Cyber Triage version 3.7.0 focuses on collecting the artifacts you care about, building a reusable artifact memory, and helping users use the MITRE ATT&CK framework.
Notable features in this release:
- Extensible File Collection: Users can configure rules of files to collect based on full paths, partial paths, or file patterns. Those rules are used by the collection tool to make a copy if they exist. They can be seen in the “Collection Details” part of the application.
- Automatically Score Other Instances of an Item: When you score an item as bad or suspicious, Cyber Triage will automatically mark other instances in the same incident. It will also look at past data when ingesting new hosts to ensure items previously marked as bad continue to be scored as bad.
- MITRE ATT&CK framework: Items scored as bad or suspicious will have a MITRE ATT&CK categorization with the analysis result. A link to the MITRE page is provided, and the names are shown in the HTML report.
Get the latest evaluation version of Cyber Triage. The full set of changes can be found here.
Extensible File Collection
What Is It?
Cyber Triage’s Collection Tool can now be customized, allowing you to specify what files to collect. The Collection Tool has always collected hundreds of files based on hard coded rules and data it parses from registry hives and other databases.
Now, you can ensure that your collection delivers even more value by extending those rules. The custom rules can be a fully qualified file path, a folder name, or just a file name. Any file that meets the patterns will be included in the collection and is available for later review.
This is the first step towards Cyber Triage having an IOC-scanner like functionality. Future releases will have the option to flag a file if it matches a rule in addition to collecting it.
Example Use Cases
This has been a long-time request and typical use cases include:
- Log files for certain applications
- Collection of files that are part of recent attack TTPs
- IOCs of an ongoing incident
How To Use It
To use this new feature, you will need to create File Sets from the Options panel.
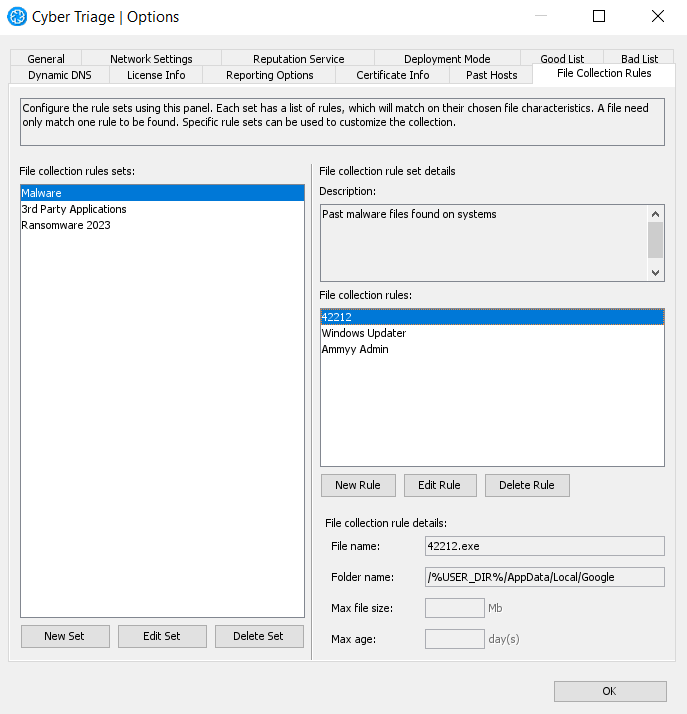
Each set contains one or more rules. A rule can contain:
- A file name (including wild cards)
- A parent folder path (including wild cards)
- Maximum size
- Maximum age
For example, you could make rules for:
- A specific file: /Program Data/Google/abc.exe
- An entire folder: /Program Data/g00gle
- All instances of a name: **/abc.exe
You can get a more detailed list of instructions from the user manual.
To see the results, you can go to the Collection Details panel and see the list of files collected. It will show you if files were found with the match or not.
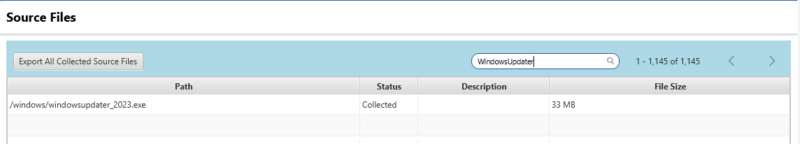
Automatically Score Other Instances of an Item
What Is It?
When you score an item as bad or suspicious, Cyber Triage will now automatically score other instances of that item. For example, if you score a process on one host as bad, it will also score other instances of that process on other hosts.
This feature saves you time and reduces mistakes by ensuring you find all instances within the current incident. It also makes your team more efficient by serving as the memory of your lab and ensuring that when something is seen again, it will get flagged.
Example Use Case
During your investigation of the endpoint, you identify an Office document that was the source of a phishing attack. It was flagged by Cyber Triage as being suspicious and you confirm that it is in fact malicious. You manually change the score to Bad.
