To protect the enterprise network, SOCs need to be able to investigate alerts.
But they often lack the capability to investigate at scale.
The core problem:
Their tools do not provide them with “clues,” which are critical to solving mysteries.
This blog we explore:
- What SOC investigations are.
- Why clues are important to them.
- Why clues are hard for SOCs at scale.
- How SOCs can investigate clues at scale.
Let’s get started. You can also watch a recorded webinar on this topic that we did with Brett Shavers.
Jump to…
SOCs Investigate with Endpoint Triage
Three Types of Intrusion Questions
Clues Go Beyond Known Bads
Detection Systems Don’t Find Clues
Manually Finding Clues Doesn’t Scale
Automated Investigation Platforms Find Clues
Cyber Triage Shows You Clues
Make Sure You Can Find Clues
SOCs Investigate with Endpoint Triage
When SOCs get an alert about an endpoint, they need to triage the endpoint to see what the attacker did.
Endpoint Triage is a short digital investigation whose goal is to prioritize further investigation.
The SOC needs to decide:
- Can it wipe the endpoint?
- Should it call incident response?
Endpoint Triage is needed because the EDR or NDR alert could be activity that happened several days into an attack. The investigation will show if there is other activity besides the alert.
Three Types of Intrusion Questions
Investigations, including Endpoint Triage, answer questions.
There are 3 forms of questions around intrusions, all of which are based on knowledge of previous attacks and how computers operate:
- Known bad questions: These are based on seeing the same exact activity as previous attacks. Example: Is there a file with the same SHA256 hash as has been previously seen as malware?
- Similar bad questions: These are based on seeing similar activity as a previous attack. Example: Is there a file with the same byte sequence, but different hash, as previous malware?
- Abnormal questions: These are based on seeing unexpected activity of similar theme to previous attacks. Example: A new process that launched after an attacker logged in. The file doesn’t match on any known signature, but you know attackers usually run malicious programs.
The latter 2 are needed because every attack is different, and you can’t rely on only finding exactly the same things that were seen before.
Looking for “similar bad” and “abnormal” artifacts is what gives you clues.
Clues Go Beyond Known Bads
Clues are the artifacts you find when looking for things similar to past incidents. Because attackers try to blend in, some of those similar things will be normal system behavior and others will be from the attacker.
Clues will point you to time frames, user accounts, and folders that contain additional evidence.
For example:
- You might look at recently created scheduled tasks because attackers will use them for persistence.
- You notice one was created six days ago on May 21.
- It runs an executable in a C:ProgramDatachromium folder.
This is a clue.
It’s in a non-standard location for executables, is a method used by attackers, and is recent.
With this clue, you should:
- This item: Examine executable with malware scanning and sandbox analysis.
- Location: Look for other files in the chromium folder.
- Time: Look at other activities when this task was created on May 21.

Detection Systems Don’t Find Clues
Detection systems don’t highlight clues because the false positive rates are too high. SOCs ignore and tune out detections that are more often wrong than right.
The typical SOC model is to have analysts first focus on low false positive detections and then dive deeper using Endpoint Triage to understand what else happened.
Manually Finding Clues Doesn’t Scale
When an analyst needs to perform Endpoint Triage after an alert and doesn’t have an investigation tool, they need to manually find clues.
This is a tedious process.
Consider this output from an EDR:
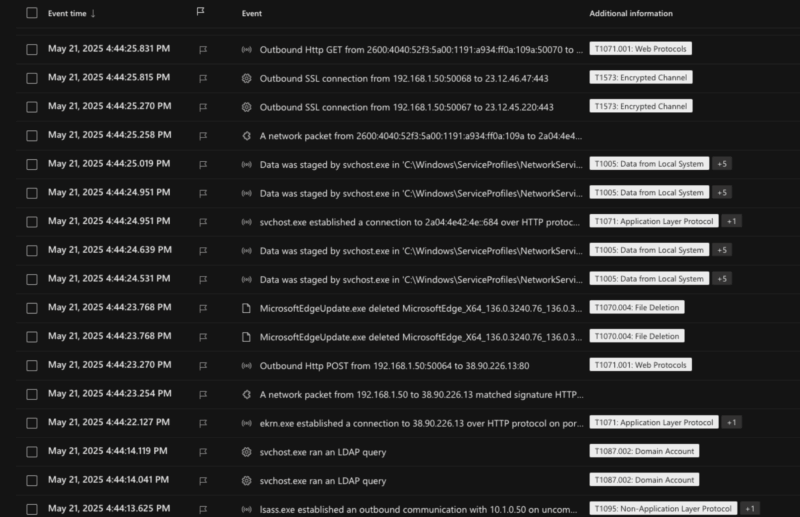
The analyst needs to be able to review pages of data like this to see if there are new processes, new users, and other new activity on the system. Most of this data is normal activity and not related to an incident.
Further, the analyst is also responsible for knowing:
- What all past attacks look like.
- What is normal.
This is time-consuming and error-prone.
This is why some organizations choose not to do Endpoint Triage and instead make the risky decision to ignore the system and see if it causes any problems in the later weeks.
Automated Investigation Platforms Find Clues
To scale investigations in your SOC and get you the answers you need, you need an investigation platform that can generate clues. Let your detection systems detect and then start the investigation process.
