Cyber Triage is trusted by global organizations committed to security
The Leader in DFIR Artifact Scoring
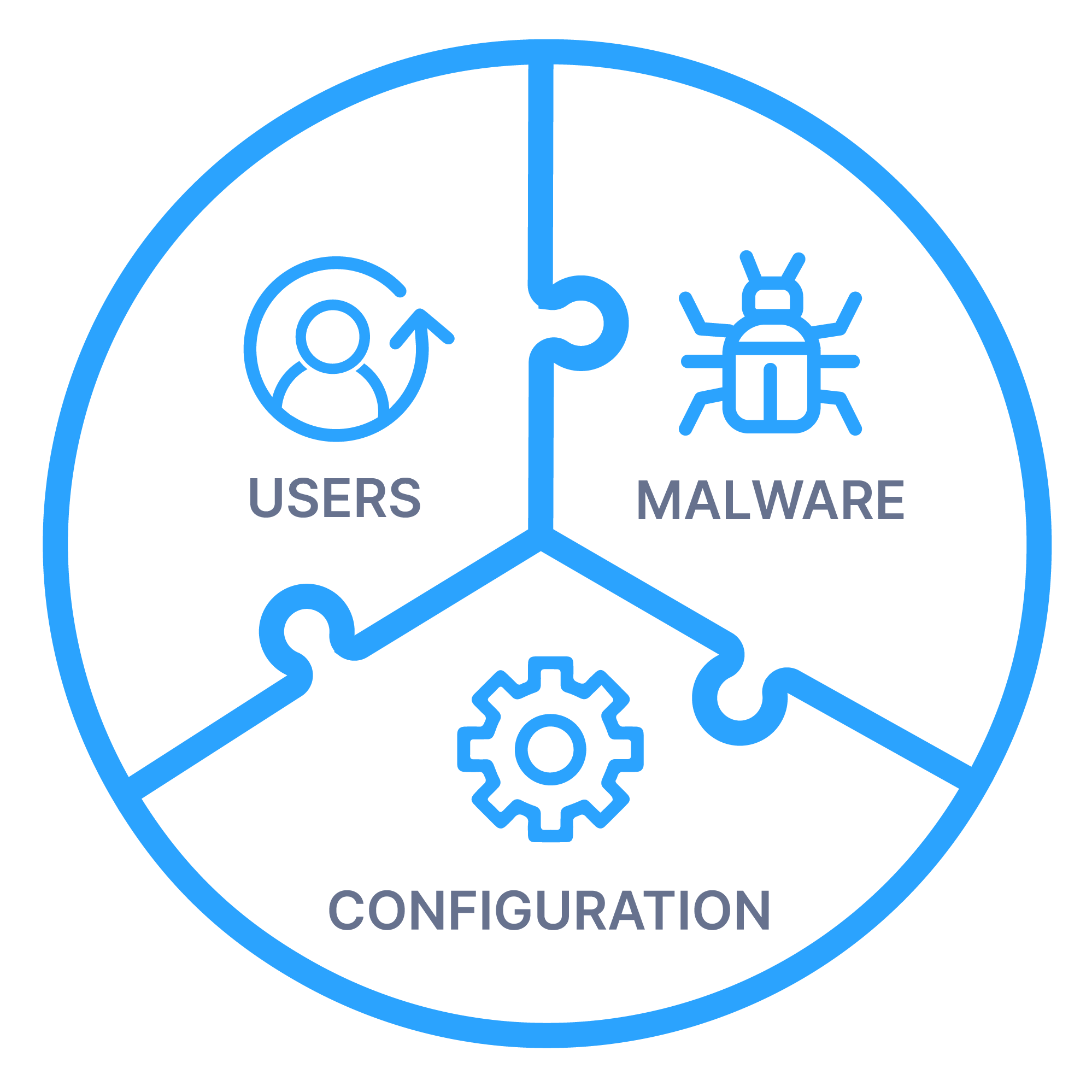
Cyber Triage is the only DFIR tool that will:
- Score artifacts to ensure you quickly focus on relevant data
- Scan executables with 40+ malware detection engines
- Deploy in challenging environments where agents can’t be used
- Recommend artifacts to ensure you follow up on all leads
SOCs, MSSPs, consultants, and law enforcement all use these features to answer their hard investigative questions, such as “What did the attacker do?” and “How did they get in?”.
