What Is It?
This event is created by the Remote Connection Manager when there was a successful login and sometimes when there were failed logins (its description can be misleading). The details depend on the OS.
- Event Log: Remote Connection Manager log
- Event ID: 1149
- Event Description: “Remote Desktop Services: User authentication succeeded”
The Remote Connection Manager is responsible for accepting Windows RDP connections and is part of the Remote Desktop Service.
Artifact Family
This event is in the Inbound Logon artifact family. It is related to incoming Windows RDP connections.
When Does It Get Created?
On newer OSes (list is below):
- This entry gets created after the user has entered a valid username and password.
- No entry (1149 or any ID) is created for invalid username and password combinations.
- port139.Hatenablog.com reported that it does not get created with rdesktop as a client and Network Level Authentication (NLA) disabled. We were not able to confirm this scenario, but did confirm that we saw 1149 entries regardless of the NLA setting.
On older OSes:
- This entry gets created whenever a user enters in a username and password combination.
- On these OSes, the event description is then misleading because it says the user was authenticated, but it could have been an incorrect password.
Mike Cary observed that the following created this event only on successful logins:
- Windows Server 2012
- Windows Server 2016
- Windows 7
- Windows 8.1
- Windows 10 (version 1803)
And the following will create 1149 events for failed logins too:
- Windows Server 2008
- Windows SBS Server 2011
What Data Is Stored?
This event has three fields of interest:
- Timestamp of when the login occurred
- User and domain name for account being logged into
- Remote IP address
It also contains a “Correlation ActivityID” that we’ll be able to correlate with events in the TerminalServices-LocalSesionManager log, but not the Security log. Those are the other two log files that contain remote desktop events.
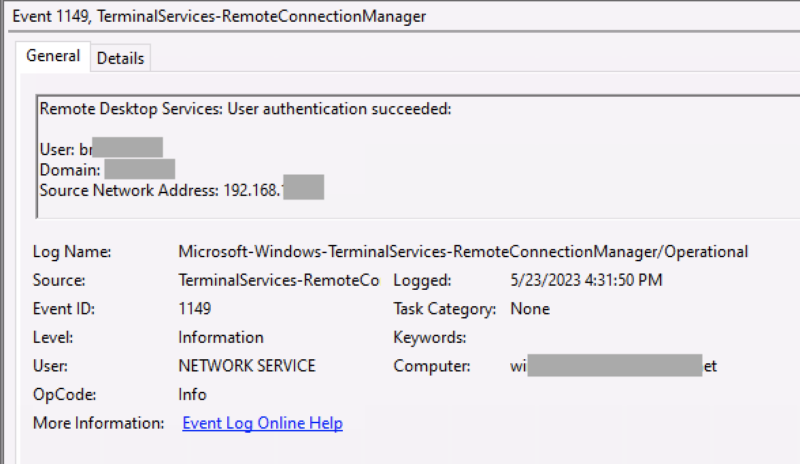
Some special notes include:
- port139.Hatenablog.com reported that the user and domain names are empty if the server is configured with RestrictedAdmin
- Daniel White reported (back in 2015) that data from the RDP cookie was used to populate the user name field in the event and that this could be forged or contain data from a previous host. This behavior was observed when 1149 was created for both failed and successful logons. We have not done a test to forge the RDP cookie, but forged data seem less likely to make it into the event log now that only successful logins are recorded.
Relevance to DFIR?
This event is useful when looking at an attacker’s use of Windows RDP.
In recent OSes, it duplicates data that would also be in the Security log, but the benefit is that data stays longer in the Remote Connection Manager log. So, even if the Security log has overwritten data from an attack, you can still get basic information from the Remote Connection Manager log.
Unfortunately, this log file will not indicate failed logins.
Sources
- https://ponderthebits.com/2018/02/windows-rdp-related-event-logs-identification-tracking-and-investigation/
- http://blog.kiddaland.net/2015/02/remote-desktop-connections-terminal.html
- https://dfironthemountain.wordpress.com/2019/02/15/rdp-event-log-dfir/
- https://port139.hatenablog.com/entry/2019/03/23/091740
- https://digitalforensicsurvivalpodcast.com/2023/01/31/dfsp-363-rdp-forensics/
- https://learn.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2008-R2-and-2008/ee907328(v=ws.10)?redirectedfrom=MSDN



