The major theme of the Cyber Triage 2.14 release was making it easier to get artifacts from remote systems. To that end, the collection tool can now:
- Directly upload the artifacts to an S3 bucket (AWS or another similar provider)
- Encrypt and/or compress the data when saving to a local or S3.
Let’s dive into these new features in this blog.
Cyber Triage Collection Methods
First, lets review the ways that you can get data into Cyber Triage:
- Live Automatic: PsExec is used to copy the collection tool to the remote system, the collection tool runs, sends data back to Cyber Triage over port 443, and then goes away when done
- Live Manual: It’s up to you to get the collection tool running and then results are sent back over the network. Common ways to get it to run are via EDR, some other IT infrastructure, or someone manually starts it
- Live File: The collection tool is manually run on the remote system and results are saved to a USB drive or network share. They are then manually brought back into Cyber Triage
- Disk Image: You can give Cyber Triage an E01 or raw image, and it will parse it and extract artifacts
- Memory Image: Volatility is used to parse the image.
The topic of this blog focuses on enhancements to “Live File,” where someone is running the collection tool from a USB or network share.
S3 Upload
DFIR Consultants and Managed Security Service Providers (MSSP) often struggle to get data from customer networks when they don’t have direct VPN access. They often have to give a collection tool to the customer, have the customer run it, and then figure out how to get the results back to the consultant/MSSP.
Now, Cyber Triage users can have their customers automatically and easily upload the artifacts to an S3 bucket in the cloud. The collection tool can be preconfigured to know where to upload to. Let’s talk about S3 buckets and how Cyber Triage uses them.
S3 Basics