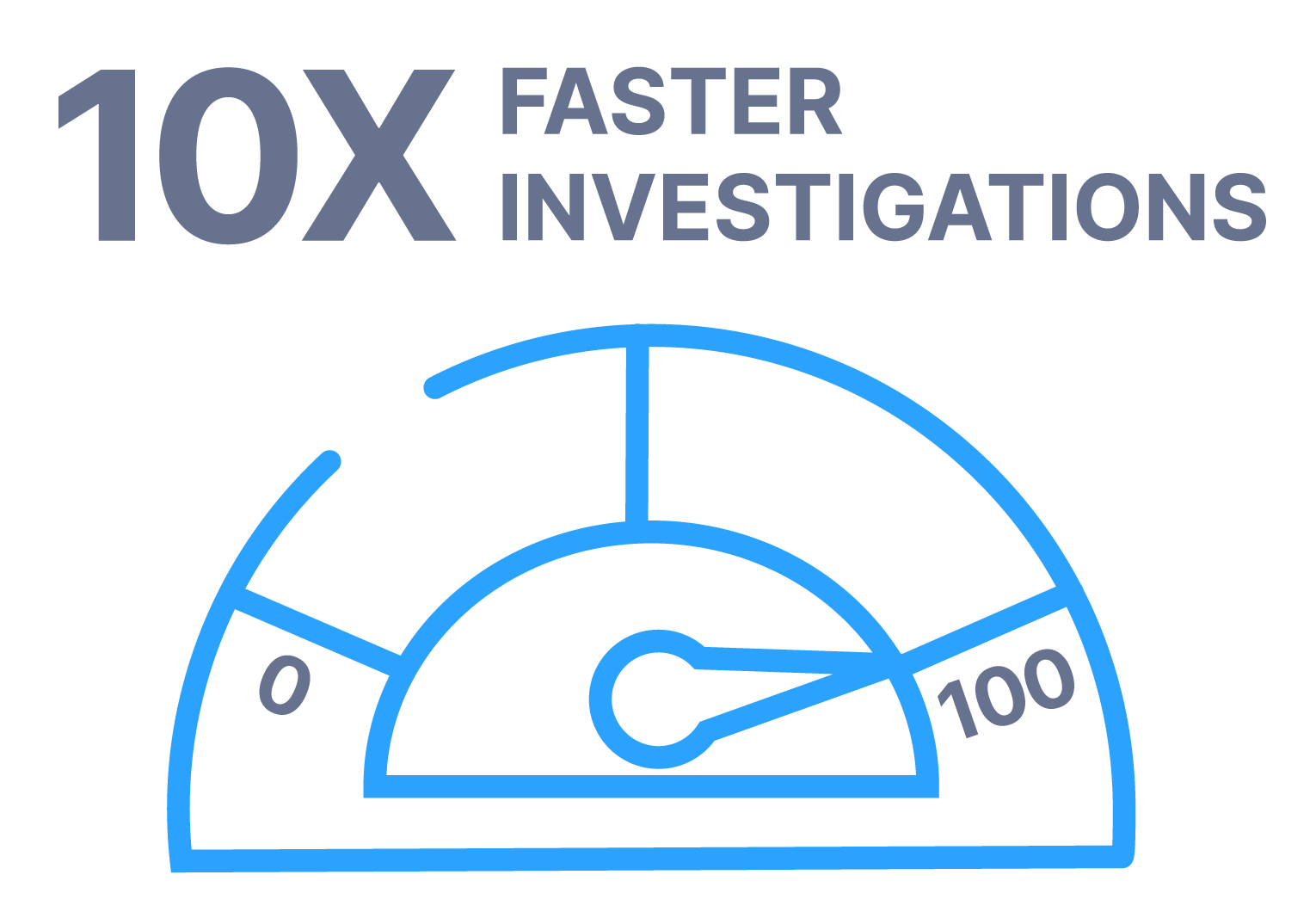
Complete Your Investigations Faster
Speed is critical to ensure you get the evidence before it is overwritten and you minimize the damage an attacker can do.
Cyber Triage maximizes the artifacts per second you process by:
- Identifying the artifacts that are relevant and showing them first.
- Recommending artifacts so that you quickly follow all leads.
- Integrating with SIEMs so that collections start ASAP.
Conduct More Comprehensive Investigations
Investigations need to be comprehensive to understand the full scope of the incident and remove the persistence mechanisms.
Cyber Triage gives you breadth by:
- Collecting dozens of artifact types based on numerous attack scenarios.
- Analyzing executables with 40+ malware scanning engines.
- Using threat intelligence to update collection methods and heuristics.
