Organizations need to be able to respond to alerts and investigate their computers, but not every organization has an incident response budget or dedicated personnel. The newly released Cyber Triage Lite helps these companies by providing a free method for collecting and viewing data from endpoints.
This post covers what is included in Cyber Triage Lite and a brief comparison with some SysInternals tools
What’s Inside
The quick answer is that Lite version of Cyber Triage does not include the automated analytics that the normal version has. For example, it doesn’t include malware scanning, flagging of suspicious items, or incident-level grouping. The table below summarizes the differences:
| Capability | Cyber Triage Lite | Cyber Triage Standard |
| Collection of volatile data, user activity, startup files, etc from USB drive, local execution, or disk image. | X | X |
| View the collected data and mark each as good or bad | X | X |
| Pivot between data types to understand the full scope of the incident. | X | X |
| Threat timeline to show when bad events occurred on this endpoint. | X | X |
| HTML Report that shows the bad and suspicious items. | X | X |
| Push collection tool to remote host as needed. | X | |
| Group and correlate endpoints by incident. | X | |
| Automated analysis to identify bad and suspicious items. | X | |
| Correlates items with previous sessions to determine how common or rare it is and if it was previously marked as bad. | X | |
| Blacklist to identify known bad items and whitelist to ignore known good items. | X |
Typical Workflows
With these features, a typical company would use Cyber Triage Lite in the following way:
- Run the collection tool from a USB drive on the endpoint and choose to either send data over the network or to the USB drive.
- In the Cyber Triage interface, review the collected data and mark processes, ports, remote desktop connections, network shares, etc. as good or bad based on their knowledge of the target endpoint. Use the threat timeline as a reference to remember when other bad events occurred.
- Generate a HTML report with the items that were marked as bad.
Comparison
Let’s look at an example of using some of the free SysInternals tools to respond to an incident versus the free Cyber Triage Lite.
Cyber Triage Scenario
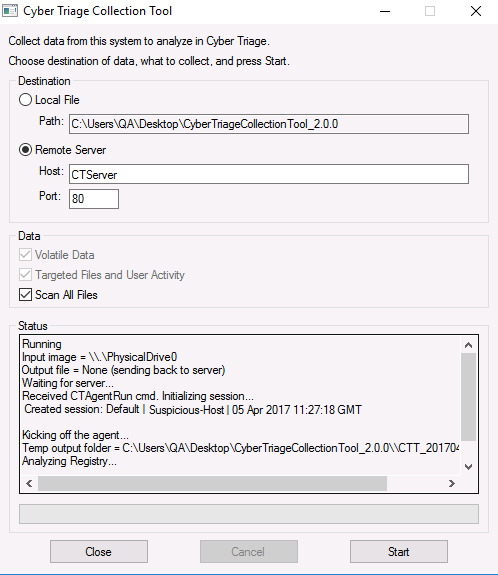
Let’s assume we have an alert about an endpoint and want to investigate it. When using Cyber Triage Lite, we copy the UI-based collection tool to a USB drive and send the data to a security-team laptop running Cyber Triage. The UI-based collection tool is shown here (there is also a command line-interface version):
As the data is being sent back to Cyber Triage, we select the Processes tab and identify a suspicious MSUpdater.exe process based on its “AppDataTemp” path.
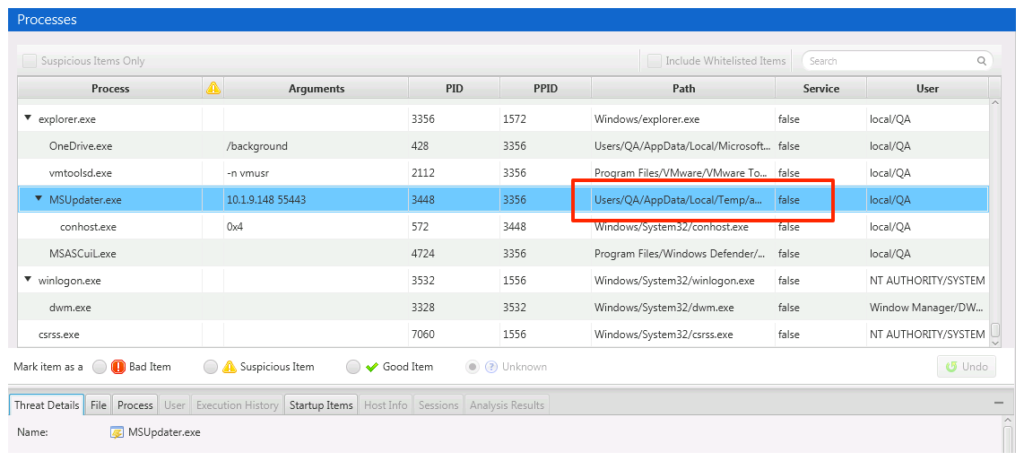
We want to know more, such as if it was automatically started at boot up or if a user may have started it. We go to the bottom of the window and choose “Startup Items” and see that it is started from a registry (we’ll be updating this table to list the specific key).