Amazon Web Services (AWS) introduced the Simple Storage Service (S3) way back in 2006. The basic concepts are that:
- An object is equivalent to a file and has a name called a key
- There is no directory hierarchy in S3. All of the files are basically in the root directory
- A bucket stores a set of objects
- A region is a location-specific data center that stores the bucket
- There are various permissions for bucket- and object-level access.
Other companies besides AWS have now built S3-compatible services. You can find a list on the Wikipedia page.
The DFIR use case would be something like:
- Responder makes an S3 bucket for Acme Corp in their S3 provider of choice, named acme
- Responder makes credentials that have write, but not read access to the acme bucket
- Acme Corp collects from an endpoint and uploads the data to a file in the acme
- Responder accesses the data from the acme
- If the credentials are compromised, the attacker cannot access data that is stored up there.
S3 in Cyber Triage
The Cyber Triage collection tool can now directly upload to an S3 bucket and implement the above process. This is in addition to the usual ways that Cyber Triage gets data when there is an on-premise server.
When you extract the collection tool, you can now specify the provider, bucket, and access tokens that the upload should go to:
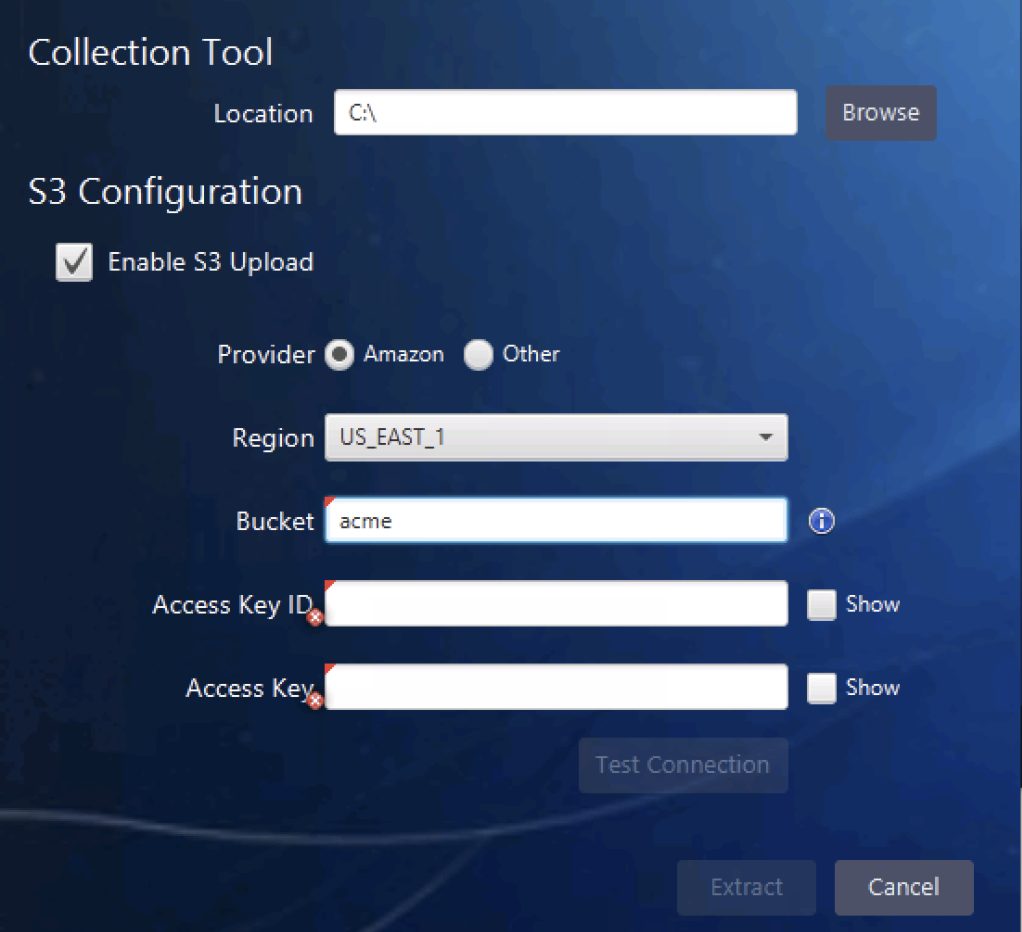
If you are using AWS, the URL is automatically determined and a list of possible regions is given. If you are using a non-AWS provider, you need to specify the URL. Some examples are given in the UI.
These results are saved to the same folder as the collection tool and its UI.
When someone launches the collection tool UI, there is now an option to upload to the configured S3 bucket:
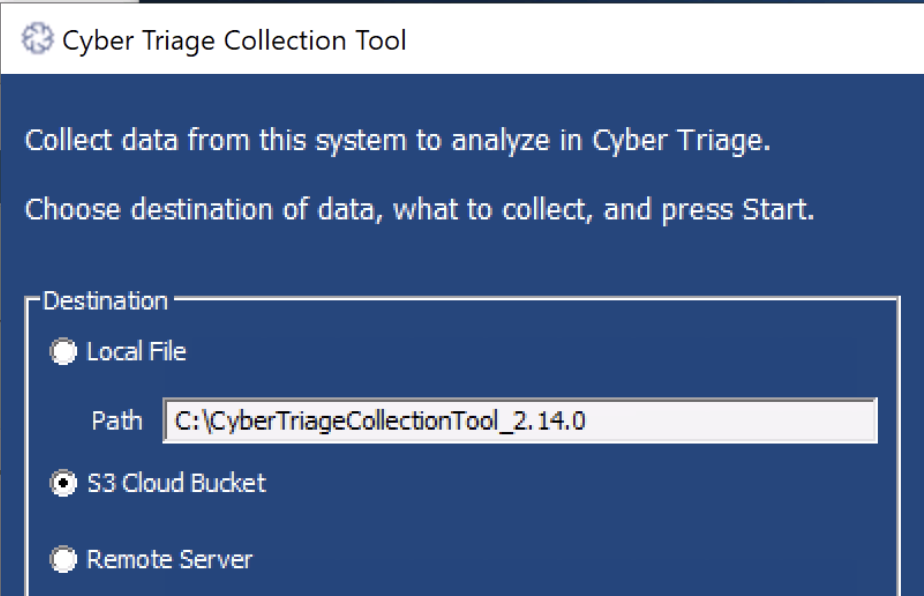
That’s it. When the collection is complete and locally saved, the resulting JSON file will be uploaded to the S3 bucket.
