The Cyber Triage Collector
Find all the evidence you need for your investigation fast.
The Cyber Triage Collector copies data from a system being investigated so that you can quickly start your analysis.
The Collector can be deployed in any environment.
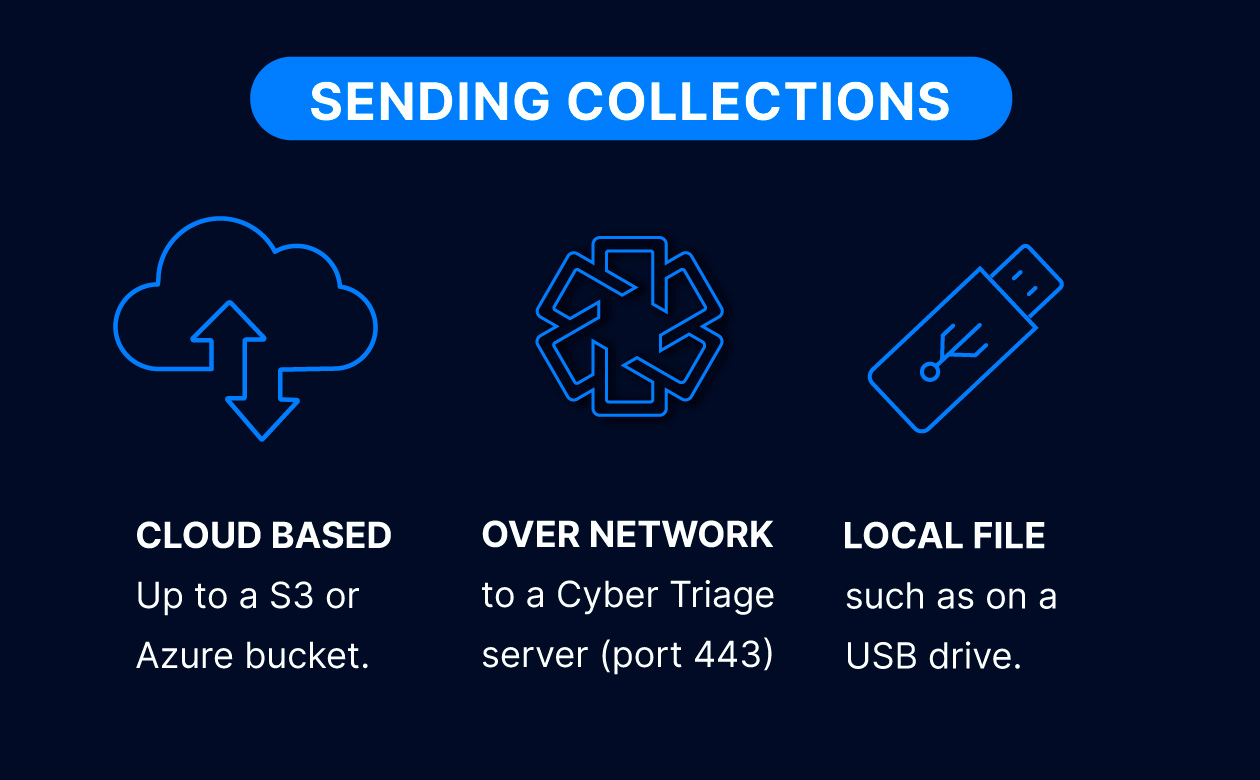
It’s a standalone tool you can deploy via EDR agents, email to your clients, or run from a USB drive. Its output can be sent to a Cyber Triage server, S3 bucket, or saved to a file.
Flexible Launch
There are many options for getting the single EXE file to the target sytem and for getting data back. Many SOCs deploy using their EDR agents.
If you need local IT staff to manually launch collect, there is also a UI wrapper so they do not need to use the command line.
For the full list, contact us.
