Skip to content
Cyber Triage 2.12: Online File Reputation Service is Released
March 24, 2020
Start Reading
Intro to Incident Response Triage (Part 6) in 2019: Malware Persistence
August 22, 2019
Start Reading
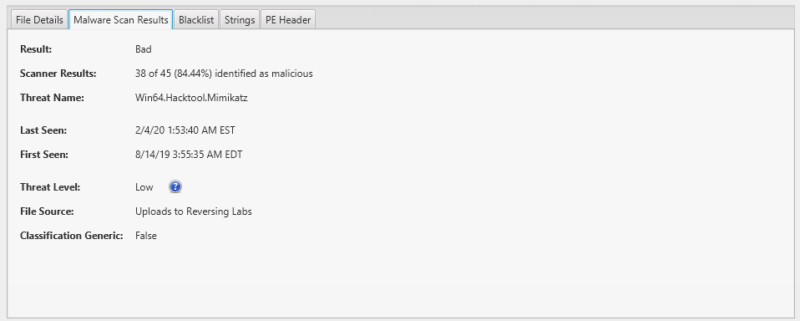
ReversingLabs Integration Improves Malware Scanning
January 15, 2019
Start Reading
Finding Suspicious Program Activity
September 14, 2016
Start Reading
Dig Deeper: Find More IOCs and Fast Flux Domains
July 21, 2016
Start Reading
Make Better Use of IDS Alerts for Incident Response
February 18, 2016
Start Reading
What is in your CSIRT First Responder’s Jump Kit?
February 24, 2015
Start Reading