You can optionally encrypt the JSON file with a password before it is uploaded (see the next section).
Encrypting the Output
If you are saving the Cyber Triage Collection Tool output to a file (USB or network share), then you can now choose to encrypt it with AES. You will be prompted to provide a password when the collection happens:

The resulting file will be called cttout.json.enc.
You will also be prompted for the same password when you import it into the Cyber Triage application:
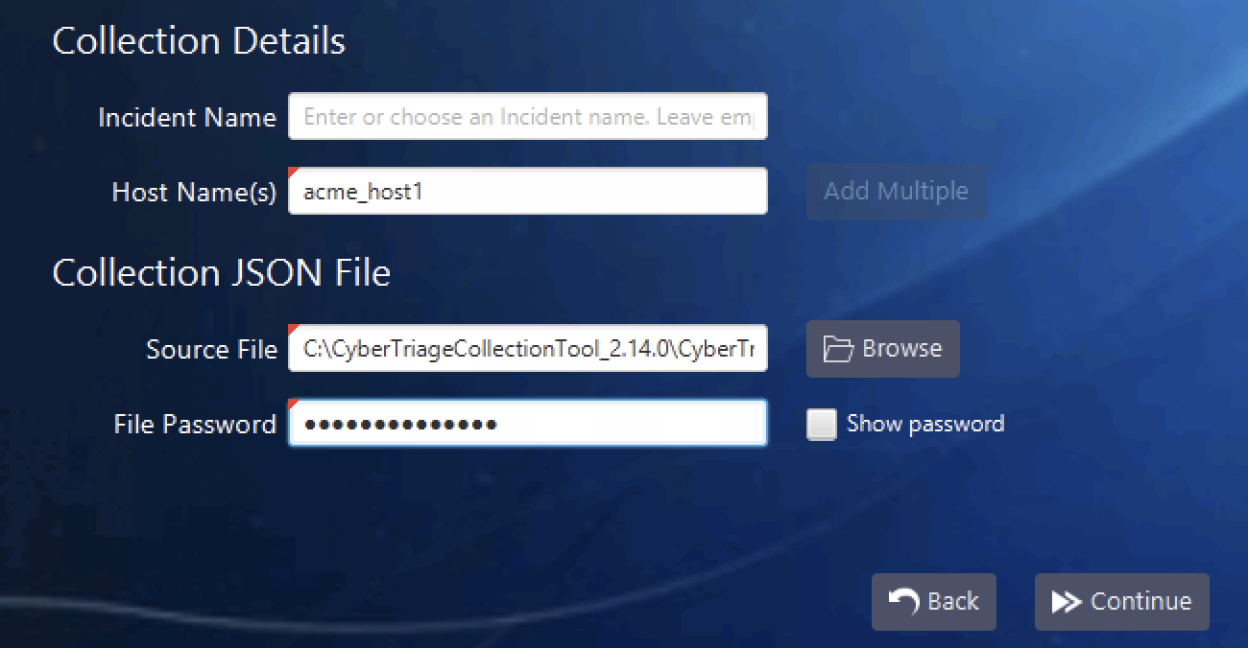
There is no recovery mechanism if the password is lost, so be careful with it!
Collection Output Compression
If you run the Cyber Triage collection tool and save the results to a file, it will now automatically be compressed using gzip. The collection tool creates a text-based JSON file and it compresses quite well.
This allows the tool to save results faster (because there is less to write to USB) and means you can copy the results around faster.
The resulting files are now called cttout.json.gz.
Version 3 Update
The engineering team is busy working on Version 3 with its new database. It’s reconnecting back with its roots and will be using the same database as Autopsy, and the team version will have a full REST API. The database is wired up in the development version, and we’re now focusing on adding in things that Autopsy doesn’t have.
Scheduled release is January 2021.
Try it Out
You can try out the latest version of Cyber Triage using this form to get a 7-day eval copy.