Comprehensive
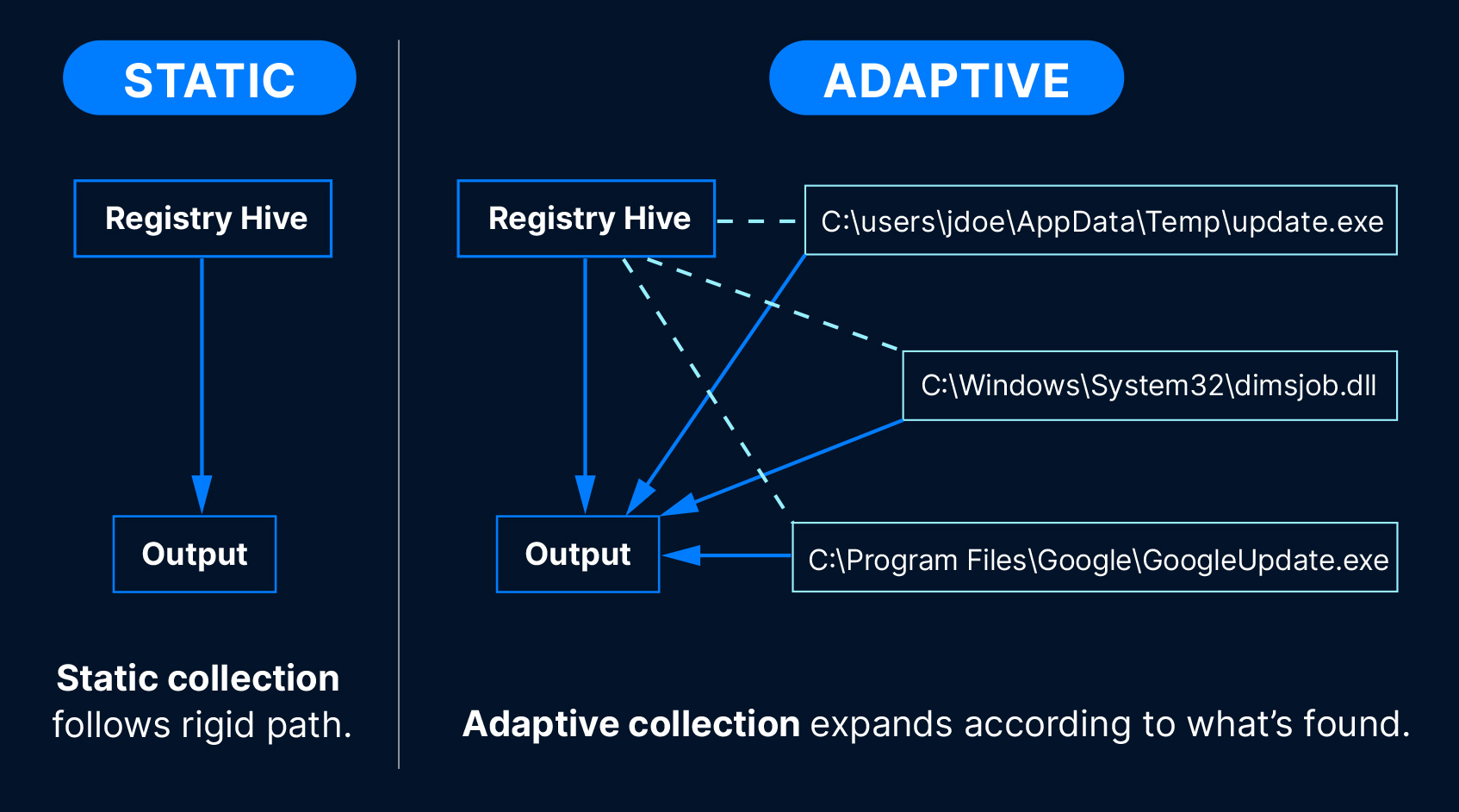
Our Collector is “adaptive” and copies over 1,000 Windows artifact types. Unlike static collectors, it uses rules as a starting point, then expands out the collection according to what it finds.
This means it gets you the most amount of relevant data, especially scripts and executable content.
Customizable
The Collector’s rules can be customized in the Cyber Triage UI.
This is useful when you want to always collect a specific application log or look for an indicator of compromise (IOC).
