Ransomware is everywhere these days, and we want to help DFIR investigators take a methodical approach to responding to an attack. In this post, we’re going to talk about briefly review ransomware and the basics of the Divide and Conquer DFIR Process, then we’ll summarize the big-picture investigative questions that need to be answered for responders to know how to beat ransomware.
How to Beat Ransomware: Overview and Series Introduction
Our approach is based on our Divide and Conquer DFIR Process. We released a free 3-hour course on the Divide and Conquer DFIR Process in October. While that course was a general overview of the process, this post focuses on ransomware.
No worries though! You do not need to take the course before reading. But, you can certainly start with this post and then take the 3-hour course while waiting for the next installment—as this post is the first of a series. This series will focus on the key investigative questions and forensic artifacts that you should consider when responding to an attack, and it will be written for both responders and managers.
- If you are a responder, you should read this post and the rest of the series to help organize and frame your approach. You can also use this to help guide your supervisors if this is their first response
- If you are a manager, you should read this post to get an idea about what questions you need to be asking your responders during a ransomware response.
Note that the goal of this series of posts is not to create a comprehensive, all-in-one, checklist of “what to do in the event of ransomware” as each case is different. While it is true that many cases involve similar deployment methodologies and even the same variants of ransomware itself, each case provides its own unique analytical and data points.
In this first post, we’re going to briefly define ransomware, review the basics of the Divide and Conquer DFIR Process, and then summarize the big questions that need to be answered to successfully deal with an attack. The next posts will be deeper dives into each of big questions.
What Is Ransomware?
2020 has seen a substantial rise in ransomware attacks, and some estimates are that ransomware cases have spiked as much as 715% from 2019. Numerous companies, both large and small, have been in the headlines for getting hit with ransomware this year, so you are no doubt aware of it and may even have been affected by it through personal or business use.
There are numerous posts out there that talk about various ransomware variants, but those details are not needed at this point in our discussion, and there is no point in us duplicating them.
For the sake of this series, the core ideas of ransomware are:
- An attacker finds some way to get into a personal or corporate network
- The attacker MAY do some reconnaissance to see where the most valuable data and services are in the network; or, they may just use default settings and encrypt common file extensions
- The attacker MAY find a way to deploy ransomware to all systems or may just focus on the first computer that was exploited
- The ransomware is deployed, which may encrypt the entire computer or just select files
- The ransomware application MAY also exfiltrate the data so that they can threaten to disclose it
- The network owners realize that data or entire systems are no longer available and then start a response.
That’s where this series begins.
What Is the Divide and Conquer Process?
Before we dive into more ransomware details, let’s review the core concepts of the Divide and Conquer Process as a refresher for some and a crash course for others.
A core challenge for incident responders is knowing where to look for indicators. There are dozens of types of artifacts and thousands of instances. It can be overwhelming.
The Divide and Conquer DFIR Process is a framework to help you focus on certain types of artifacts that are relevant to the specific incident you are investigating.
Here is the main concept:
- Investigators need to start off with a set of questions that they have been tasked to answer
- Those questions are often hard to answer given all of the techniques that an attacker may have used; so, we use the classic problem-solving approach of breaking big problems into smaller solvable problems. In this case, we break big questions into smaller answerable questions
- We repeat this breakdown process until we get to questions that are simple enough to answer with a single artifact category
- We then get the data to answer the question and plan our next step accordingly.
As an example, the 3-hour course talks about the general big-picture question of “Is this computer compromised?” and breaks that first down into sub-questions of:
- Is there malicious user activity?
- Is there malware on the system?
- Are there malicious operating system changes?
These get further broken down. For example, on the topic of malware, we’ll get down to questions about startup items and network connections.
In this series, we’re going to break down questions about ransomware. The top-level questions are different from “is this computer compromised?” but we’ll end up with many of the same lower-level questions, such as looking at user activity and what they searched for.
What Are The “Big Picture” Ransomware Questions?
One of the key concepts of the Divide and Conquer approach is to always stay focused on the investigative questions that need to be answered. So, let’s start at the top with the questions executives will probably ask the security, IT, and legal teams:
- How do we get our data/services back?
- How do we get the attacker out?
- What else did the attacker do besides encrypt?
