Time is critical during incident response. Every minute you have an attacker roaming around your network can compromise valuable information and do irreparable damage to your systems. The latest Cyber Triage release saves your time by presenting information more efficiently, collecting more data, and performing improved analytics.
Download the latest version of Cyber Triage from here, read details below, or watch the video:
Minor Rearranging
Sometimes, small changes in your house can make your daily routines much more efficient. We’ve been taking that approach over the past few months with Cyber Triage, making many small changes in the UI to make you more efficient.
Here are some examples:
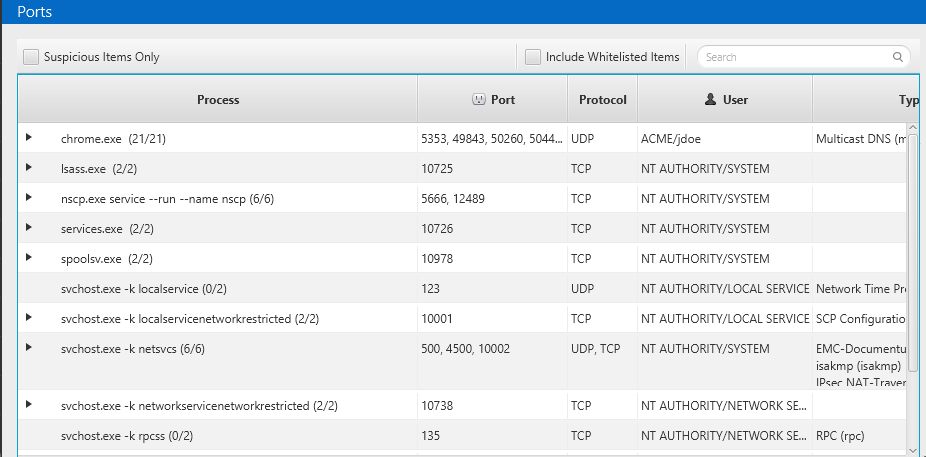
- The Open Ports table allows you to identify if an attacker has installed software that is listening for a network connection. This may give them backdoor access to your endpoint. Cyber Triage previously displayed this data organized by network port, but it is now organized by process, making it easier to quickly review. After all, many of us think more in terms of processes than network numbers.
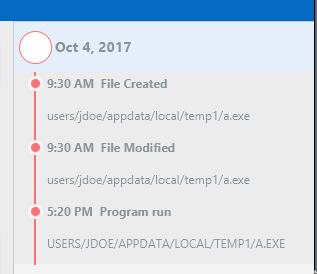
- The Timeline has been updated to give you context about when events happened in the system. In previous versions, the timeline displayed only the timestamp and a path. It now displays an event description to give you more context about what happened at that path. You can now differentiate when a file was created versus when it was executed.
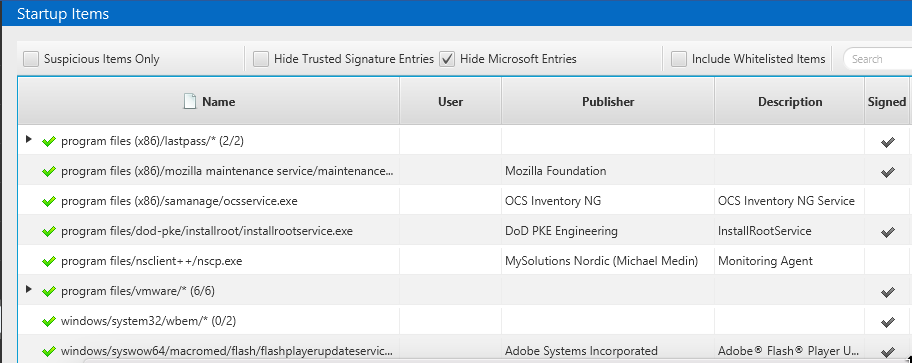
- The Startup Items table allows you to review what programs and services start each time the computer starts. Cyber Triage now displays more information in the table, such as if the program was signed and its PE headers, making it easier to identify and focus on the suspicious programs.
Keep your eye out for other changes in this release that similarly improve efficiency.
Chrome Support
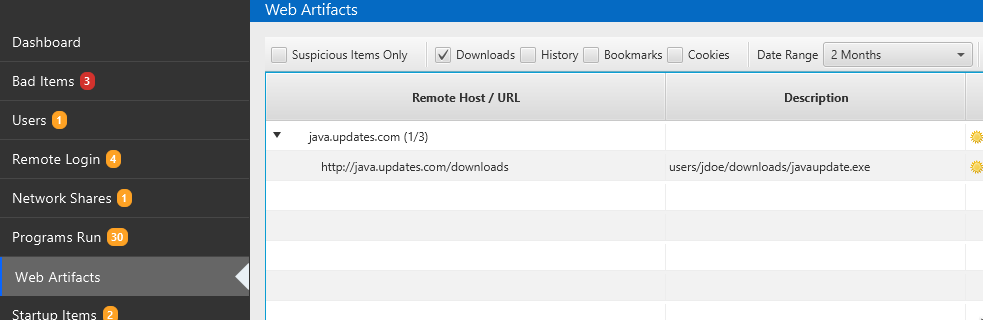
In our last release, we added support for Firefox so that responders could look for evidence of phishing attacks or insider threats. This release now adds Chrome as well. The agentless collection tool will aggregate the various databases and the results will be displayed in the Web Artifacts table, allowing you a more thorough insight into what was downloaded and searched for.
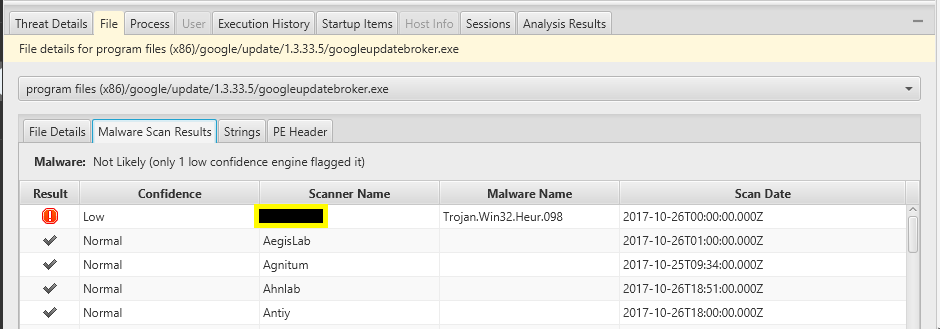
Improved Malware Scoring
In previous versions of Cyber Triage, some files would incorrectly be flagged as suspicious because of a malware scanning engine (that you’d probably never heard of before) from OPSWAT MetaDefender was flagging it incorrectly.
In this release, we changed our scoring algorithm so that you should see less of this. We have introduced a notion of weighted confidence into the scoring so that some false positive-prone engines do not waste your time.
Small Things Add Up
Cyber Triage 2.1.7 is focused on small but powerful changes to the UI, data collected, and analytics that will have a big impact on your endpoint response workflow.
Ready to try it out? Get your free evaluation copy by filling out the form on our website. The Lite (free) version of Cyber Triage includes the web browser collection and new UI layouts, but not the malware scanning.