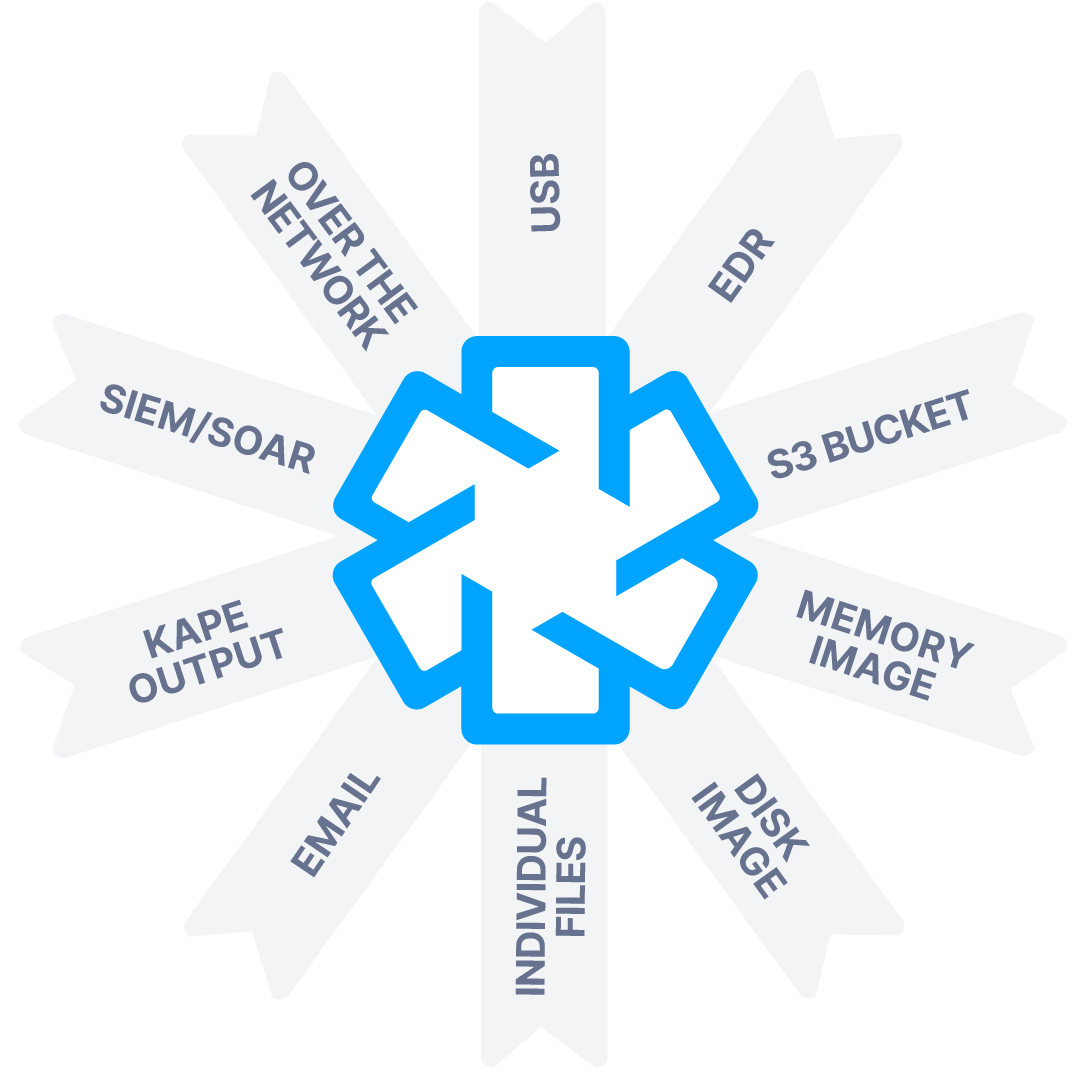
Flexible Deployments
Investigations using Cyber Triage have four basic steps:
- Data is collected using an agentless collection tool that sends artifacts over the network, to USB, or S3.
- Artifacts are analyzed and scored using threat intelligence. Correlations are made between hosts.
- Responders review the artifacts and dive deeper based on what questions they need to answer.
- Additional hosts are collected from and added to the incident.
Cyber Triage has been designed to work in any scenario a Cyber First Responder finds themselves in. It can run on a laptop, the cloud, or an on-premise server.
Learn How to Answer Intrusion Questions in Our 3-Hour Course
Intrusion investigations are amongst the most difficult for digital forensic investigators because there are so many types of evidence to look for. Our Divide and Conquer DFIR Process helps investigators answer these hard questions by breaking them into smaller questions.
About Cyber Triage
Cyber Triage is built by Sleuth Kit Labs, a spinout of BasisTech. This is the same team responsible for Autopsy and The Sleuth Kit (TSK). Sleuth Kit Labs believes in making the jobs of those on the front lines easier by making software that is automated and easy to use. The company understands that it can’t decrease first responders’ responsibilities, but it can make digital forensics as easy and effective as possible.

Get Cyber Triage
Download your free 7-day evaluation with scenario data
Try Cyber Triage to see how it will make your intrusion investigations faster and more comprehensive. Fill out this form to get an installer. Use our scenario data (or your own) to get started.