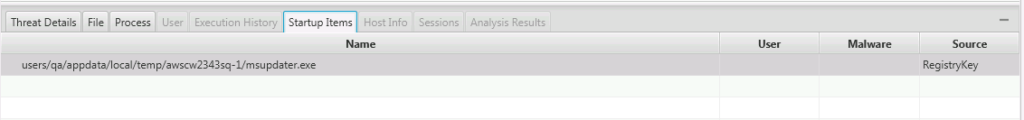
This now becomes much more suspicious because startup items aren’t typically in Temp folders. To see if it has network connections we change the bottom tab to go to Active Connections and see that it has an outbound connection.
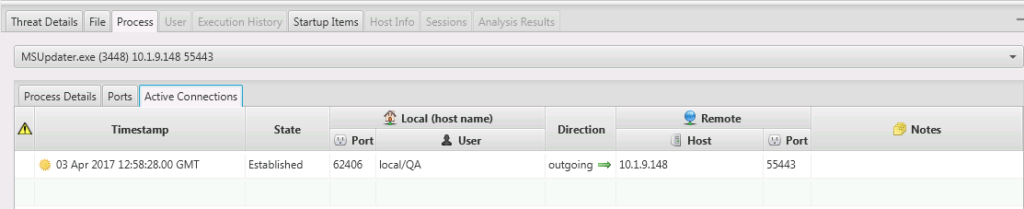
We also have access to the file’s 8 NTFS time stamps, strings, and other metadata to help make a conclusion about the process and file. If we conclude that this process is bad, then we mark it as bad in the Cyber Triage UI.
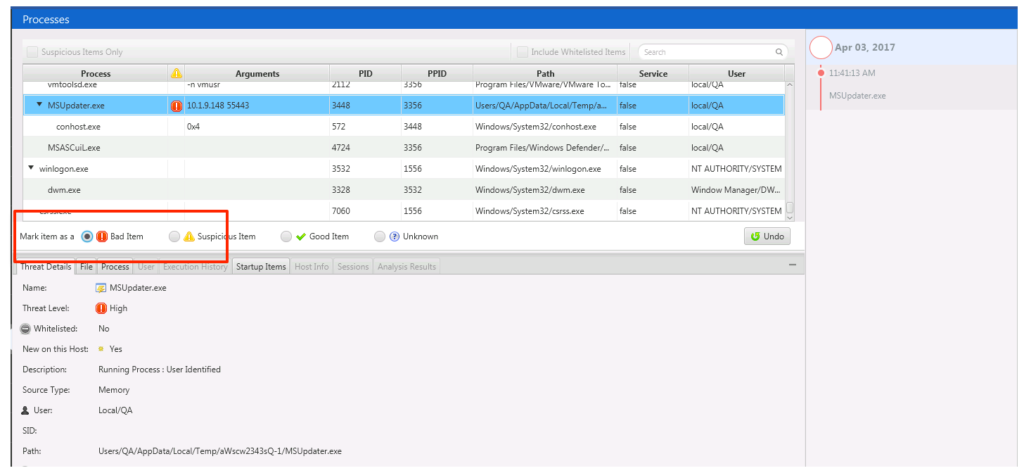
When we mark it as bad, it will get added to the timeline and included in the final report, an example of which is given here:
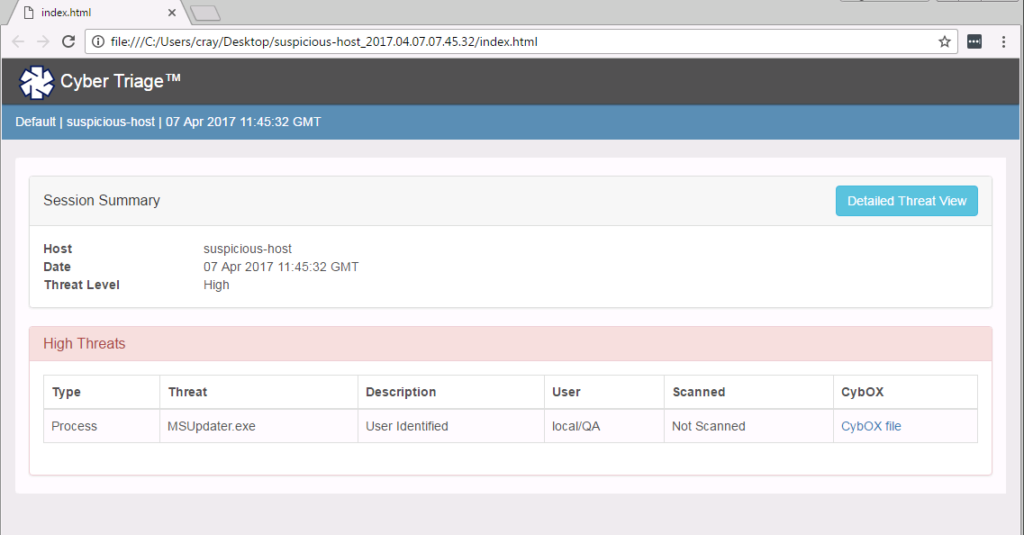
SysInternals Scenario
Let’s look at the same scenario with SysInternals, which are a collection of command line and graphical interface tools from Microsoft. During an incident response, you would use several of the tools to collect the data you need.
