Remote logons are important to investigate during any intrusion, but they can also be complicated because Windows records so many events about specific phases of the logon session.
The volume is both good and bad. Good because you can get details when you want it, and different log files cycle through at different rates. Bad because it can be hard to piece all of them together.
The Cyber Triage team spent a lot of time this past year looking at logons so that we could create a new concept of inbound and outbound logon sessions in 3.4. We’re doing a blog series to cover all of the various sources of Inbound logon events.
This first post will give an overview of the series and then some links to events in the RemoteConnectionManager log.
Inbound Logon Sessions
As part of the effort to make logons easier in Cyber Triage, we defined a concept of a logon session (separate from the Windows session boundaries). Our inbound logon sessions:
- Start with a connection and authentication attempt
- End with a disconnect or log off
There are many events in the RemoteConnectionManager, Security, and LocalSessionManager log that we use to create the start and end of a session.
Our goal is to represent a single logon session with a start time, end time, and remote IP. An example is seen here:
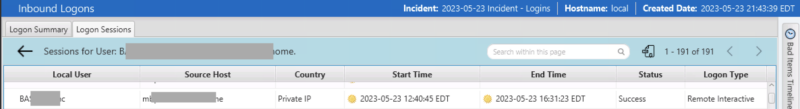
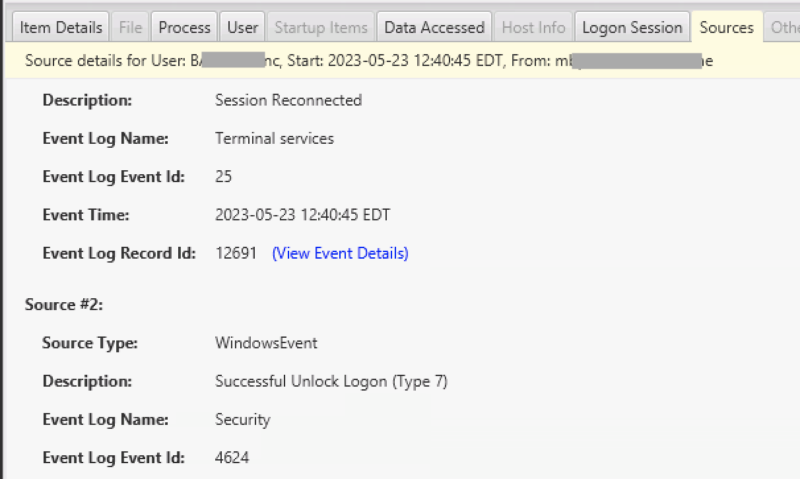
We want to hide the details of the various events, unless you really want them, in which case they are under the “Sources” tab.
Series Plan
- We’ve launched a page and posts about the RemoteConnectionManager log and two of its events 261 and 1149.
- We’ll soon launch content about the LocalSessionManager.
- We’ll then launch Security-log related content
Brian Carrier will also be at TechnoSecurity in June, talking about logons and how to investigate them.
Try Cyber Triage’s Support for Logons
If you are struggling with the number of events around inbound logons, try out Cyber Triage and see how it will merge events from different sources. This approach makes it easier for you to identify who is coming into a system and from where without having to look in multiple event logs.
Try out the free 7-day evaluation today.