Cyber Triage will now scan other hosts in the same incident to determine if they have a file with the same hash, and any occurrence of that file in the future will automatically be scored as bad.
How To Use It
Whenever you manually score an item as bad or suspicious, a new recommendation engine panel will appear. In addition to showing you other data types that could be relevant, it will now also show you other instances of the same item.
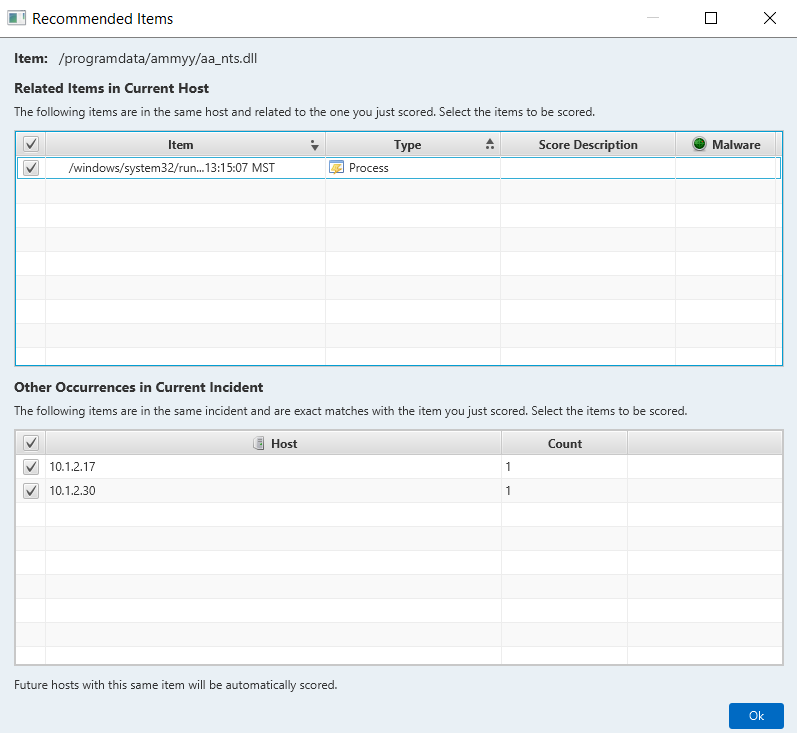
Future hosts will automatically get scored without you needing to intervene.
MITRE ATT&CK Framework
What Is It?
Cyber Triage will now categorize its findings with the MITRE ATT&CK framework, which contains a set of methods and TTPs that are used by attackers.
This feature allows you to more easily place Cyber Triage findings into ATT&CK structured reports and helps you to understand what phases of an attack are known.
Notable features are:
- Bad and suspicious items are mapped to ATT&CK categories and will allow you to read the ATT&CK page for more details.
- The HTML report shows the ATT&CK category
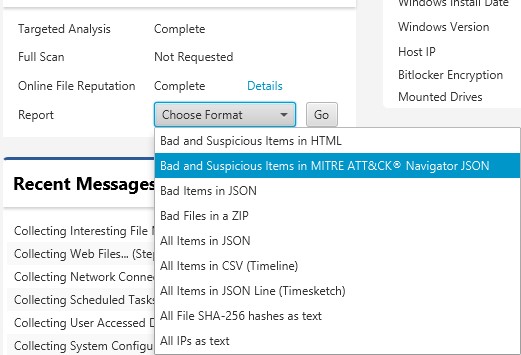
- You can export the results that can be imported into the Attack Navigator
Example Use Case
During your investigation with Cyber Triage, you find that BITS Jobs was used to download data. When Cyber Triage flags that BITS Jobs data, it will also provide a link to the corresponding ATT&CK page (T1197).
How To Use It
You can see the mapping in the bottom “Results” tab.
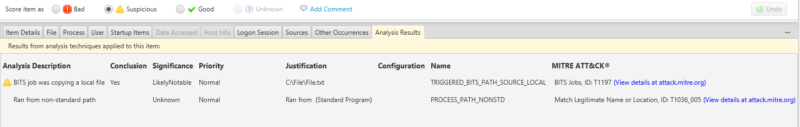
You can export the results to import into the ATT&CK Navigator by using the Report pull-down.
New Server Certificate Verification
While not a new collection or analysis feature, Cyber Triage did change how it validates the server when making TLS connections. This change is to prevent man-in-the-middle attacks.
In 3.7, you will need to specify to the Collection Tool how to verify the certificate. This change is only visible to users who launch the collection tool themselves from the command line. You will need to use ‘–cert_hash’ to either specify the server’s certificate hash or tell the collection tool not to verify.
You can read more about it in the User’s Guide.
And that’s it for 3.7.0!
We hope you enjoy this release. If there are any questions or you need assistance with any of these new features (or any questions at all) please reach out to support@cybertriage.com.
Get the latest evaluation version of Cyber Triage.
View the Cyber Triage User Guide for help.