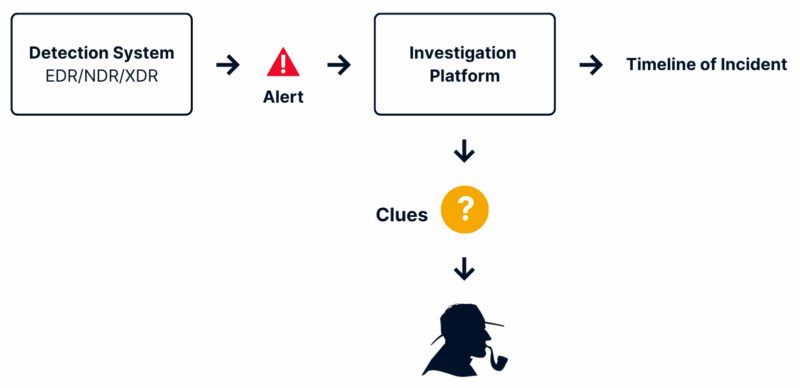
An Automated Investigation Platform is optimized for quick and accurate investigations:
- Flags the known bads and suspicious.
- Imports data from a variety of sources and methods (continuous and point in time).
- Helps the investigator make decisions about the suspicious.
Cyber Triage Shows You Clues
Cyber Triage analyzes endpoint artifacts and highlights ones that are bad or suspicious. The suspicious ones are the clues that you should review and determine if they are relevant to the incident or normal activity.
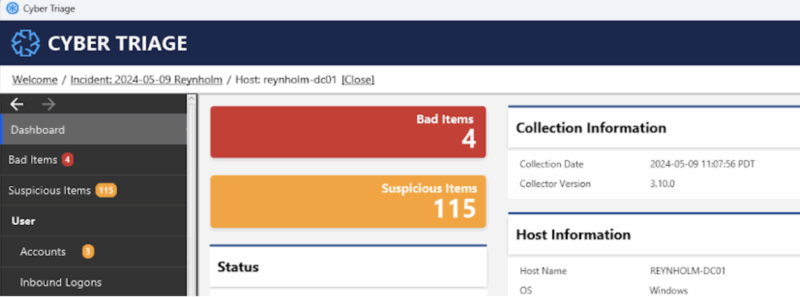
For example, the below dataset is from our evaluation data and shows several examples of suspicious things to understand if they are normal or not in the environment.
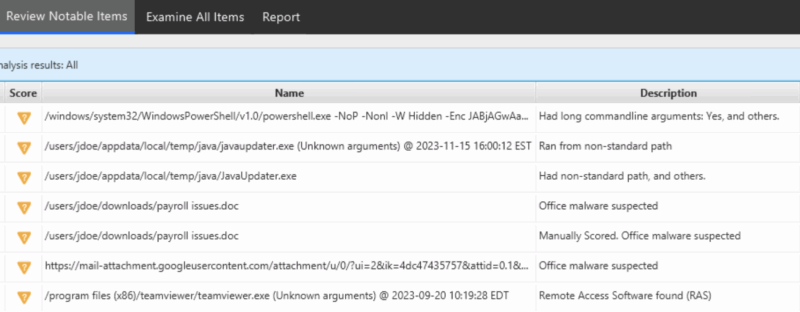
It highlighted:
- Programs running from non-standard locations.
- Startup items that have long arguments and could be file-less malware.
- Existence of remote access software, which could be nothing or could from an attacker.
You can add items to a Goodlist based on what is normal in your environment so that certain locations and programs do not generate alerts.
Cyber Triage integrates with your EDR to collect artifacts for analysis. This allows your analysts to quickly perform Endpoint Triage after an alert.
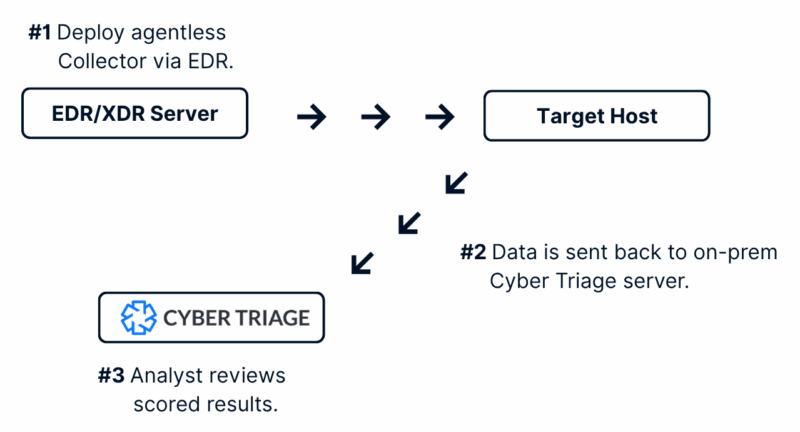
With Cyber Triage, you can triage endpoints with this process:
- Analyst validates the alert and starts a Cyber Triage collection via SOAR or EDR.
- Data comes into Cyber Triage and within minutes has identified bad and suspicious artifacts.
- Analyst reviews the bad items to understand what “known bad” items were found.
- Analyst reviews the suspicious items and makes decisions about if they are from attacker activity or normal.
- Timeline and final report are generated so decisions can be made about escalating or wiping.
Make Sure You Can Find Clues
If you don’t have an automated way to generate clues in your SOC, try out Cyber Triage for free. It will automatically analyze data from EDR or SOAR collections and identify the suspicious items your analysts should review.
You can try Cyber Triage using this link.