- How do we prevent this from happening again?
We can visually see this as:
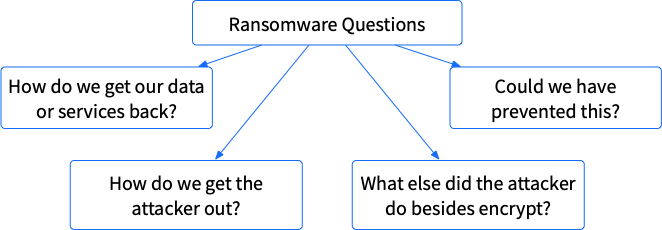
We can’t answer any of these with a single artifact category, so we’ll need to break each of these into smaller and smaller and smaller questions. The remainder of the series will be diving into each of these questions, but let’s cover the basics of each here.
How Do We Get Our Data/Services Back?
Ransomware works only if the encrypted data or service is valuable to the organization. So, the first question is often how to get it back.
Options include:
- Paying the ransom
- Restoring from backups
- Thanking the attacker for getting rid of some useless data (highly unlikely)
Just like some countries don’t negotiate with terrorists, some organizations will not even consider paying the attacker. That said, most organizations will consider it.
We’ll dive into this more in the next post, but we can break this question into sub-questions such as:
- What files were encrypted by the ransomware? You’ll need to know this to determine their value and if there are backups
- What services are not available because of ransomware? Some ransomware will encrypt the entire computer, and it can no longer provide a critical service
- Do you have backups? Many companies think they have backup solutions in place. However, few companies regularly test their backup procedures, and if the backups are online, then they could also have been encrypted
- What is the value of the impacted data and services? It’s good to have some rough idea of the value of the files and services that are no longer available to decide if the ransom is worth it
- Are you allowed to pay the ransom? This is no longer purely a business/moral/ethical decision. It also requires input from legal, as recent changes by the U.S. Treasury may make it illegal to pay ransomware operators
- What would it cost to rebuild or restore from backups? This is the cost to simply bring systems back up on your own. You’ll also need to factor in the cost to kick the attacker out in a later question.
We can visually see this as:
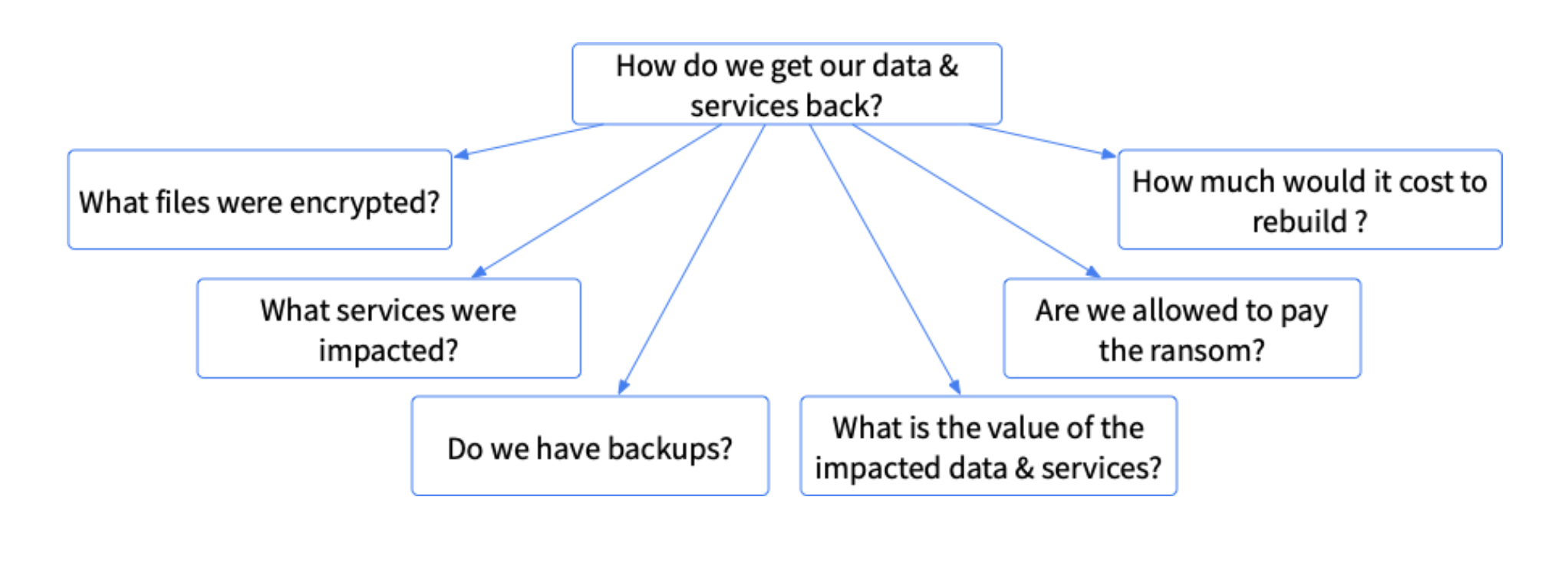
Of all of the ransomware questions, the topic of getting data back is not just about the investigation process: It will involve legal, IT, and other business factors. In this series, however, we’re focusing on the forensics questions.
