specifying a date range can help to narrow results.
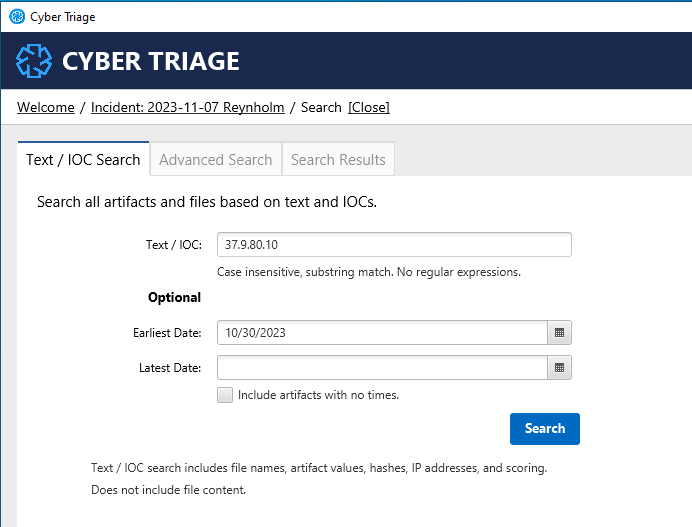
Select the “Advanced Search” tab to narrow the search to a specific artifact type. We recommend narrowing the date range whenever possible to return only the most relevant results. You can further narrow the search by including an IOC or text value in the query.
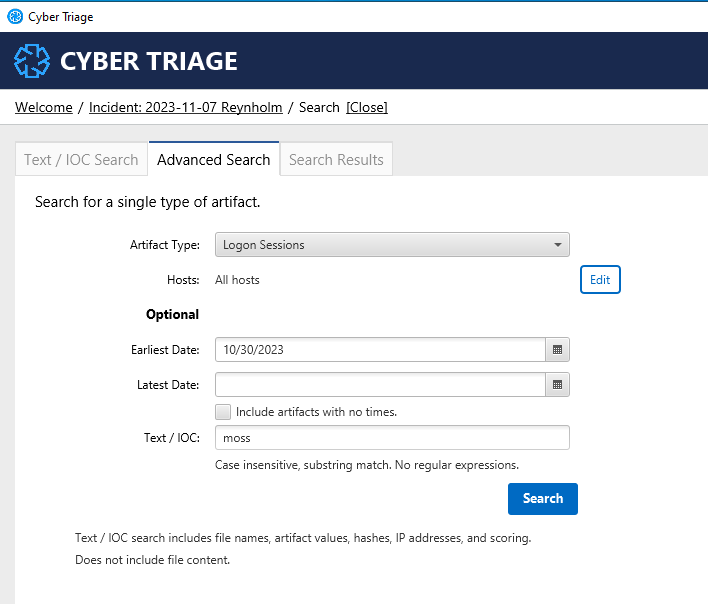
Searches will take you to the final tab on the right. Pay attention to the information in the light blue bar to ensure your query went through correctly. Searches can take some time to complete, so start from a narrow query whenever possible.
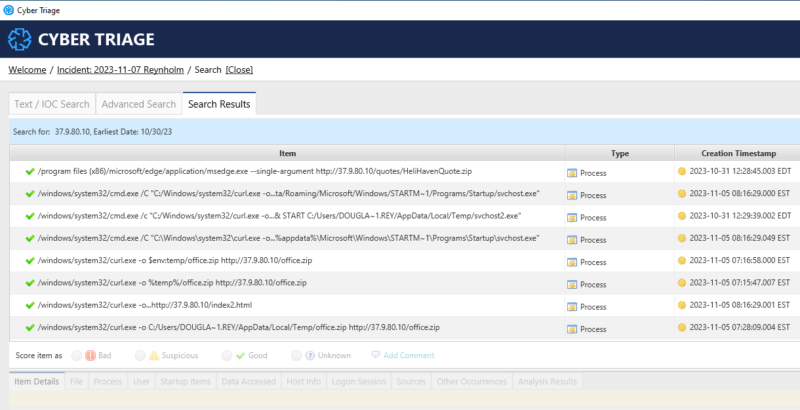
To learn more about a specific item in the results, click on it to open the detailed item view or click “Open Host” on the right side to switch out of the incident view.
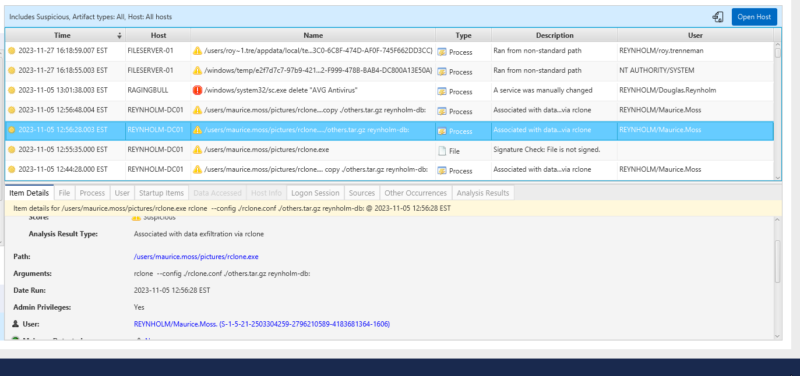
More detailed instructions and screenshots are in the User Guide.
Try It Out
You can download an evaluation copy using this form. If you are already a customer and haven’t received a link, send a message to support.
We will continue building features to analyze as many systems as possible and enable you to dive deeper.
Are you using an EDR?
Check out our recent blog on how to send a Cyber Triage collection directly from your EDR.