KAPE is a popular tool for collecting files from a suspect system. In this blog post, we’re going to show you how to use Cyber Triage to efficiently analyze your KAPE outputs. Cyber Triage will score the artifacts and highlight ones you should focus on first. We’ll also talk about how our collection tool is different from KAPE so that you can decide which one you want to use.
This blog is also useful if you use Velociraptor and output data in the “KAPE Format”. That too can be imported into Cyber Triage.
KAPE Basics
The Kroll Artifact Parser and Extractor (KAPE) is a set of command line tools and scripts that allow an incident responder to collect artifacts from a target system. It’s development has been led by Eric Zimmerman and is taught in several SANS courses.
From their website:
“With KAPE, you can find and prioritize the most critical systems to your case and collect key artifacts before imaging. This means no longer having to wait until full system images are gathered and then wading through data where typically less than 10% will have any forensic value.”
There are two primary methods that KAPE uses to collect data:
- A set of files and directories are collected based on paths in configuration files (called targets)
- Command line tools are run that can extract or parse additional data. For example, PsList from SysInternals could be called to collect information about running processes.
The results are all saved to a single location and bundled into a container:
- Logical folder structure
- ZIP file
- VHD file
KAPE can be used for free for internal corporate, law enforcement, and academic use. A commercial license is required for consultants.
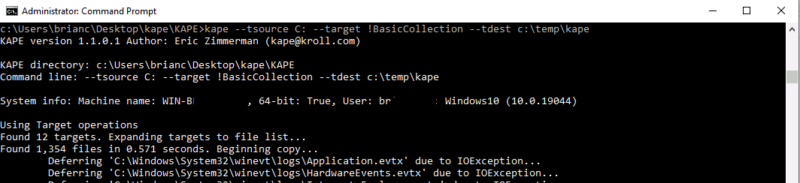
Here’s an example of running KAPE:
KAPE vs Cyber Triage Collection Tool
As you may know, our Cyber Triage application has a program called the Collection Tool that runs on target systems and it also collects files and artifacts. So, you may be wondering how KAPE and the Collection Tool are different.
The two tools have similar goals and overlap, but there are a few key differences and each has its own strengths:
The Cyber Triage Collection Tool strengths include:
- The Collection Tool collects more executables. It parses registry keys and other files so that it can collect the corresponding executable, dll, or referenced file. For example, it will collect the “AutoRuns” executables for malware analysis. KAPE can run the AutoRuns program and show the list of paths and it will copy the entire registry hive, but it will not copy the specific executables that are run when the system starts.
- The Collection Tool is a single executable with minimal dependencies that is easy to move around and launch. KAPE has several files and requires .NET.
KAPE strengths include:
- The KAPE output is easy to use in other post-processing tools because the output is a logical file set. Any tool that can take in logical files, a ZIP, or VHD can process the results. With Cyber Triage, you have to use a report module to convert to such a folder-based structure. The Collection Tool output is a JSON file.
- KAPE is more user-extensible. KAPE uses a set of text-based configuration files to specify what gets copied or run, which makes it possible for users to create their own set of files and share them. The Cyber Triage Collection Tool allows the user to specify artifact categories (such as Startup Items or Processes), but not specific artifact locations.
While not the point of this article, we are working on adding similar extensibility into the Cyber Triage Collection Tool.
Cyber Triage Adds Analytics to KAPE
While we think our collection tool is very powerful, we want to support people who are already using KAPE. After all, the real value of Cyber Triage is its scoring ability and how it can prioritize what specific artifacts are anomalous and you should review.
Instead of getting a list of thousands of artifacts to start looking at, Cyber Triage gives you a starting point of a small subset to focus on.
A few months back, we added the ability to import KAPE data into Cyber Triage. This means that you can continue to collect with KAPE and then leverage the Cyber Triage analytics to start the investigation.
For example:
- Flag startup items that are running out of anomalous locations
- Review inbound logins for lateral movement
Using KAPE With Cyber Triage
Now that we’ve agreed that Cyber Triage is a great way to take KAPE data to the next level, let’s go over how to do it.
Specifying the Correct Targets
First, let’s make sure that you run KAPE with the appropriate arguments and targets so that as many of the Cyber Triage analytics can be used. While no KAPE targets collect all of the files that Cyber Triage can process (we may make one that does), we recommend you use the BasicCollection or SANS_Triage targets. These collect the registry hives and event logs that are needed.
For example, something like:
C:\> kape --tsource c: --target !BasicCollection
NOTE: Cyber Triage can process the VHD output faster than a logical file set, so if given the choice, we’d recommend outputting in VHD.
Importing the Data
Once you have your files, move them to the computer running Cyber Triage. If you collected it as a ZIP file, then you should extract the ZIP file contents to a folder.