How Do We Get The Attacker Out?
Regardless of whether you pay the ransom or restore from backups, getting the data back is only one part of the solution. Failing to remove any foothold that the attacker was able to create or to mitigate the initial attack vector will likely result in another incident by this attacker or another.
Therefore, the second big-picture question that management will likely want to be answered is how to get the attacker out of the network. This of course is not a question that can be easily answered by a single artifact category, so we’ll need to break it down a few layers.
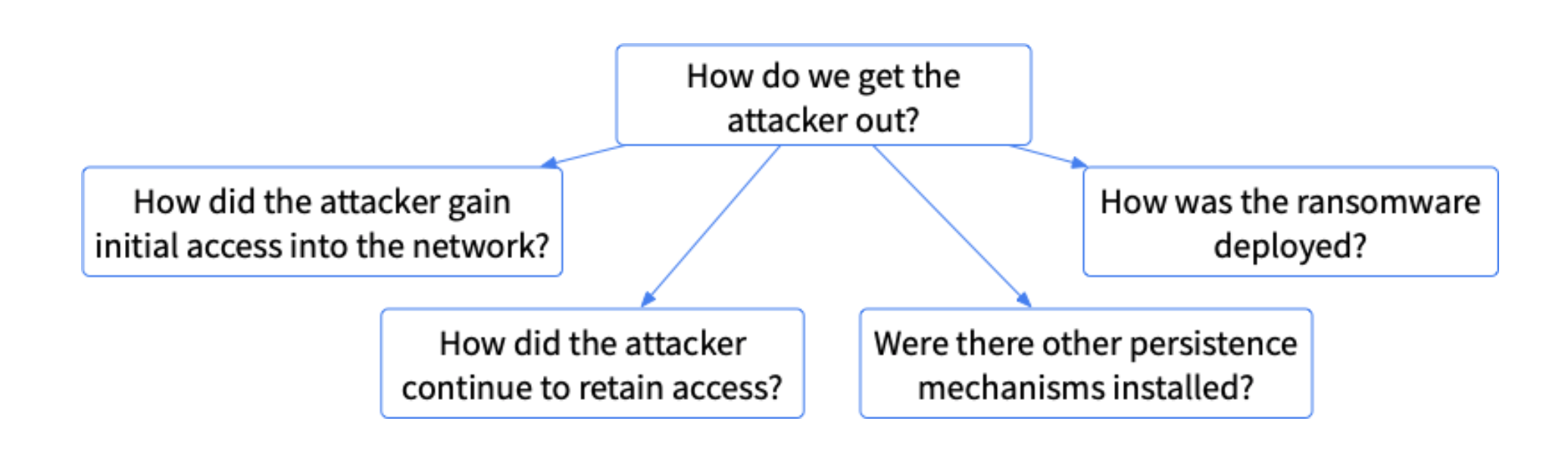
Additional breakdown questions include:
- How did the attacker gain initial access to the network? You’ll need to know how they initially got in because that could be the easiest way to get back in again. Common methods include phishing or exploiting a software (or hardware) flaw
- How did the attacker continue to retain access? Most attacks don’t happen all in one swoop. The attacker likely did some reconnaissance in the network over time. You’ll need to know how they were able to get access when they wanted it. Common methods include credential compromise, backdoors, and command and control setups
- Are there other persistence mechanisms installed? You can hopefully identify how the attacker was able to come back into the network, but you should also be looking for other backdoors and such that the attacker may have installed as a backup in case their primary method was detected. Many organizations will reset all passwords because they are not sure which accounts were compromised
- How was the ransomware deployed? It is often good to know how the attacker was able to deploy the ransomware to all of the computers to show that you understand how the attack happened and the places the attacker may have been. This ensures you know what other security issues to address. Additional security flaws may have been exploited in this process, for example, to get access to the domain controller.
