Sandboxing is a critical DFIR capability because so many incidents involve malware. Sandboxing helps you to identify what a file will do. Is the file benign or malicious? If it’s malicious, then what will it try to do when run?
In this blog we’ll cover this important digital forensics and incident response capability, focus on a specific offering from Recorded Future, and cover how to use that service for free in Cyber Triage.
Sandboxing in Incident Response
What is Sandboxing?
Sandbox analysis is a form of dynamic executable analysis whereby a program is launched and observed. It’s referred to as a “sandbox” because it’s run in an isolated “play” area that will not impact your production systems. The sandboxing solution will record what files are accessed, network connections created, etc.
You can do dynamic analysis on your own by launching programs, but it will require you to either set up an isolated environment or risk the need to rebuild your systems if malware spreads. Note that in addition to launching executables, you can often open PDF, DOCX, OneNote, and other file formats that are used to infect systems.
The output from a sandbox is often lists of:
- Files that were created or opened
- Registry keys that were created or opened
- Hosts that were connected to
- Other process behaviors, such as mutexes, hooks, etc.
Sandbox vs Signature Analysis
There are two broad categories of malware analysis: dynamic and static.
Static is all about looking for signatures in the file contents and making decisions. The file is never ‘executed’ or opened in its intended application (such as Word). The file is scanned for byte patterns or parsed with some specialized detection tool to look for things that often indicate malicious intent. This is what most malware detection is.
Dynamic is all about launching the file and observing. Sandboxing is a form of dynamic analysis.
Both play a critical role in DFIR because they each have strengths and weaknesses.
Benefits of Sandboxing
Sandboxing ultimately allows you to make better decisions about a file. It allows you to answer two types of DFIR investigative questions:
- What does this file do? You have a known malicious file and you want to better understand what it does. For example, maybe several malware scanning engines or a Yara rule flagged an executable and associated it with a malware family. If you want to understand the malware’s capabilities, you can search for blog posts about it and you can also run it in a sandbox. With the sandbox results, you can then look for the files, hosts, etc. that the executable is capable of accessing.
- Is this file malicious? Maybe you have a file that you’re suspicious of. This can happen because a small number of malware scanners thought it was malicious, but some didn’t. Or, maybe because it’s a new file that isn’t on VirusTotal or ReversingLabs yet, but you found it in a funny location or was an attachment. Sandboxing can help you make that decision about if it’s benign or perhaps malicious. Some sandboxing tools will also generate a score based on its behavior.
Limitations of Sandboxing
While sandboxing has many benefits to helping the DFIR examiner, there are a few limitations:
- Sandboxing is slower than signature-based analysis. If you have hundreds or thousands of files to analyze, it is far faster to do a hash-based lookup to know if the file is already known to be good or bad.
- Malware may know it’s being watched. Many forms of malware will try to detect that it’s being run in a sandbox and either shut down or do something boring. So, malicious software may not always act maliciously in a sandbox.
- Malicious activity may not happen during execution. Many sandbox tools have a time limit on how long they run. It could be that the malware either sleeps for a while or waits for some trigger to do malicious activity. That activity may never happen before the sandbox kills the process.
Recorded Future Triage (i.e. Hatching)
We’re going to take a look at the offering from Recorded Future, which acquired Hatching last year. We partnered with Recorded Future so that Cyber Triage users have free access to the Recorded Future Triage sandbox.
Recorded Future Triage offers dynamic analysis for Windows, Linux, Mac, and Android files. It runs the files in a cloud-hosted environment and provides you with a detailed report on the behavior of the malware that includes malicious scoring of the file. It was created by people who were originally involved with Cuckoo Sandbox.
Users of the service can get live interactive control of the VM running the detonated file and see a video of the desktop as it was running. It also has APIs to integrate with various cyber security solutions.
Sandboxing in Cyber Triage
In the 3.4 release, we added our first basic integration with the Recorded Future Triage sandbox. The integration allows you to choose files to upload to the sandbox and then later get the results.
This feature allows you to get a better understanding of what a file is capable of doing so that you can find additional evidence or commit to a file being good or bad.
The expected use cases are:
- You’ve collected hundreds of executable files and libraries from a suspect system and processed them with Cyber Triage. It’s scoring algorithms and integration with ReversingLabs (which includes 40+ malware detection tools) results in a couple of files being marked as suspicious. You’re not sure if the file was marked as suspicious as a false positive or if it is truly bad. You can use the Recorded Future Triage sandbox to get more information.
- ReversingLabs scores the file as bad and you want to better understand what the process did. You can submit it to the sandbox, identify what files were created and then open those up to see what data was collected.
How To Upload Files
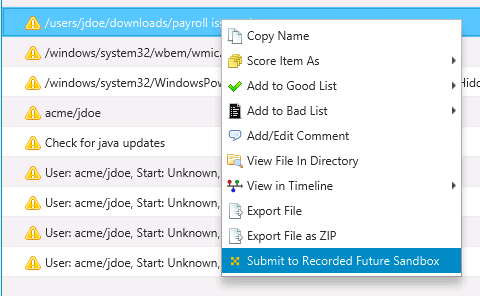
Currently, you need to initiate the process to upload the files for analysis. To do so, right click on a file and choose “Submit to Recorded Future Sandbox”.