Flexible Output
The output of the Collector is a single file that can be sent to many destinations. It can be encrypted with a public key.
To use the output in other tools, use Cyber Triage to export the files.
Try Cyber Triage Collector
The Collector comes with all versions of Cyber Triage. Try out Cyber Triage today to get access to the Collector and make sure you quickly get all of the data you need.
Collector FAQ
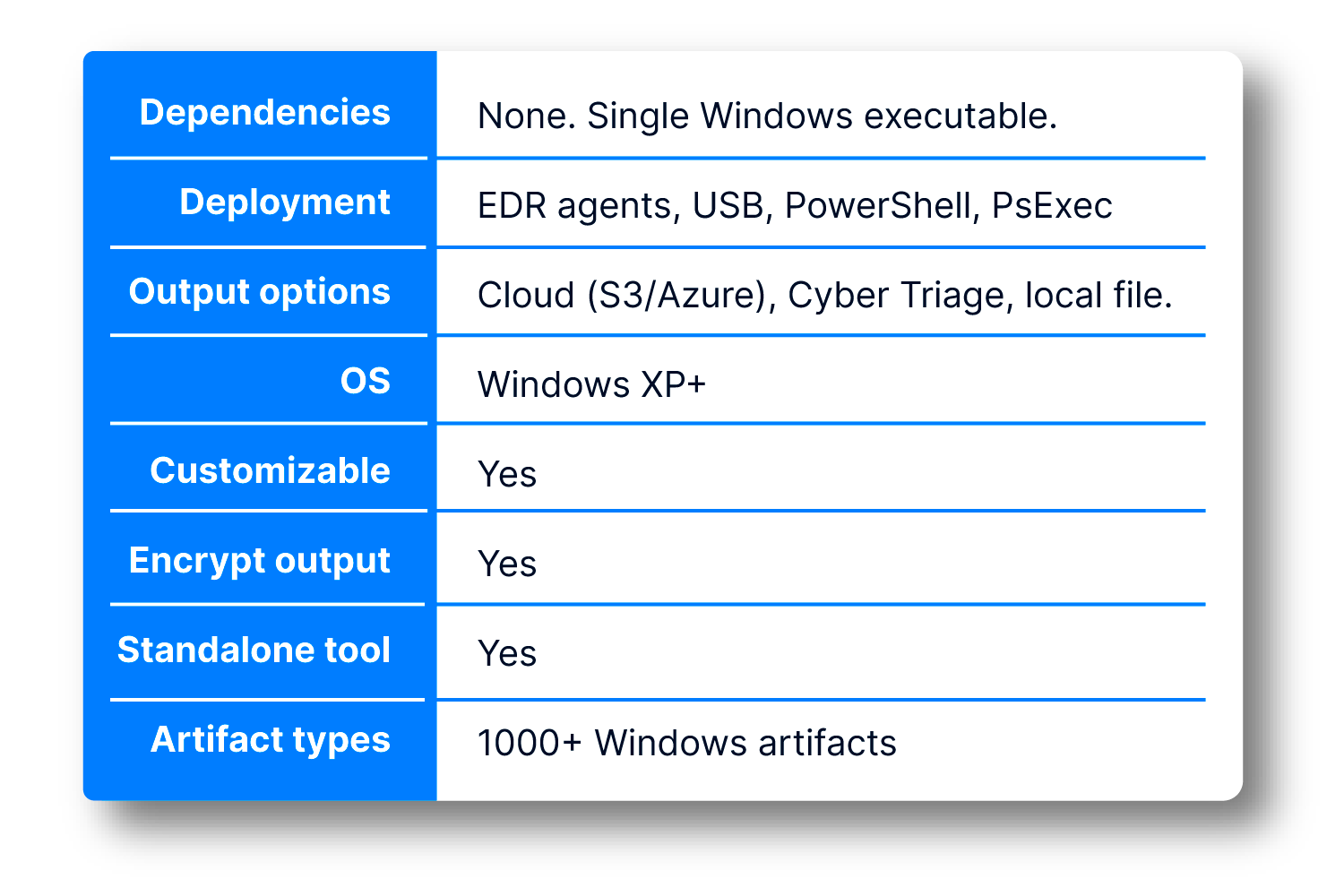
A standalone executable that extracts key DFIR artifacts and source files from a live Windows system or other data sources so you can start analysis fast. It runs on Windows, has no .NET dependencies.