We can visually see this as:
What Else Did The Attacker Do Besides Encrypt?
It’s important to determine if the attacker did anything beyond the already detected encrypted data ransomware. This is not common, but it’s always good to know the scope of what the attacker did in your network.
Knowing the answer to this could help you understand if you were a targeted attack and may face long-term consequences from this attacker—or if this was a one-time deal.
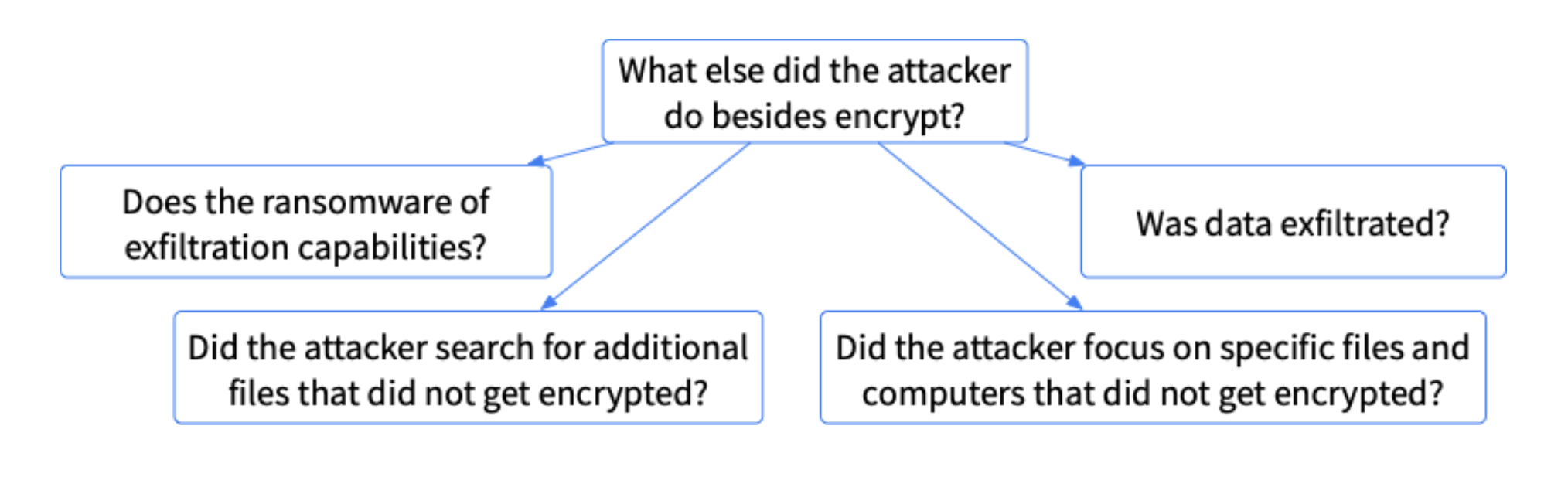
The high-level question “what else did the attacker do besides encrypt?” can be broken into sub-questions, such as:
- Does the ransomware have exfil capabilities? Some ransomware will make copies of the files so that the attacker can threaten to release the files even if the ransom is not paid
- Did the attacker search for additional files that were not encrypted? If the attacker was looking for, and found, important files (databases, HR files, etc.) that were not ultimately encrypted, that is suspicious. Those are valuable files that the company would have likely paid for
- Did the attacker focus on specific accounts and computers that were not encrypted? Some attackers will focus on key individuals and their files because those are the most likely to be paid. But, additional focus should be paid on systems that the attacker searched for and did not ultimately get encrypted
- Was data exfiltrated? As part of looking at what the attacker manually searched for and reviewed, it’s important to determine if they manually exfiltrated data by creating ZIP or RAR file and somehow uploading it to another location.
