Cyber Triage 2.10 came out last month right before our workshop at OSDFCon, and we wanted to highlight a few user-requested features (recommendation engine visualization, flagging unseen files, and CSV export).
All of them help you more quickly focus on items that could be related to an incident.
You can download the latest version from here.
Recommendation Engine Visualization
Over the summer, we introduced the recommendation engine that suggests other incident items you may want to review.
For example, if you mark a process as “Bad,” then it may also point out files or network connections that are related to that process. The main idea is to make sure you are following all of the threads in your investigation.
With the latest release, we display those items in a visual form as well as tabular. Here, you can see a scheduled task was marked as suspicious, and Cyber Triage also suggests that you mark the file and execution ties:
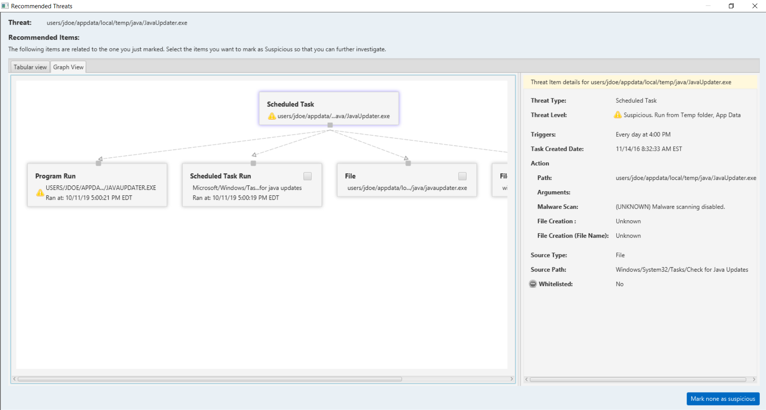
This allows you to more easily see the related items and make decisions.
Flag Files Not Seen Before
Most executables and dlls are not unique to a single computer. They are there because they came from a program that is likely used by thousands or millions of people.
The latest release of Cyber Triage can mark files as suspicious if Reversing Labs has never seen them before and you are choosing to not upload the file for analysis:
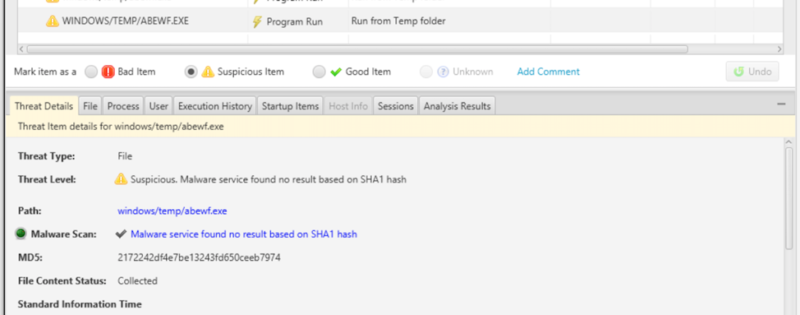
This feature enables the organizations who do not upload files to Reversing Labs to more easily identify the rare files and then decide if they are likely a unique form of malware or just an atypical software program. Some organizations will only perform a hash-based lookup (such as MD5 or SHA1) and not upload content to any provider because they are concerned about data leakage.
Export For Threat Intel
Cyber Triage now allows you to export the contents of any table (or all collected data) as a CSV text file. This includes tables such as all startup items, user accounts, and events in the timeline:
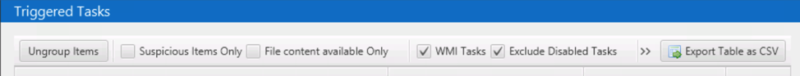
This feature will ensure that you can export the Cyber Triage data and import it into your SIEM or threat intelligence system. Other users will use this feature to more easily copy and paste data into their reports.
Try It Out
If you’d like to try these new features, then you can download an eval copy from here.