You’ll then get a prompt to review the privacy terms associated with the upload. They are different from those for ReversingLabs. The basic takeaway is that the results will be available in the Recorded Future threat intelligence feed, but not associated back directly to you.
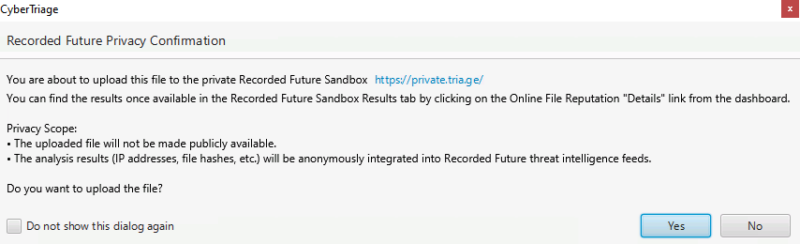
The file will run in the sandbox for 2 minutes, so you do other things while you wait for the results.
How to Get Results
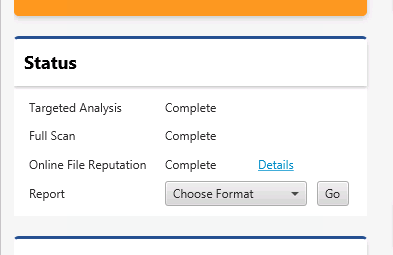
When you are ready for the results, go to the dashboard and choose the “Details” button for “Online File Reputation”.
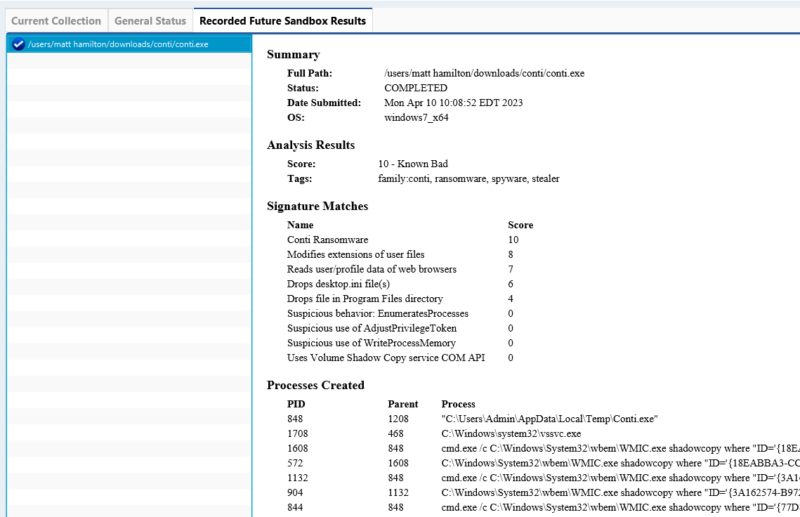
That brings you to a window with a “Recorded Future Sandbox Results” tab. Selecting that will show you the submitted files. In the below example, you can see that the uploaded Word file got marked as “Bad” from spawning a child process and creating files.
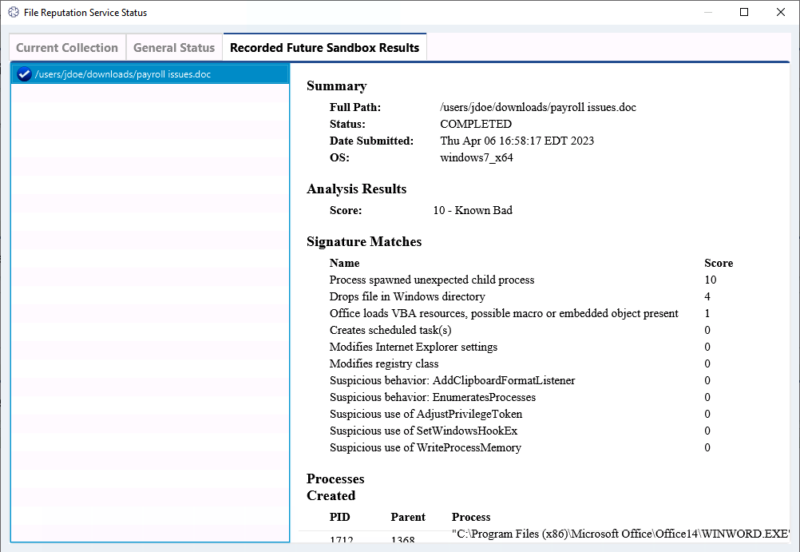
The report has fields for:
- Signatures that matched
- Processes launched
- Network connections made
- Files created
Here’s an example from a malicious Conti executable:
Conclusion
Sandboxing is a useful capability to have access to during your DFIR investigation. The integration of Recorded Future in Cyber Triage makes it easy for an investigator to upload a file and identify its capabilities.
Future releases of Cyber Triage will automatically upload suspicious files and allow you to view the video of the desktop during detonation.
You can try out Cyber Triage and the Recorded Future integration by filling out the form here.