We can visually see this as:
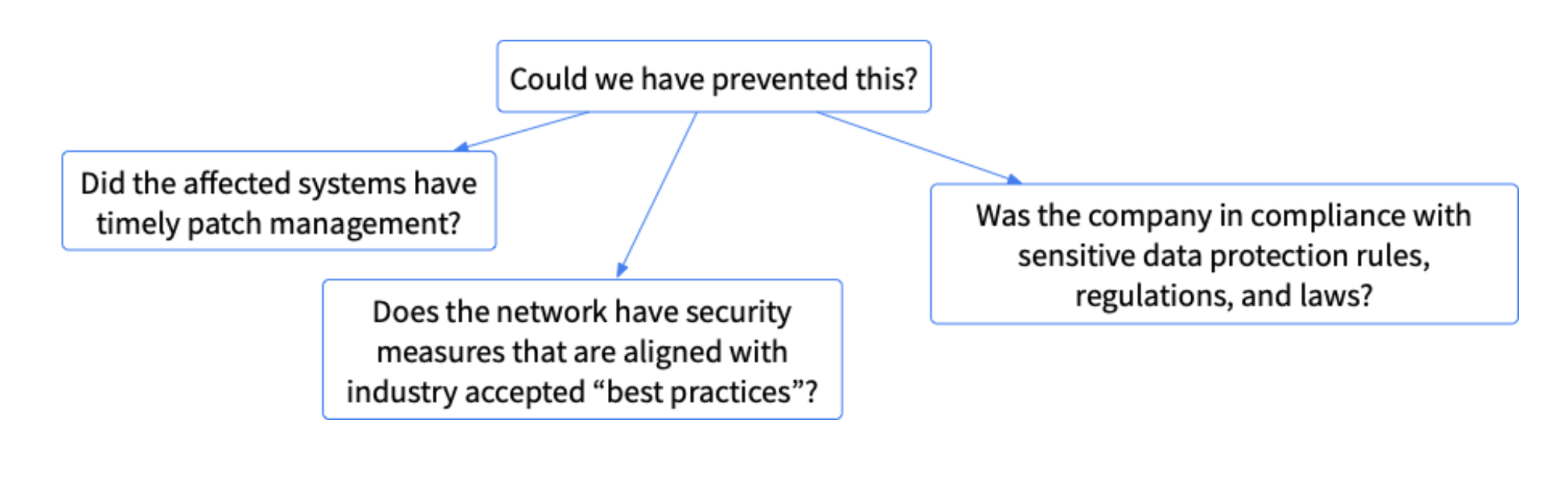
Could We Have Prevented This?
As part of answering “how do we get the attacker out?” you will hopefully uncover how the attack happened and what to fix to keep them out. The next question is if the security team could have done things differently to prevent the initial attack from succeeding. This retrospective question is important for any organization that wants to improve its security, but it may also be required if you have cybersecurity insurance.
Contrary to popular belief, simply having a cyber insurance policy is not a “blank check” redeemable in the event of an incident. Generally, the organization must demonstrate that a “reasonable effort” was made in an attempt to prevent an incident.
The prevention question can be broken down into sub-questions such as:
- Did the affected systems have timely patch management?
- Does the network have security measures that are aligned with industry-accepted “best practices”?
- Was the company in compliance with sensitive data protection rules, regulations, and laws?
We can visually see this as:
What We’ll Cover in The Next Posts on How to Beat Ransomware
In the next four posts, we’ll explain how to beat ransomware by focusing on answering each of the four questions above with host-based artifacts. In each post, we’ll break the questions down until they are small enough that we can provide an answer.
In the meantime, sign up for the 3-hour Divide and Conquer video course that covers the basic concepts of the process and provides a basic overview of Cyber Triage.
If you’d like to try Cyber Triage, the automated intrusion investigation software built on the principles of the Divide and Conquer Process, you can download it here.
If you liked this content and want to make sure you don’t miss our next article, sign up for the Cyber RespondIR email!



