In addition to account takeover and installing malware, attackers may also make changes to the computer’s operating system to ensure that they can retain access and avoid detection. In this post of our “Free DFIR with Cyber Triage Lite” series, we’re going to focus on looking for those settings with Cyber Triage Lite.
You’ll want to read this article if you are looking for a free DFIR tool that gives you a UI to review your collected data and generate reports.
Previously in this series, we focused on how to collect data using Cyber Triage Lite and how to use the UI to review user accounts and malware . This post is all about OS Configuration Settings.
You can download Cyber Triage Lite from here.
Divide and Conquer DFIR Process Review
Before we dive into the details of the Cyber Triage Lite UI, let’s review the Divide and Conquer DFIR process, which is how we approach digital investigations. You can skip this section if you’ve already heard us talk about this.
The basic concept is that you’ll start with an investigative question (such as “what did the attacker access”?) that is often hard to answer. The solution is to break it into smaller and smaller questions that can be answered with a single type of artifact. It uses the basic problem-solving technique of breaking a hard problem into smaller and easier problems.
As several of our previous posts and videos have outlined, we often break the questions down into groups about:
- Users: Was there suspicious user activity?
- Malware: Were there malicious programs?
- OS Configuration Settings: Were there malicious system changes?
Each of those is further broken down (we’ll break down users in the next section).
That’s the gist at the high level. To learn more, refer to:
- Blog Series
- Online Video Course (3-hours)
What is Cyber Triage Lite?
To make sure all readers are starting from the same place, let’s also quickly review Cyber Triage Lite. Cyber Triage Lite is the free version of Cyber Triage. It uses the same Collection Tool, but it doesn’t have the analytics and scoring features of Cyber Triage Standard. For example, you’ll get the same UI as Cyber Triage, but it won’t have items marked as Bad or Suspicious.
The main advantage of Cyber Triage Lite over other free DFIR tools is the UI. There are other free collection tools, but they give you a list of text files to review. Cyber Triage Lite gives you a UI to navigate and pivot with. That’s what this series is about.
Why We Look For Operating System Changes
In addition to malware and user accounts, your investigation will also want to look for OS configuration changes because it is another way that attackers retain access to your environment. For example, they may enable remote access or disable security settings.
The Cyber Triage UI has a single location for all OS Configuration settings, but it has a ‘type’ column to map out what “Divide and Conquer” question it answers.
Notably, we break the question of “Were there malicious system changes?” into the smaller questions of:
- Are there remote access changes that make it easier for the attacker to retain access?
- Are there security changes that could prevent the attacker from getting detected?
- Are there audit or backup changes that could prevent data from existing that would help in the investigation and recovery?
- Are there process loading changes that allow the attacker to inject malware?
- Are there networking changes that allow the attacker to reroute or monitor traffic?
Reviewing OS Configuration Settings
OS Configuration Settings are a bit different in Cyber Triage than other data types because there is not a distinct section for each investigative question. Instead, all of the settings are listed and there is a column for the type of question it helps to answer.
You can find the settings with the “OS Config Settings” menu item.
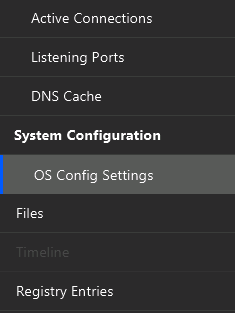
The table in the upper right will list out all of the collected settings and the first column identifies which investigative question the setting applies to.
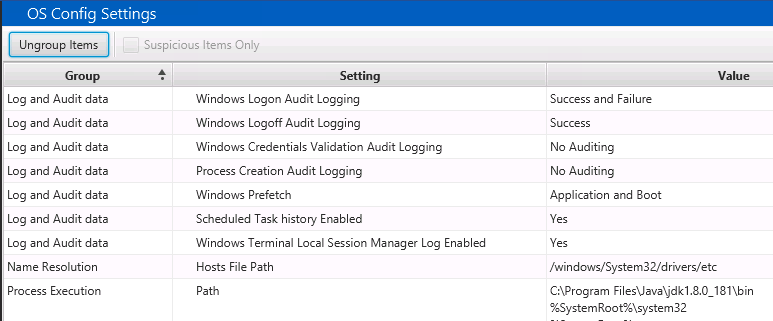
If you are unsure why a setting is relevant or what it means, you can refer to the bottom and many will have settings for the purpose, relevance, and default value. For example, here is the data for the Login Audit settings:
If you want to manually score any setting as bad or suspicious, then you can use the “Mark Item As” option like we saw in previous posts. This will cause the item to be added to the final report.