Collections start from rules and dynamically expand based on what’s discovered (e.g., following paths inside artifacts to pull more relevant scripts/executables), maximizing useful evidence with minimal round-trips.
The Collector looks for over 1,000 individual data artifacts ranging from operating system configuration files to application logs. In addition to the standard Windows artifacts (Registry, event logs, Prefetch files, shortcut files, etc.), it uses an adaptive collection algorithm that identifies recently used executables (.exe and .dll). This means that any threat actor tools or malware on the system will also be collected. We also collect logs from RMM tools and other non-Windows applications.
Here’s a list of the types of collected artifacts:
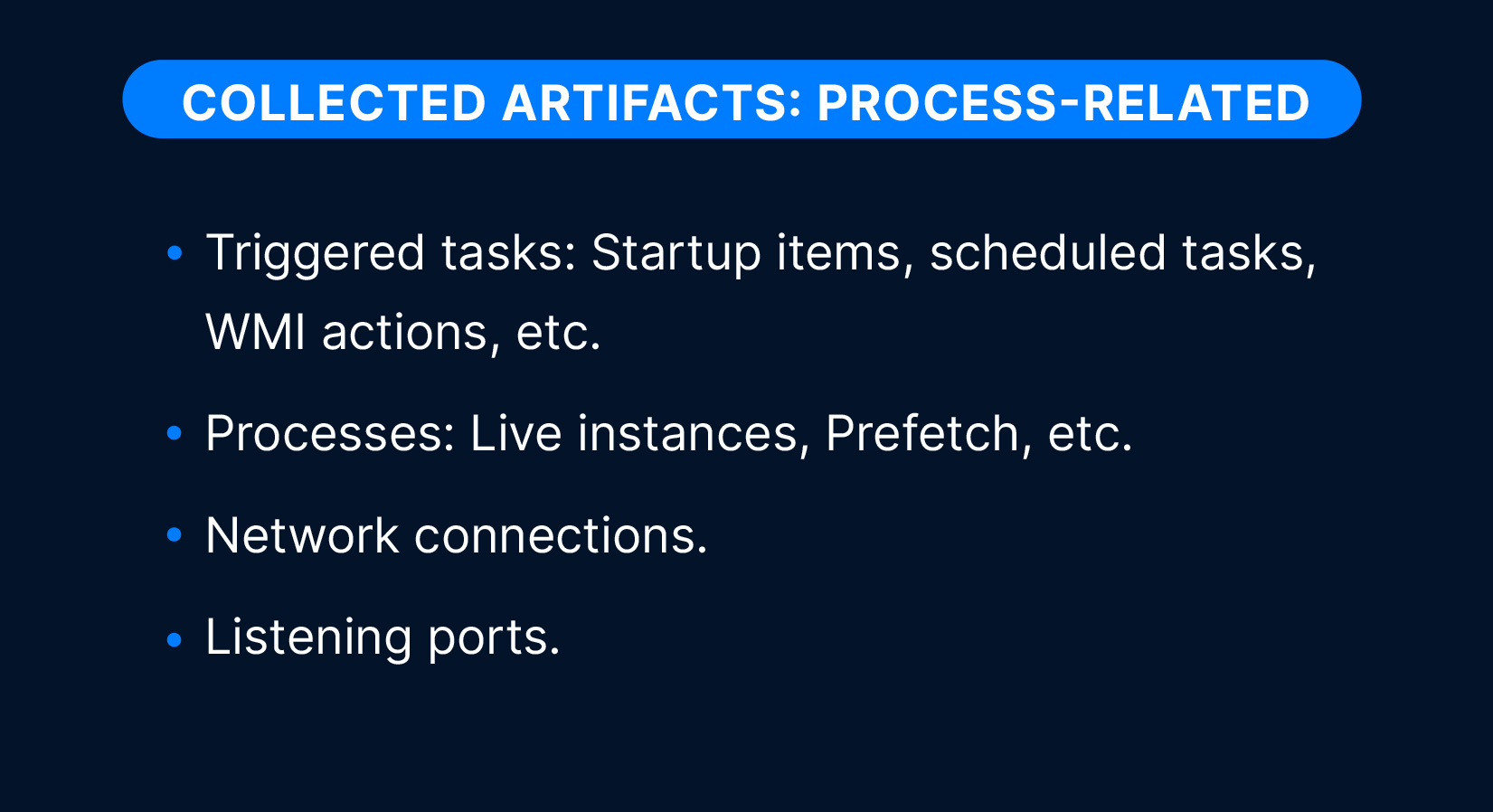
Process-related artifacts:
- Triggered tasks: Startup items, scheduled tasks, WMI actions, etc.