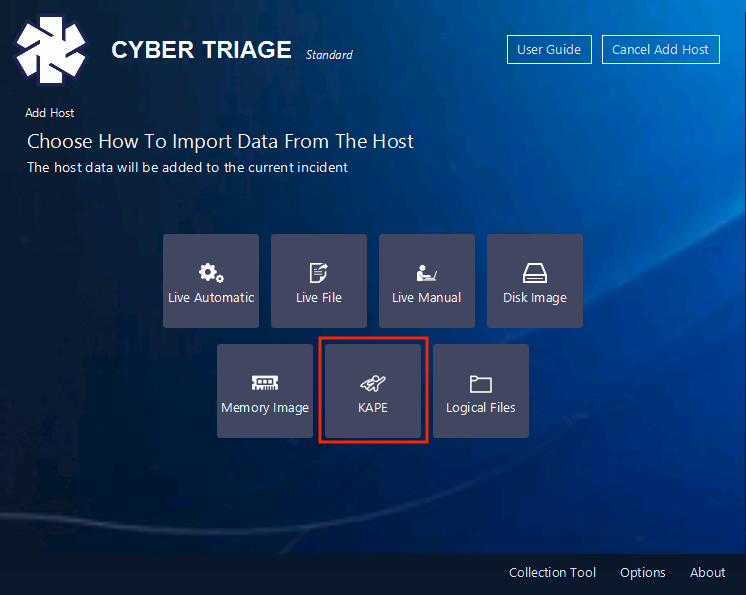
Create a new incident (or use one you’re already working on) and choose “Add Host”. Then choose the KAPE” target.
NOTE: Do not use the “Logical File” option because it will not know how to map KAPE’s special way of storing long file names.
On the next panel, specify the path to the VHD or exported ZIP file contents. If you import a logical folder, you should see a “C” folder.
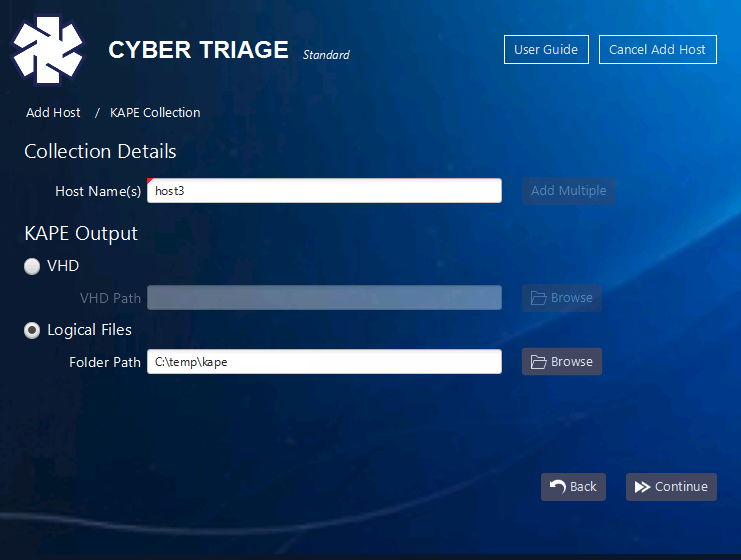
You’ll then be given options about what kinds of data to extract from the registry hives and event logs.
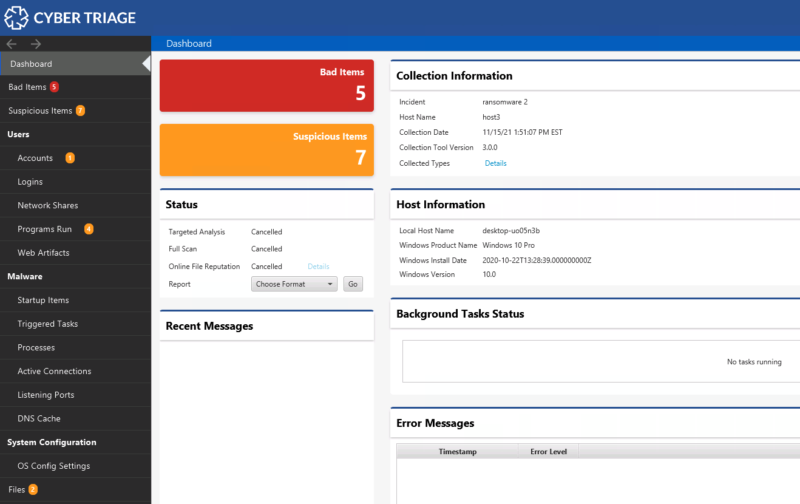
As data is added, it will be scored and shown on the dashboard. You can then review the Bad and Suspicious items.

Current Limitations
There are some important caveats to call out when using KAPE and Cyber Triage
- Because KAPE doesn’t collect as much file content, you will not be able to take advantage of the malware scanning that comes with Cyber Triage. So, if a malicious startup item is located in a standard Windows folder and has a normal looking name, then it will not be as obvious that it’s malicious.
- The lack of malware scanning also means that you’ll see more suspicious items (as false positives) because the malware scanning isn’t able to “downgrade” a suspicious file as being Good.
- Cyber Triage currently (as of version 3.6 – January 2023) does not parse any of the KAPE module output. It parses only the registry hives, event logs, and other files included in the target.
- You may see some warnings about missing files because Cyber Triage tried to locate a file that was not collected.
Conclusion
We want to make sure people can get scoring with whatever collection method they choose. We’ll be expanding support in the future to import other tool outputs (such as SysInternals). To try Cyber Triage, use this form for a free 7-day evaluation.