We can now review each of the types of investigative questions in more detail.
Log and Audit Data Settings
The “Log and Audit Data” group of items answers questions about “Are there audit or backup changes that could prevent data from existing that would help in the investigation and recovery?”.
You can review these settings to determine what will be in the audit logs. For example:
- Logon Audit: This shows if logins will be logged when successful, failed, or never. Different versions of Windows have different default settings for this. Knowing what the setting is can help figure out why you are not seeing logins.
- Logoff Audit: This shows if log-offs are logged.
- Process Creation Auditing: This shows if there will be a log entry for each new process that is launched.
- Windows Prefetch: This shows if Prefetch is enabled on the system, which will help determine which applications were run.
The paid version of Cyber Triage will identify some of these settings as suspicious if they are not the default values.
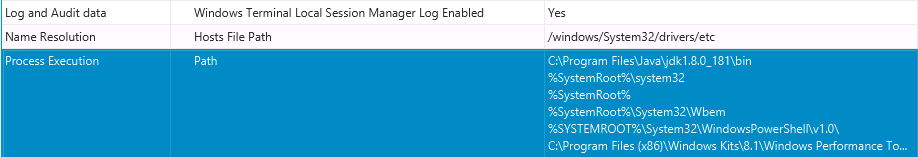
Network Name Resolution Settings
The “Name Resolution” group answers questions about “Are there networking changes that allow the attacker to reroute or monitor traffic?”. Here, you will find the path to the hosts file. The host file is also collected, so you can then go review that under the “Files” area.
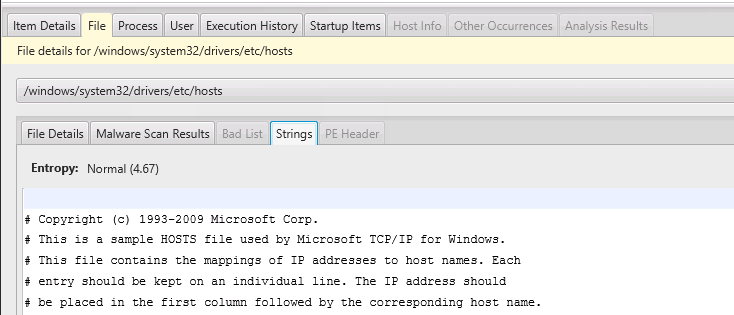
The paid version of Cyber Triage will flag this file if it has non-standard settings.
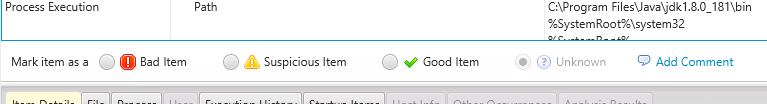
Process Execution Settings
The “Process Execution” group answers questions about “Are there process loading changes that allow the attacker to inject malware?”. Here you will find the Windows PATH environment variable that is used to:
- Locate executables when the full path is not give
- Locate libraries to load
You can review this string to look for suspicious folders that are added before the Windows folder entries. Attackers do this so that their programs or libraries are launched before official Windows files.
Remote Access Settings
The “Remote Access” group answers questions about “Are there remote access changes that make it easier for the attacker to retain access?“. Here you will find the setting about if the Windows Remote Desktop feature was enabled.
Note that the attacker could install other remote access tools, which you may see listed in the “Startup Items” section. This section just includes the official Windows remote access feature.
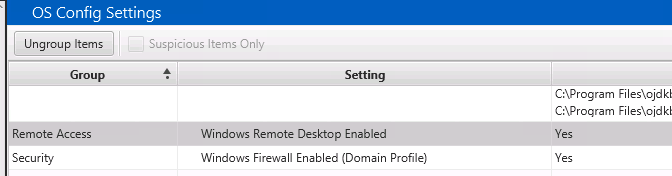
Security Settings
The “Security” group answers questions about “Are there security changes that could prevent the attacker from getting detected?”. Here you will find settings about Windows Firewall, Windows Defender, and Task Manager.
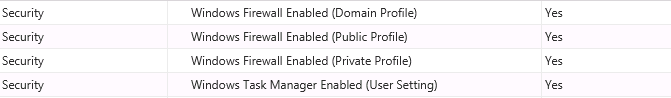
You can determine if they are enabled or not, but keep in mind that sometimes the Windows Firewall is disabled because there is a different firewall in use.
Conclusion
OS Configuration Settings are a critical part of an investigation to ensure that you know what changes were made and what security settings may have existed before the incident. Cyber Triage Lite has features dedicated to the review of OS Configuration-related artifacts. If you’d like to try it out, fill out this form here.