- Processes: Live instances, prefetch, etc.
- Network connections.
- Listening ports.
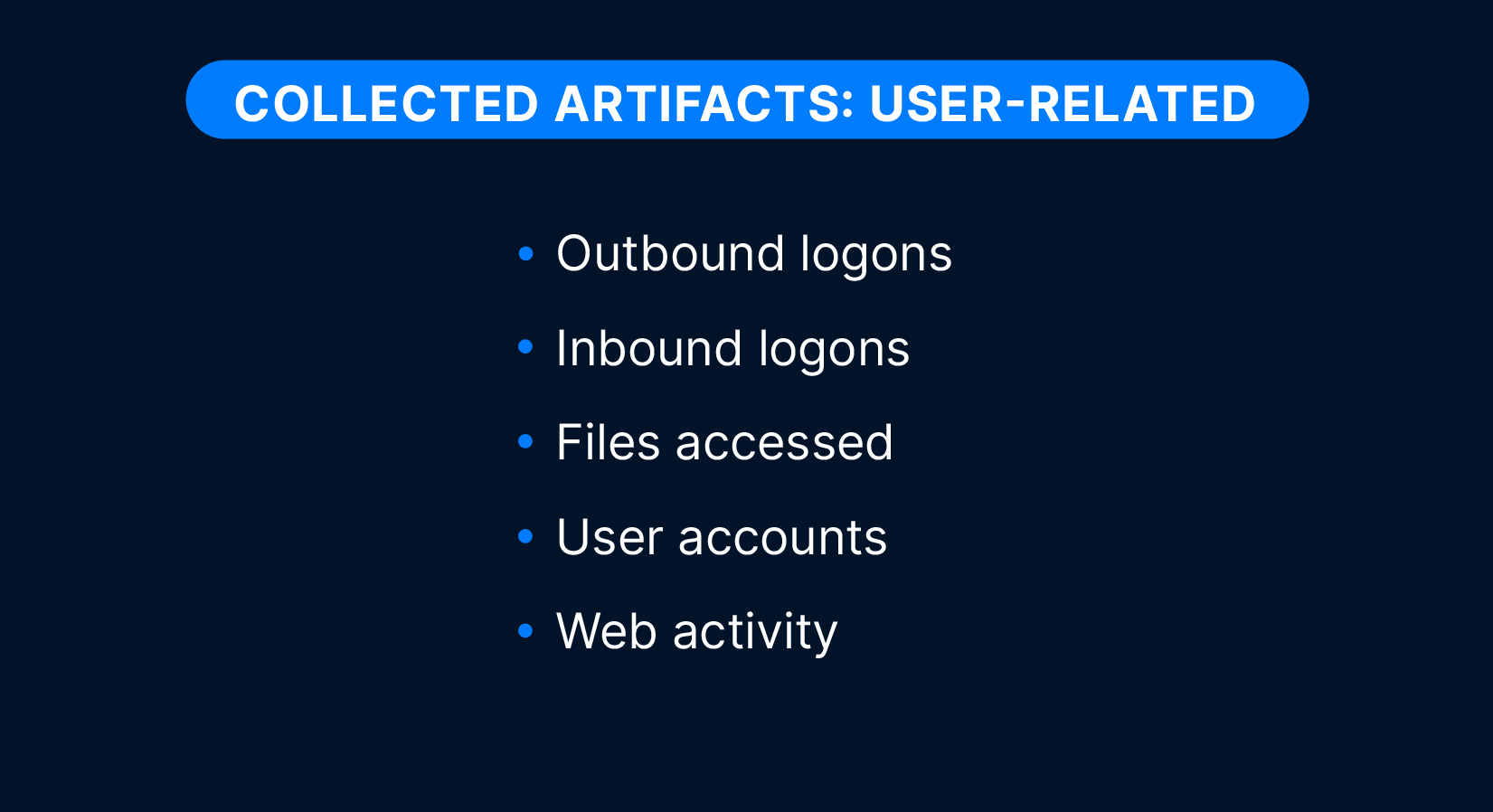
User-related artifacts:
- Outbound logons
- Inbound logons
- Files accessed
- User accounts
