Skip to content
How To DFIR Investigate with Cyber Triage and CrowdStrike Real Time Response
May 14, 2024
Start Reading
How To Investigate Endpoints with Cyber Triage and Windows Defender
April 2, 2024
Start Reading
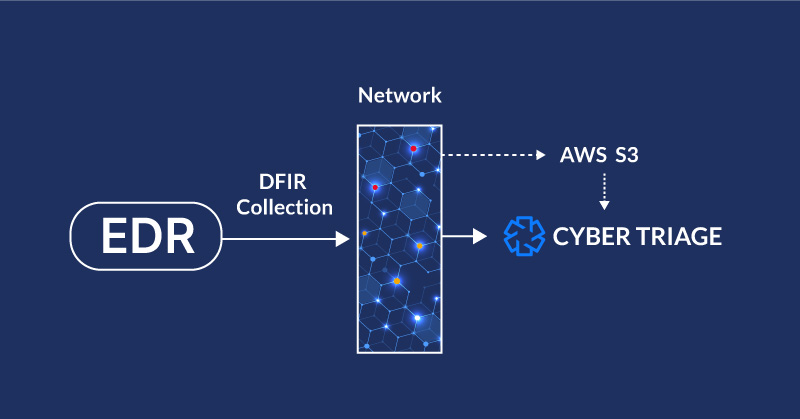
EDRs don’t collect all DFIR artifacts,
but they can help you do it
December 4, 2023
Start Reading
ReversingLabs Integration Improves Malware Scanning
January 15, 2019
Start Reading
Use of PsExec That Doesn’t Reveal Password Hashes
November 6, 2018
Start Reading
Volatility integration in Cyber Triage to Analyze Memory
May 4, 2018
Start Reading
Search For Advanced Malware In Cyber Triage Using Yara Rules
March 19, 2018
Start Reading
Integrate with Splunk for Faster Alert Triage
February 5, 2018
Start Reading
Phantom Integration Allows for Faster Responses
December 14, 2017
Start Reading