If we wanted to repeat the above scenario, we have to choose between two approaches. We can run command line tools to collect data and then analyze it elsewhere or run the Process Explorer graphical program and interact with it on the target system.
Let’s first look at the command line approach. We can run ‘pslist’ to see the processes. In this view though, we do not know the full path to know that process MSUpdater.exe is suspicious.
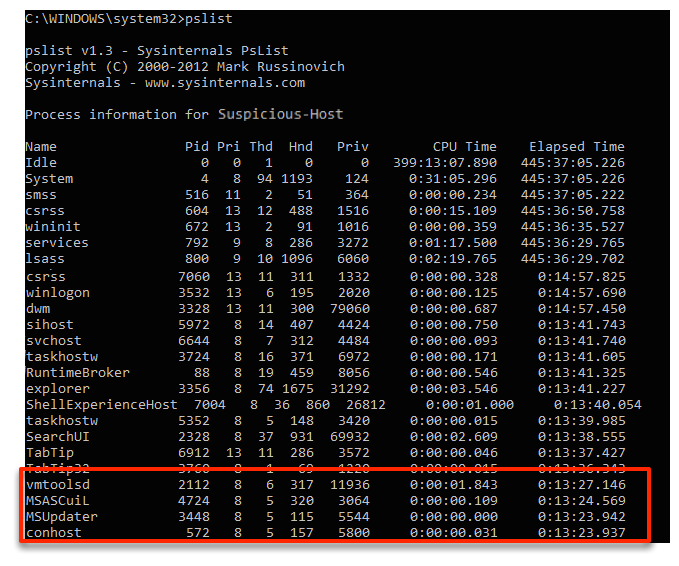
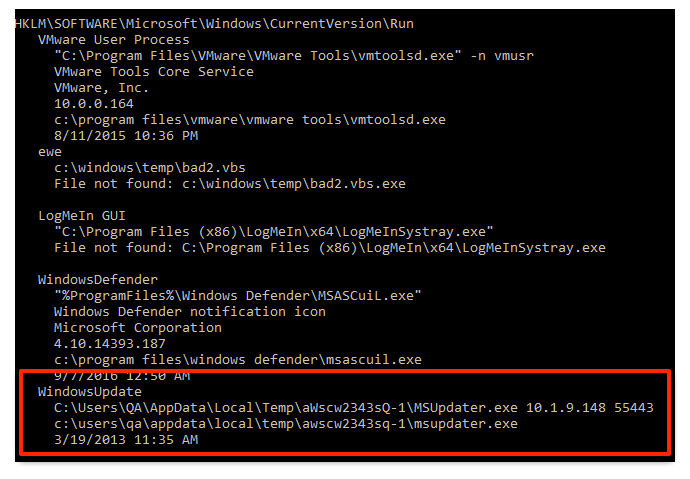
But, let’s say that we do know that it is suspicious. If we want to see if it was automatically started, we need to then run the ‘autoruns’ program, which produces over 8,000 lines of text output, and search for the string “MSUpdate.exe”. We can see that it was started from the Run key.
If we want to profile the process more, we can run ‘netstat -ano’ and search its text output for the process Id of MSUpdater.exe to see if it has active network connections.
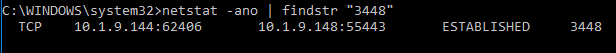
So, we can get similar data as we got with Cyber Triage, but it involves going to different tools with different command line arguments and searching the output for IDs and names. It requires the user to remember a lot of things.