- Web activity
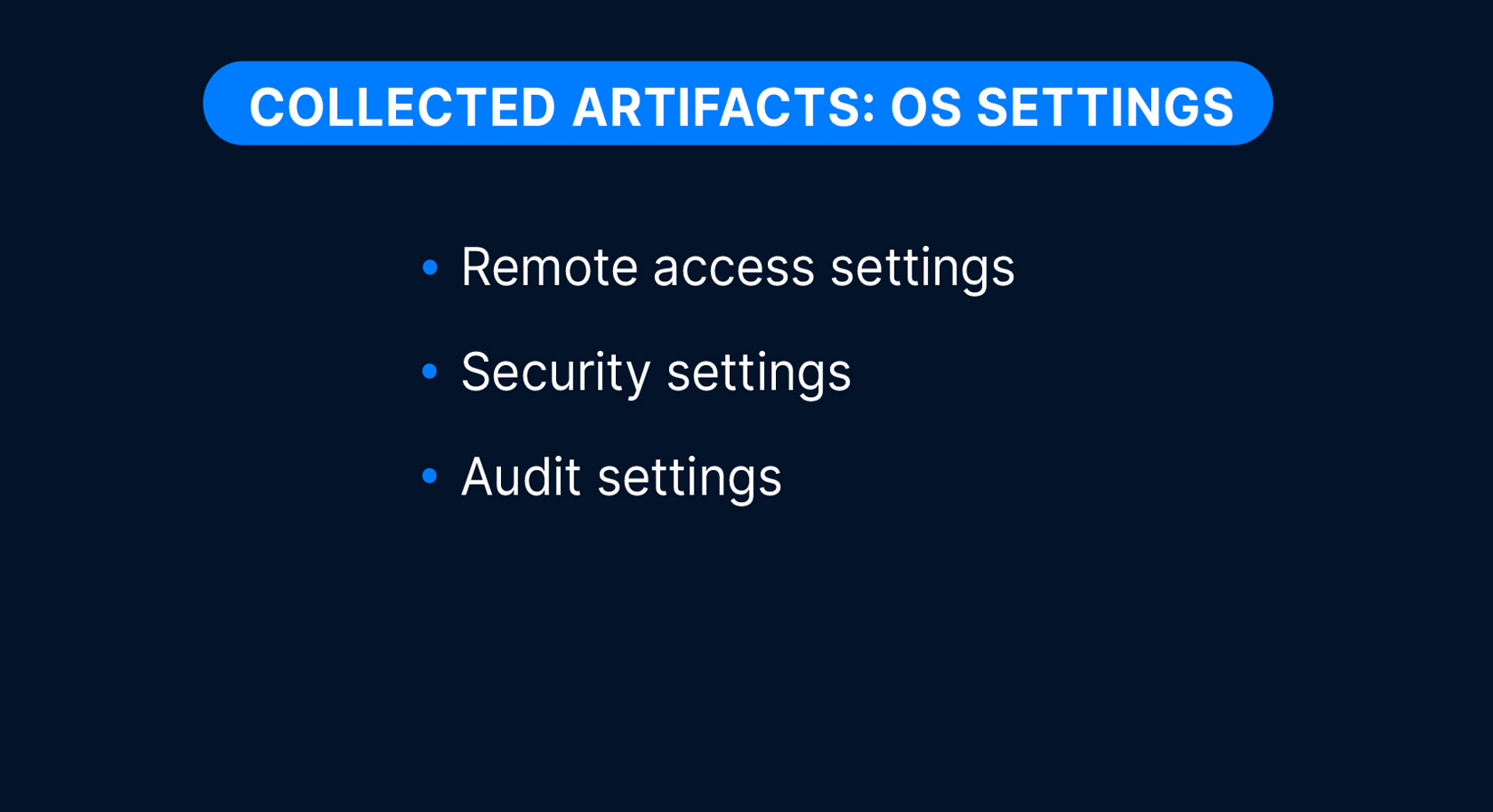
OS settings artifacts:
- Remote access settings
- Security settings
- Audit settings
File content artifacts:
- All source files (registry hives, event logs, etc.).
