In this post, we’ll cover a unique approach to applying the OODA loop principles to your investigation process.
In our Intro to DFIR series, we talked about specific technical things to look at during endpoint triage. For example, how malware should be investigated based on how it starts, if it is running, and whether there are any remnants. I’ve been posting a few of my articles from this and other series on Twitter and LinkedIn, and on one of those posts, Harlan Carvey commented how “It’s all about the OODA loop…”
Well, that comment inspired this next series, which builds on the last. We’ll now focus on the order in which you look for those things to make the process as fast as possible using the OODA loop.
Our approach differs from existing articles by applying the OODA loop at a different level, focusing explicitly on endpoint triage and deciding whether an endpoint is relevant.
Let’s get started!
Jump to…
What is OODA?
Different Approach on OODA Loop for DFIR
Why Do We Need an Investigation Process?
Series Overview
What is OODA?
The OODA loop is a decision-making framework that is much like the scientific method. It is a process that many of us use on a regular basis without knowing it. By breaking the process into phases and thinking about each, it allows us to be more aware of the situation and make faster and better decisions.
The original motivation for OODA was to enable fighter jet pilots to make faster and better decisions after an observation was made that the pilots who made the fastest decisions were the ones who won. (Check out this page to get an in-depth review of the process’s origins.)
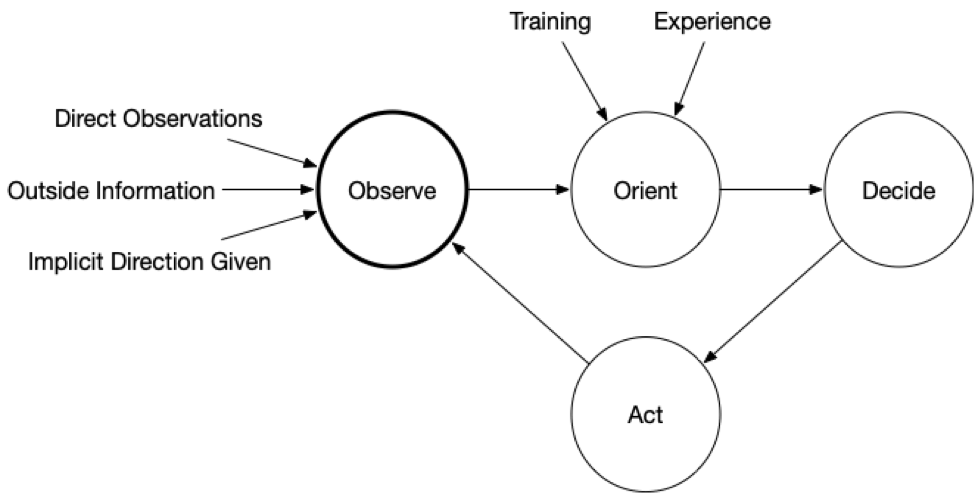
OODA is an acronym with four phases that feed back into each other and repeat as decisions are made and more data becomes available.
- Observe: Observe the situation using a variety of sources that are available. You will never be able to collect all data before making your first decision.
- Orient: Use your experience and training to make sense of what you are seeing. Make hypotheses about what is happening and predictions about what could happen next.
- Decide: Based on your goals, orientation, and timing needs, decide on what action to take and when. Actions could include testing a hypothesis about the current state (i.e. get more data) or to try to change the predictions about what will happen next (i.e. thwart a bad guy).
- Act: Implement the decision.
The impact of the action (and at all stages) should be observed and fed back so that a new orientation can be made and another follow-on decision and action.
Different Approach on OODA Loop for DFIR
If you Google “OODA,” you will come across several other cybersecurity blog posts about OODA, but this one is different.
All of these address using OODA at a higher level in the investigation process. Such as when trying to figure out the full scope of an attack, what are the attacker’s intentions, who should be notified when, etc.
This blog series is all about using OODA within a smaller context of triaging a specific endpoint.
During Incident Response, time is critical. So, we are going to use OODA to minimize the time spent on each endpoint by acting quickly just like a fighter pilot.
Why Do We Need an Investigation Process?
In the previous blog series, we focused on what kinds of data to analyze during endpoint triage. We talked about looking for malware when it starts, when it is running, or remnants it has left behind. We also talked about investigating user activity.
But, we didn’t talk about the order in which to perform them.
If you don’t need to look at all of the data types, then the order that you use may impact how much time you spend.
For example, if the goal of your triage is to answer the investigation question, “Is this system potentially relevant?”, you may need only a few clues to decide that. So, you should focus on getting that answer as soon as possible. Going sequentially through all of the collected data types in Cyber Triage may not be the most efficient use of time.
Instead, it might be better to first review what Cyber Triage automatically flags as bad and suspicious. Then, from there, decide whether it is good enough or if specific things should be analyzed further to increase confidence.
To be clear, there is no single way of performing an investigation. Every investigator will have a different path and look at different types of data in different orders. The goal is to get to the correct conclusion as soon as possible.
Series Overview
The next four posts in this series dive into each of the four phases (observe, orient, decide, and act). We’ll cover what the phase is and how to apply it to endpoint triage.
If you’d like to follow along with the series using Cyber Triage, you try free for 7 days here.
Next post… How to Observe during Investigations.