Alternatively, we could launch the ProcessExplorer program on the target computer and do the analysis by interacting with the endpoint. When we run it, we see this:
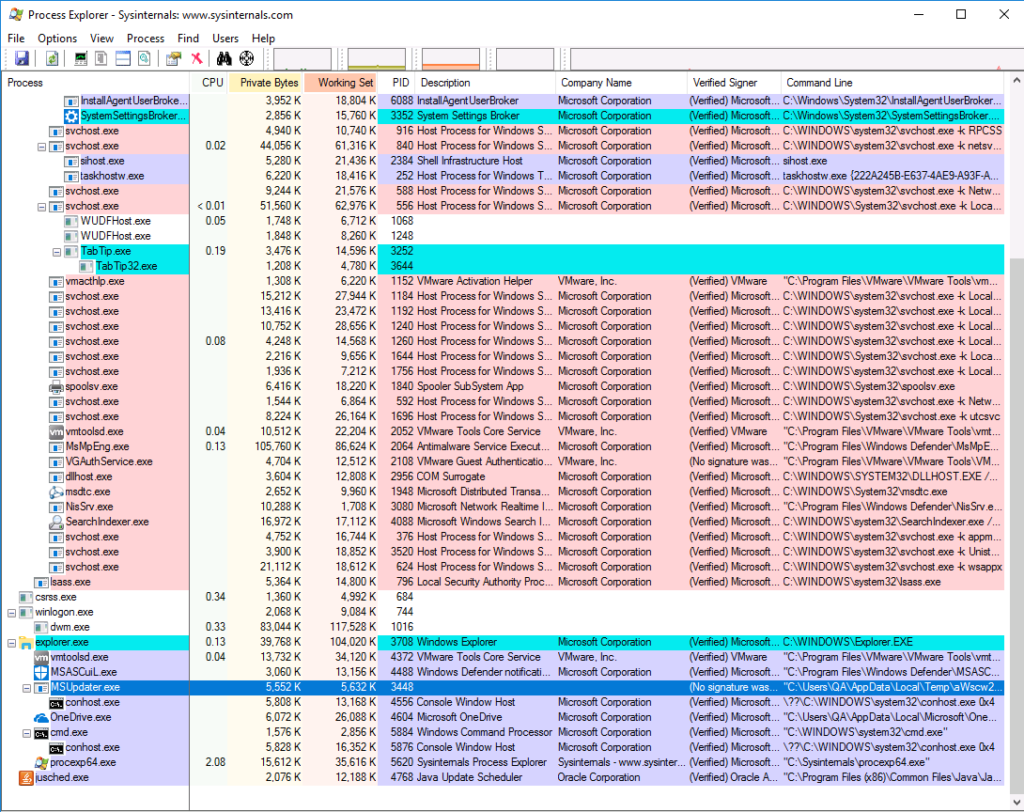
From there, we can see the suspicious process MSUpdater.exe. From the process, we can see process details and see the active connections, but not if it was a startup item.
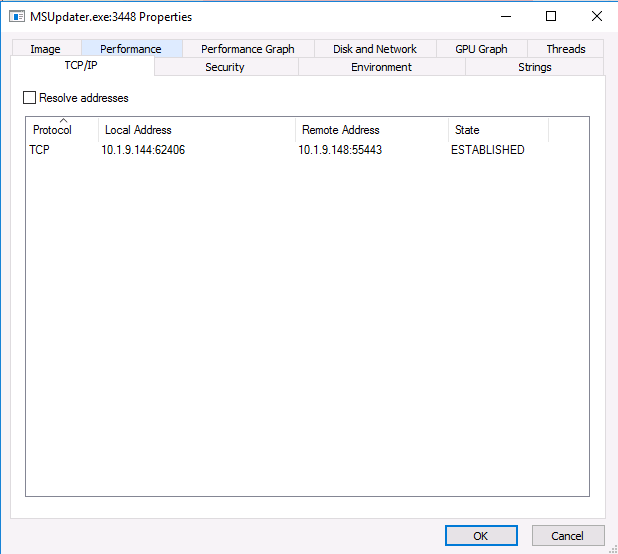
But, once we identify the process as being suspicious we have no way of recording that in the software or making a final report. This program also doesn’t show us anything about remote logins, DNS cache, network shares, and other data types that Cyber Triage collects and views.
In summary, while the SysInternals tools can be very useful, the command line tools take a lot of effort to match outputs from the various tools and the graphical interface tools do not have the same breadth or have reporting features.
Try it Out
Cyber Triage Lite gives companies a basic collection and review capability for free. If you want to use it, fill out the form and you’ll get a download link. For a limited time, you’ll also get 7-days of the paid features after you install it. If you want to see some data that you don’t think is being collected, add a comment here or send an email to support cybertriage com.