- All executables used by the system.
- All file metadata from NTFS MFT.
- All recently created files.
Yes! You can export all the collected files into a ZIP file for analysis with any other forensic tool.
The Collector is free to use with no limitations. You can get a copy of it (and the free version of Cyber Triage) here: https://www.cybertriage.com/download-lite/
The executable is a Windows command-line program (single file) designed to run on Windows (XP and above). The Cyber Triage can be used to analyze Linux systems by using the Unix-like Artifacts Collector (UAC).
Use an EDR to push and run it (via our Deployer PowerShell script), email/hand it to a user with a simple UI wrapper, or run from a USB/remote share.
You can save to a local file, upload directly to the Cyber Triage Server, or send to cloud object storage (Amazon S3, other S3 cloud services, or Azure Blob).
Yes, enable optional public-key encryption for the output file.
Yes. You can create custom collection rules and rule sets (e.g., to always include specific app logs).
Yes, the Collector accepts command-line arguments or a configuration file. There is also a GUI interface if you want to run it manually. Common options include –fast (skip full FS scan), –dtypes (choose data types), –ruleset_file (extra files to grab), –skip_file_contents (hashes only, no content). Use –help to see all.
Yes. Save to a local file (USB or share) and later import the collection into Cyber Triage. One of the nice features of the Collector is that, by default, you do not need to use any command-line arguments, so you can give the USB to a team of interns, have them run around making collections while you get on with the analysis*.
* Sleuth Kit Labs does not guarantee that the Cyber Triage Collector is 100% intern-proof, but it is as close as possible, as any software can be!
Cyber Triage can be configured to connect directly to your cloud storage, meaning you can load collections from within the user interface without having to mess about downloading and copying files all over the place. It also supports any cloud storage service using the S3 protocol and Microsoft Azure.
Yes! Cyber Triage can ingest many different data formats. Just fire up the full app and add the data directly!
Our Deployer script launches the Collector in the background and can return early so the EDR doesn’t kill the session; platform-specific guidance (e.g., CrowdStrike RTR timeouts, 4 GB pullback limits) is documented.
Yes. The Windows command-line tool also has a simple UI wrapper to make client-driven collections easy. In addition to this, you can pre-configure the Collector so all they need to do is right-click and select “Run As Administrator”.
Yes. Standard Pro, Standard Enterprise, Team, and Team Enterprise editions include the Collector.
You can drive Cyber Triage itself from the command line to create incidents, add hosts, and generate reports. This is ideal for scripted pipelines.
Use the Deployer PowerShell script and the EDR’s script/library features (e.g., CrowdStrike RTR library, Defender for Endpoint Live Response, SentinelOne RemoteOps/RemoteShell).
Yes. Request the Deployer script from our site; it downloads the latest Collector and launches it according to your settings; documentation and platform lists are linked from the download page.
All Standard and Team editions support adding multiple hosts at a time, making it easy to scale investigations.